
Compared three types of AWS Config data that can be delivered to Amazon S3 buckets: "ConfigHistory," "ConfigSnapshot," and "Config API call logs using AWS CloudTrail"
This page has been translated by machine translation. View original
Introduction
This is Onoyandayo.
Everyone, have you ever wanted to deliver AWS Config (hereafter, Config) data to an Amazon S3 (hereafter, S3) bucket? I have.
When I vaguely say "Config data," I sometimes call it "Config logs" in other contexts, and it can be confusing which Config data I'm referring to. I myself had a vague understanding of these data types and often mixed them up, so in this article, I'd like to outline three types of data and summarize their differences.
3 Types of Config Data That Can Be Delivered to S3 Buckets
There are three types of Config data that can be delivered to S3 buckets:
- ConfigHistory
- ConfigSnapshot
- AWS CloudTrail (hereafter, CloudTrail) logs of Config API calls
While there are technically other types as well, we'll focus on these for now.
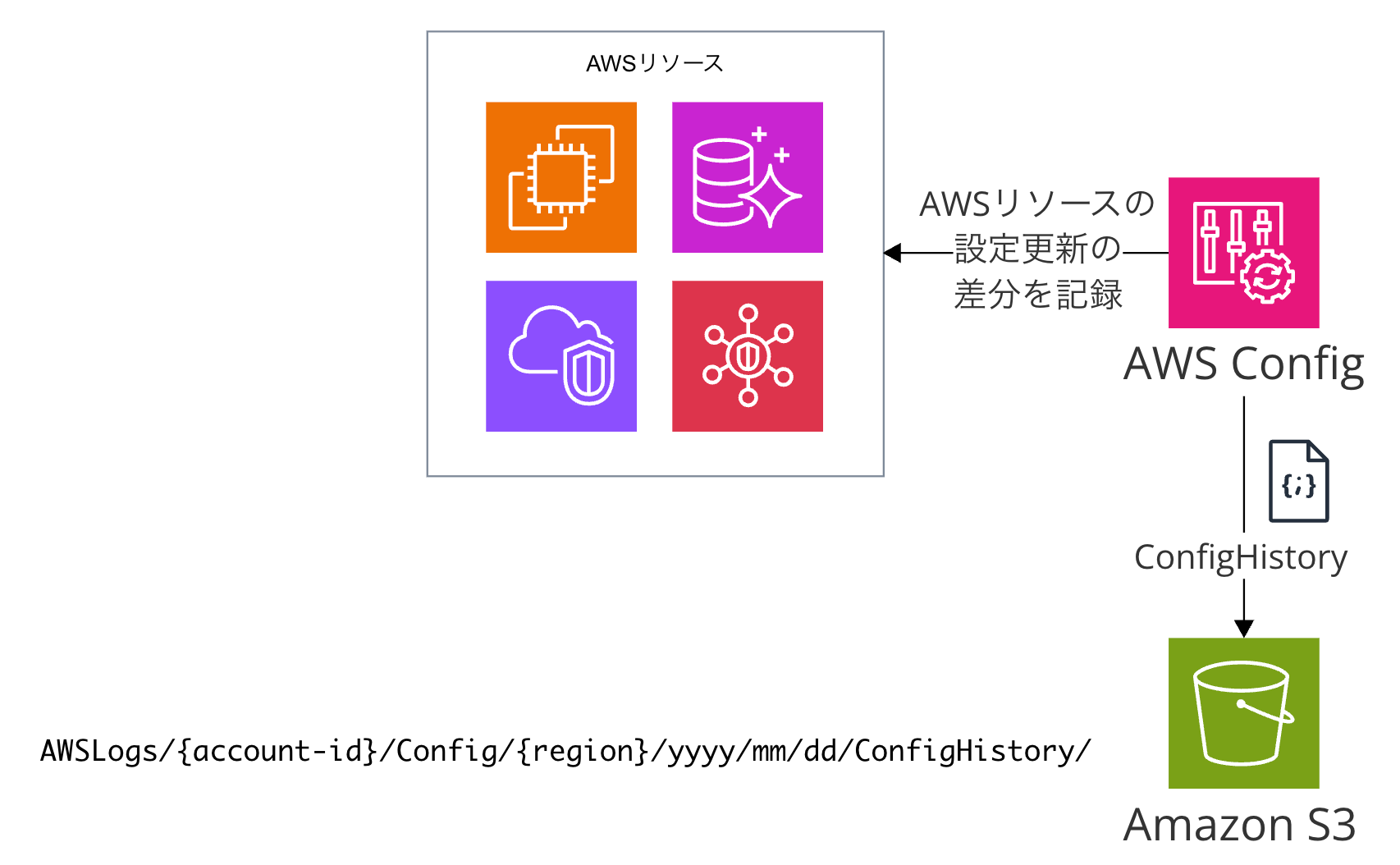
ConfigHistory
ConfigHistory is a record of AWS resource configuration changes and the differences before and after those changes, generated by the Config service. In the Japanese AWS documentation, it's translated as "設定履歴" (configuration history).
When storing in S3, the data flow is Config → S3 bucket. In the Config bucket, it's recorded directly under the path AWSLogs/{account-id}/Config/{region}/yyyy/mm/dd/ConfigHistory/.
For example, it's written in JSON format like this:
ConfigHistory Example
{
"fileVersion": "1.0",
"configurationItems": [
{
"relatedEvents": [],
"relationships": [
{
"resourceId": "SecurityHubAccepter-LambdaFunction-TznYtfenhJP0",
"resourceType": "AWS::Lambda::Function",
"name": "Is associated with "
}
],
"configuration": {
"complianceType": "NON_COMPLIANT",
"targetResourceId": "SecurityHubAccepter-LambdaFunction-TznYtfenhJP0",
"targetResourceType": "AWS::Lambda::Function",
"configRuleList": [
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-9chg6a",
"configRuleId": "config-rule-9chg6a",
"configRuleName": "securityhub-lambda-function-settings-check-dffd84a5",
"complianceType": "NON_COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-jjgsho",
"configRuleId": "config-rule-jjgsho",
"configRuleName": "securityhub-lambda-function-public-access-prohibited-dd612fa0",
"complianceType": "COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-qqi2mk",
"configRuleId": "config-rule-qqi2mk",
"configRuleName": "securityhub-lambda-inside-vpc-02636789",
"complianceType": "NON_COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-ahsbwu",
"configRuleId": "config-rule-ahsbwu",
"configRuleName": "securityhub-lambda-function-xray-enabled-8b95331d",
"complianceType": "NON_COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-lvotoo",
"configRuleId": "config-rule-lvotoo",
"configRuleName": "securityhub-lambda-function-settings-check-27cb7b04",
"complianceType": "NON_COMPLIANT"
}
]
},
"supplementaryConfiguration": {},
"tags": {},
"configurationItemVersion": "1.3",
"configurationItemCaptureTime": "2026-01-13T07:22:34.366Z",
"configurationStateId": 1768288954366,
"awsAccountId": "XXXXXXXXXXXX",
"configurationItemStatus": "OK",
"resourceType": "AWS::Config::ResourceCompliance",
"resourceId": "AWS::Lambda::Function/SecurityHubAccepter-LambdaFunction-TznYtfenhJP0",
"awsRegion": "ap-northeast-1",
"configurationStateMd5Hash": ""
},
{
"relatedEvents": [],
"relationships": [
{
"resourceId": "SecurityHubAccepter-LambdaFunction-TznYtfenhJP0",
"resourceType": "AWS::Lambda::Function",
"name": "Is associated with "
}
],
"configuration": {
"complianceType": "NON_COMPLIANT",
"targetResourceId": "SecurityHubAccepter-LambdaFunction-TznYtfenhJP0",
"targetResourceType": "AWS::Lambda::Function",
"configRuleList": [
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-jjgsho",
"configRuleId": "config-rule-jjgsho",
"configRuleName": "securityhub-lambda-function-public-access-prohibited-dd612fa0",
"complianceType": "COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-qqi2mk",
"configRuleId": "config-rule-qqi2mk",
"configRuleName": "securityhub-lambda-inside-vpc-02636789",
"complianceType": "NON_COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-ahsbwu",
"configRuleId": "config-rule-ahsbwu",
"configRuleName": "securityhub-lambda-function-xray-enabled-8b95331d",
"complianceType": "NON_COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-lvotoo",
"configRuleId": "config-rule-lvotoo",
"configRuleName": "securityhub-lambda-function-settings-check-27cb7b04",
"complianceType": "NON_COMPLIANT"
}
]
},
"supplementaryConfiguration": {},
"tags": {},
"configurationItemVersion": "1.3",
"configurationItemCaptureTime": "2026-01-13T11:14:11.813Z",
"configurationStateId": 1768302851813,
"awsAccountId": "XXXXXXXXXXXX",
"configurationItemStatus": "OK",
"resourceType": "AWS::Config::ResourceCompliance",
"resourceId": "AWS::Lambda::Function/SecurityHubAccepter-LambdaFunction-TznYtfenhJP0",
"awsRegion": "ap-northeast-1",
"configurationStateMd5Hash": ""
},
{
"relatedEvents": [],
"relationships": [
{
"resourceId": "notify-aws-billing",
"resourceType": "AWS::Lambda::Function",
"name": "Is associated with "
}
],
"configuration": {
"complianceType": "NON_COMPLIANT",
"targetResourceId": "notify-aws-billing",
"targetResourceType": "AWS::Lambda::Function",
"configRuleList": [
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-9chg6a",
"configRuleId": "config-rule-9chg6a",
"configRuleName": "securityhub-lambda-function-settings-check-dffd84a5",
"complianceType": "COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-jjgsho",
"configRuleId": "config-rule-jjgsho",
"configRuleName": "securityhub-lambda-function-public-access-prohibited-dd612fa0",
"complianceType": "COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-qqi2mk",
"configRuleId": "config-rule-qqi2mk",
"configRuleName": "securityhub-lambda-inside-vpc-02636789",
"complianceType": "NON_COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-ahsbwu",
"configRuleId": "config-rule-ahsbwu",
"configRuleName": "securityhub-lambda-function-xray-enabled-8b95331d",
"complianceType": "COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-lvotoo",
"configRuleId": "config-rule-lvotoo",
"configRuleName": "securityhub-lambda-function-settings-check-27cb7b04",
"complianceType": "COMPLIANT"
}
]
},
"supplementaryConfiguration": {},
"tags": {},
"configurationItemVersion": "1.3",
"configurationItemCaptureTime": "2026-01-13T07:22:31.344Z",
"configurationStateId": 1768288951344,
"awsAccountId": "XXXXXXXXXXXX",
"configurationItemStatus": "OK",
"resourceType": "AWS::Config::ResourceCompliance",
"resourceId": "AWS::Lambda::Function/notify-aws-billing",
"awsRegion": "ap-northeast-1",
"configurationStateMd5Hash": ""
}
]
}
When people talk about "enabling Config data and sending it to S3," in most cases they're referring to ConfigHistory being sent to S3.
For example, when enabling Config through the AWS console, you can select an S3 bucket. Once successfully enabled, you'll be able to send ConfigHistory to S3.
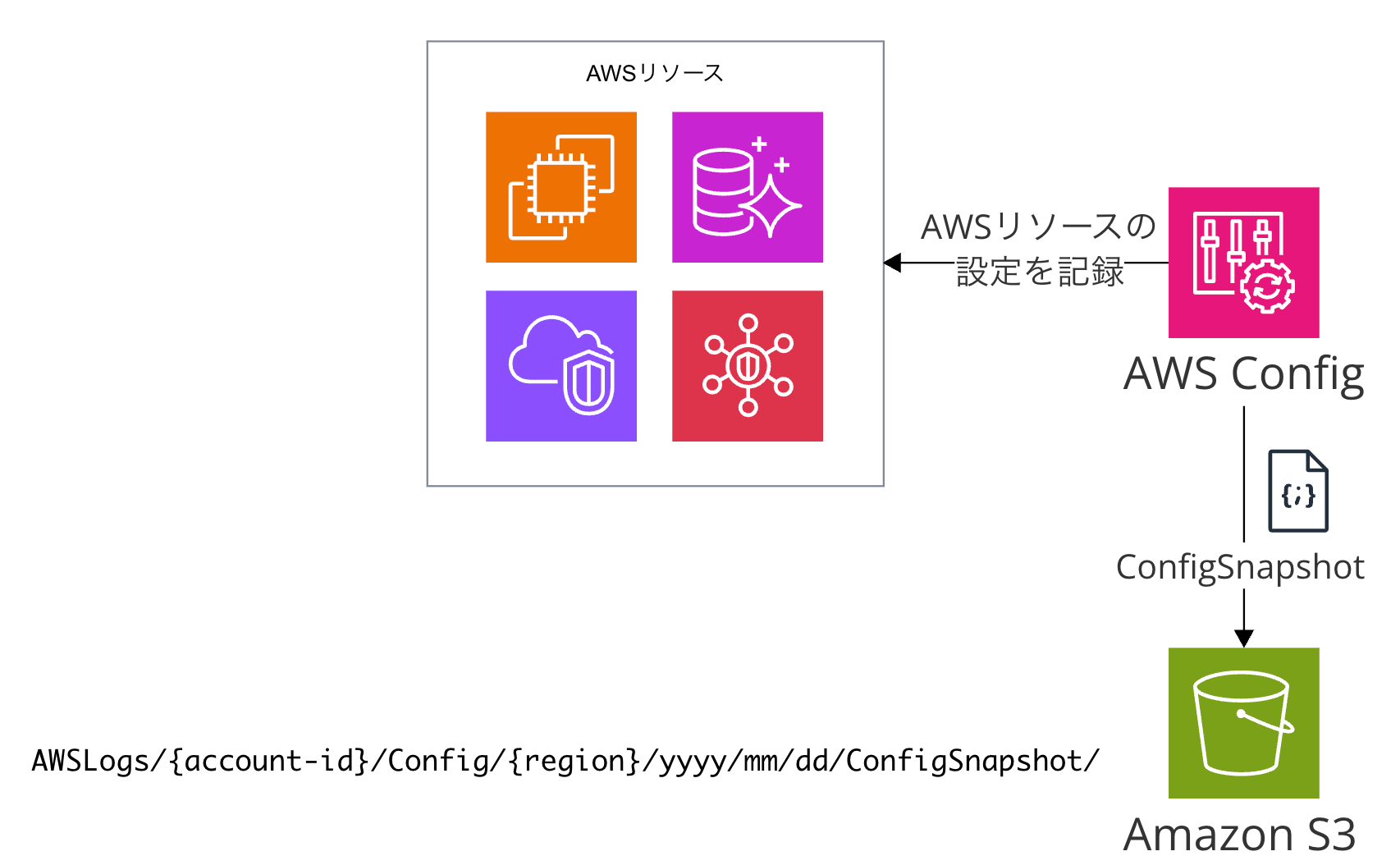
ConfigSnapshot
ConfigSnapshot is a periodic snapshot of AWS resource configurations generated by the Config service. In Japanese AWS documentation, it is translated as "設定スナップショット" (configuration snapshot).
When storing in S3, the data flow is Config → S3 bucket. In the Config bucket, it is recorded directly under the path AWSLogs/{account-id}/Config/{region}/yyyy/mm/dd/ConfigSnapshot/.
For example, it is described in JSON format like this:
ConfigSnapshot Example
{
"fileVersion": "1.0",
"requestId": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"configurationItems": [
{
"configurationItemVersion": "1.0",
"resourceId": "vol-XXXXXXXXXX",
"arn": "arn:aws:us-west-2b:XXXXXXXXXXXX:volume/vol-XXXXXXXXXX",
"accountId": "XXXXXXXXXXXX",
"configurationItemCaptureTime": "2014-03-07T23:47:08.918Z",
"configurationStateID": "YYYYYYYY-YYYY-YYYY-YYYY-YYYYYYYYYYYY",
"configurationItemStatus": "OK",
"relatedEvents": [
"AAAAAAAA-AAAA-AAAA-AAAA-AAAAAAAAAAAA",
"BBBBBBBB-BBBB-BBBB-BBBB-BBBBBBBBBBBB"
],
"availabilityZone": "us-west-2b",
"resourceType": "AWS::EC2::Volume",
"resourceCreationTime": "2014-02-27T21:43:53.885Z",
"tags": {},
"relationships": [
{
"resourceId": "i-XXXXXXXXXX",
"resourceType": "AWS::EC2::Instance",
"name": "Attached to Instance"
}
],
"configuration": {
"volumeId": "vol-XXXXXXXXXX",
"size": 1,
"snapshotId": "",
"availabilityZone": "us-west-2b",
"state": "in-use",
"createTime": "2014-02-27T21:43:53.0885+0000",
"attachments": [
{
"volumeId": "vol-XXXXXXXXXX",
"instanceId": "i-XXXXXXXXXX",
"device": "/dev/sdf",
"state": "attached",
"attachTime": "2014-03-07T23:46:28.0000+0000",
"deleteOnTermination": false
}
],
"tags": [
{
"tagName": "environment",
"tagValue": "PROD"
},
{
"tagName": "name",
"tagValue": "DataVolume1"
}
],
"volumeType": "standard"
}
},
{
"configurationItemVersion": "1.0",
"resourceId": "i-XXXXXXXXXX",
"accountId": "XXXXXXXXXXXX",
"arn": "arn:aws:ec2:us-west-2b:XXXXXXXXXXXX:instance/i-XXXXXXXXXX",
"configurationItemCaptureTime": "2014-03-07T23:47:09.523Z",
"configurationStateID": "ZZZZZZZZ-ZZZZ-ZZZZ-ZZZZ-ZZZZZZZZZZZZ",
"configurationItemStatus": "OK",
"relatedEvents": [
"AAAAAAAA-AAAA-AAAA-AAAA-AAAAAAAAAAAA",
"BBBBBBBB-BBBB-BBBB-BBBB-BBBBBBBBBBBB"
],
"availabilityZone": "us-west-2b",
"resourceType": "AWS::EC2::Instance",
"resourceCreationTime": "2014-02-26T22:56:35.000Z",
"tags": {
"Name": "integ-test-1",
"examplename": "examplevalue"
},
"relationships": [
{
"resourceId": "vol-XXXXXXXXXX",
"resourceType": "AWS::EC2::Volume",
"name": "Attached Volume"
},
{
"resourceId": "vol-YYYYYYYYYY",
"resourceType": "AWS::EC2::Volume",
"name": "Attached Volume",
"direction": "OUT"
},
{
"resourceId": "subnet-XXXXXXXXXX",
"resourceType": "AWS::EC2::SUBNET",
"name": "Is contained in Subnet",
"direction": "IN"
}
],
"configuration": {
"instanceId": "i-XXXXXXXXXX",
"imageId": "ami-XXXXXXXXXX",
"state": {
"code": 16,
"name": "running"
},
"privateDnsName": "ip-10-0-1-100.us-west-2.compute.internal",
"publicDnsName": "ec2-203-0-113-50.us-west-2.compute.amazonaws.com",
"stateTransitionReason": "",
"keyName": "example-key",
"amiLaunchIndex": 0,
"productCodes": [],
"instanceType": "t1.micro",
"launchTime": "2014-02-26T22:56:35.0000+0000",
"placement": {
"availabilityZone": "us-west-2b",
"groupName": "",
"tenancy": "default"
},
"kernelId": "aki-XXXXXXXXXX",
"monitoring": {
"state": "disabled"
},
"subnetId": "subnet-XXXXXXXXXX",
"vpcId": "vpc-XXXXXXXXXX",
"privateIpAddress": "10.0.1.100",
"publicIpAddress": "203.0.113.50",
"architecture": "x86_64",
"rootDeviceType": "ebs",
"rootDeviceName": "/dev/sda1",
"blockDeviceMappings": [
{
"deviceName": "/dev/sda1",
"ebs": {
"volumeId": "vol-YYYYYYYYYY",
"status": "attached",
"attachTime": "2014-02-26T22:56:38.0000+0000",
"deleteOnTermination": true
}
},
{
"deviceName": "/dev/sdf",
"ebs": {
"volumeId": "vol-XXXXXXXXXX",
"status": "attached",
"attachTime": "2014-03-07T23:46:28.0000+0000",
"deleteOnTermination": false
}
}
],
"virtualizationType": "paravirtual",
"clientToken": "example-token",
"tags": [
{
"key": "Name",
"value": "integ-test-1"
},
{
"key": "examplekey",
"value": "examplevalue"
}
],
"securityGroups": [
{
"groupName": "launch-wizard-2",
"groupId": "sg-XXXXXXXXXX"
}
],
"sourceDestCheck": true,
"hypervisor": "xen",
"networkInterfaces": [
{
"networkInterfaceId": "eni-XXXXXXXXXX",
"subnetId": "subnet-XXXXXXXXXX",
"vpcId": "vpc-XXXXXXXXXX",
"description": "",
"ownerId": "XXXXXXXXXXXX",
"status": "in-use",
"privateIpAddress": "10.0.1.100",
"privateDnsName": "ip-10-0-1-100.us-west-2.compute.internal",
"sourceDestCheck": true,
"groups": [
{
"groupName": "launch-wizard-2",
"groupId": "sg-XXXXXXXXXX"
}
],
"attachment": {
"attachmentId": "eni-attach-XXXXXXXXXX",
"deviceIndex": 0,
"status": "attached",
"attachTime": "2014-02-26T22:56:35.0000+0000",
"deleteOnTermination": true
},
"association": {
"publicIp": "203.0.113.50",
"publicDnsName": "ec2-203-0-113-50.us-west-2.compute.amazonaws.com",
"ipOwnerId": "amazon"
},
"privateIpAddresses": [
{
"privateIpAddress": "10.0.1.100",
"privateDnsName": "ip-10-0-1-100.us-west-2.compute.internal",
"primary": true,
"association": {
"publicIp": "203.0.113.50",
"publicDnsName": "ec2-203-0-113-50.us-west-2.compute.amazonaws.com",
"ipOwnerId": "amazon"
}
}
]
}
],
"ebsOptimized": false
}
}
]
}
While ConfigHistory is delivered to S3 almost by default, ConfigSnapshot can only be delivered to S3 when enabled via AWS CLI.
ConfigSnapshot cannot be obtained through the AWS console. You can only generate a ConfigSnapshot by calling the DeliverConfigSnapshot action or by executing an AWS CLI command. Once a ConfigSnapshot is generated, it is stored in the S3 bucket that you specified when enabling Config.
For example, you can generate a ConfigSnapshot by executing the following command. Please refer to AWS documentation for details.
$ aws configservice deliver-config-snapshot --delivery-channel-name default
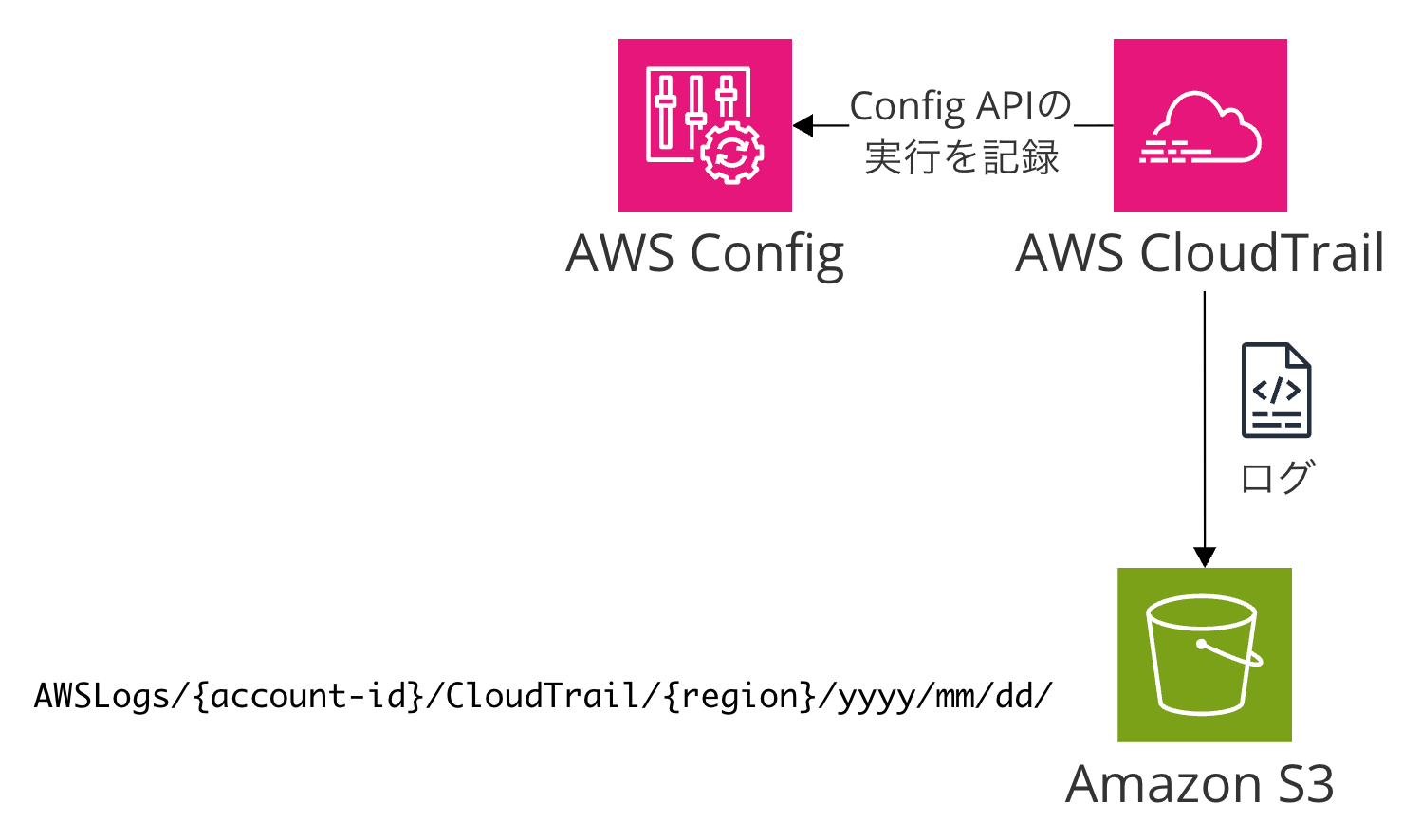
Using CloudTrail to Log Config API Calls
The two data types above are data generated by Config itself. In contrast, to record API calls to the Config service itself, you need to use AWS CloudTrail (hereinafter, CloudTrail) to record Config API call logs.
When storing in S3, the data flow is Config API call → CloudTrail → S3 bucket. In the CloudTrail bucket, it is recorded directly under the path AWSLogs/{account-id}/CloudTrail/{region}/yyyy/mm/dd/. The entity recording the logs is not Config but CloudTrail. Let's be careful not to confuse them since Config itself does not generate these logs.
The data is in JSON array format.
Example of Config API Call Logs Using CloudTrail
{
"Records": [
{
"eventVersion": "1.11",
"userIdentity": {
"type": "AWSService",
"invokedBy": "cloudtrail.amazonaws.com"
},
"eventTime": "2026-01-27T04:29:55Z",
"eventSource": "kms.amazonaws.com",
"eventName": "GenerateDataKey",
"awsRegion": "ap-northeast-1",
"sourceIPAddress": "cloudtrail.amazonaws.com",
"userAgent": "cloudtrail.amazonaws.com",
"requestParameters": {
"encryptionContext": {
"aws:cloudtrail:arn": "arn:aws:cloudtrail:ap-northeast-1:XXXXXXXXXXXX:trail/Members",
"aws:s3:arn": "arn:aws:s3:::cm-members-cloudtrail-XXXXXXXXXXXX"
},
"keySpec": "AES_256",
"keyId": "arn:aws:kms:ap-northeast-1:XXXXXXXXXXXX:key/XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX"
},
"responseElements": null,
"additionalEventData": {
"keyMaterialId": "XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX"
},
"requestID": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"eventID": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"readOnly": true,
"resources": [
{
"accountId": "XXXXXXXXXXXX",
"type": "AWS::KMS::Key",
"ARN": "arn:aws:kms:ap-northeast-1:XXXXXXXXXXXX:key/XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX"
}
],
"eventType": "AwsApiCall",
"managementEvent": true,
"recipientAccountId": "XXXXXXXXXXXX",
"sharedEventID": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"eventCategory": "Management"
},
{
"eventVersion": "1.11",
"userIdentity": {
"type": "AWSAccount",
"principalId": "XXXXXXXXXXXXXXXXXXXXX",
"accountId": "XXXXXXXXXXXX",
"invokedBy": "AWS Internal"
},
"eventTime": "2026-01-27T04:30:41Z",
"eventSource": "sts.amazonaws.com",
"eventName": "AssumeRole",
"awsRegion": "ap-northeast-1",
"sourceIPAddress": "AWS Internal",
"userAgent": "AWS Internal",
"requestParameters": {
"roleArn": "arn:aws:iam::XXXXXXXXXXXX:role/cm-REDACTED_USER",
"roleSessionName": "cm-REDACTED_USER"
},
"responseElements": {
"credentials": {
"accessKeyId": "XXXXXXXXXXXXXXXXXXXX",
"sessionToken": "REDACTED_SESSION_TOKEN",
"expiration": "Jan 27, 2026, 5:30:41 AM"
},
"assumedRoleUser": {
"assumedRoleId": "XXXXXXXXXXXXXXXXXXXXX:cm-REDACTED_USER",
"arn": "arn:aws:sts::XXXXXXXXXXXX:assumed-role/cm-REDACTED_USER/cm-REDACTED_USER"
}
},
"additionalEventData": {
"ExtendedRequestId": "XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX"
},
"requestID": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"eventID": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"readOnly": true,
"resources": [
{
"accountId": "XXXXXXXXXXXX",
"type": "AWS::IAM::Role",
"ARN": "arn:aws:iam::XXXXXXXXXXXX:role/cm-REDACTED_USER"
}
],
"eventType": "AwsApiCall",
"managementEvent": true,
"recipientAccountId": "XXXXXXXXXXXX",
"sharedEventID": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"eventCategory": "Management"
},
{
"eventVersion": "1.11",
"userIdentity": {
"type": "AssumedRole",
"principalId": "XXXXXXXXXXXXXXXXXXXXX:cm-REDACTED_USER",
"arn": "arn:aws:sts::XXXXXXXXXXXX:assumed-role/cm-REDACTED_USER/cm-REDACTED_USER",
"accountId": "XXXXXXXXXXXX",
"accessKeyId": "XXXXXXXXXXXXXXXXXXXX",
"sessionContext": {
"sessionIssuer": {
"type": "Role",
"principalId": "XXXXXXXXXXXXXXXXXXXXX",
"arn": "arn:aws:iam::XXXXXXXXXXXX:role/cm-REDACTED_USER",
"accountId": "XXXXXXXXXXXX",
"userName": "cm-REDACTED_USER"
},
"attributes": {
"creationDate": "2026-01-27T04:30:41Z",
"mfaAuthenticated": "true"
}
}
},
"eventTime": "2026-01-27T04:30:44Z",
"eventSource": "ec2.amazonaws.com",
"eventName": "DescribeRegions",
"awsRegion": "ap-northeast-1",
"sourceIPAddress": "XXX.XXX.XXX.XXX",
"userAgent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/144.0.0.0 Safari/537.36",
"requestParameters": {
"regionSet": {},
"allRegions": true
},
"responseElements": null,
"requestID": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"eventID": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"readOnly": true,
"eventType": "AwsApiCall",
"managementEvent": true,
"recipientAccountId": "XXXXXXXXXXXX",
"eventCategory": "Management",
"tlsDetails": {
"tlsVersion": "TLSv1.3",
"cipherSuite": "TLS_AES_128_GCM_SHA256",
"clientProvidedHostHeader": "ec2.ap-northeast-1.amazonaws.com"
},
"sessionCredentialFromConsole": "true"
}
]
}
Personally, when I hear "Config logs," this is what I imagine. I think different people might imagine different types of data, so it might be better to be specific with terms like "data generated by Config itself" or "Config logs recorded by CloudTrail."
Situations Where This Distinction Becomes Important
For example, when sending or replicating Config-related data to a different account in a multi-account environment, the S3 bucket you need to configure differs depending on what "Config-related data" refers to.
If you want to send or replicate data recorded by Config itself, namely ConfigHistory or ConfigSnapshot, to another account, you need to modify the settings of the Config S3 bucket. If you want to send or replicate actions/API calls executed by Config itself to another account, you need to modify the settings of the CloudTrail S3 bucket.
Be Careful with Terms Like "Config Data"
Depending on the situation, if it's unclear what "Config data" refers to, you might not know which AWS resource settings need to be changed.
It's good to revisit the overall concept of AWS services. That's all!



