
I tried CloudFront with HTTPS records support and tested Route 53 alias configuration and behavior
This page has been translated by machine translation. View original
On July 1, 2025, Amazon CloudFront announced an update to support HTTPS DNS records.
HTTPS records are DNS records that inform clients about supported protocols (HTTP/2, HTTP/3, etc.) and IP address hints before connecting to servers. This helps optimize connection negotiation and improves performance.
I had the opportunity to test this CloudFront HTTPS record support by creating an alias HTTPS record in a Route 53 hosted zone targeting CloudFront, and I'd like to share the results.
CloudFront Configuration
I created a single website (default) distribution.
For this test, I set up a CloudFront instance using a wildcard ACM certificate issued in the Virginia region.
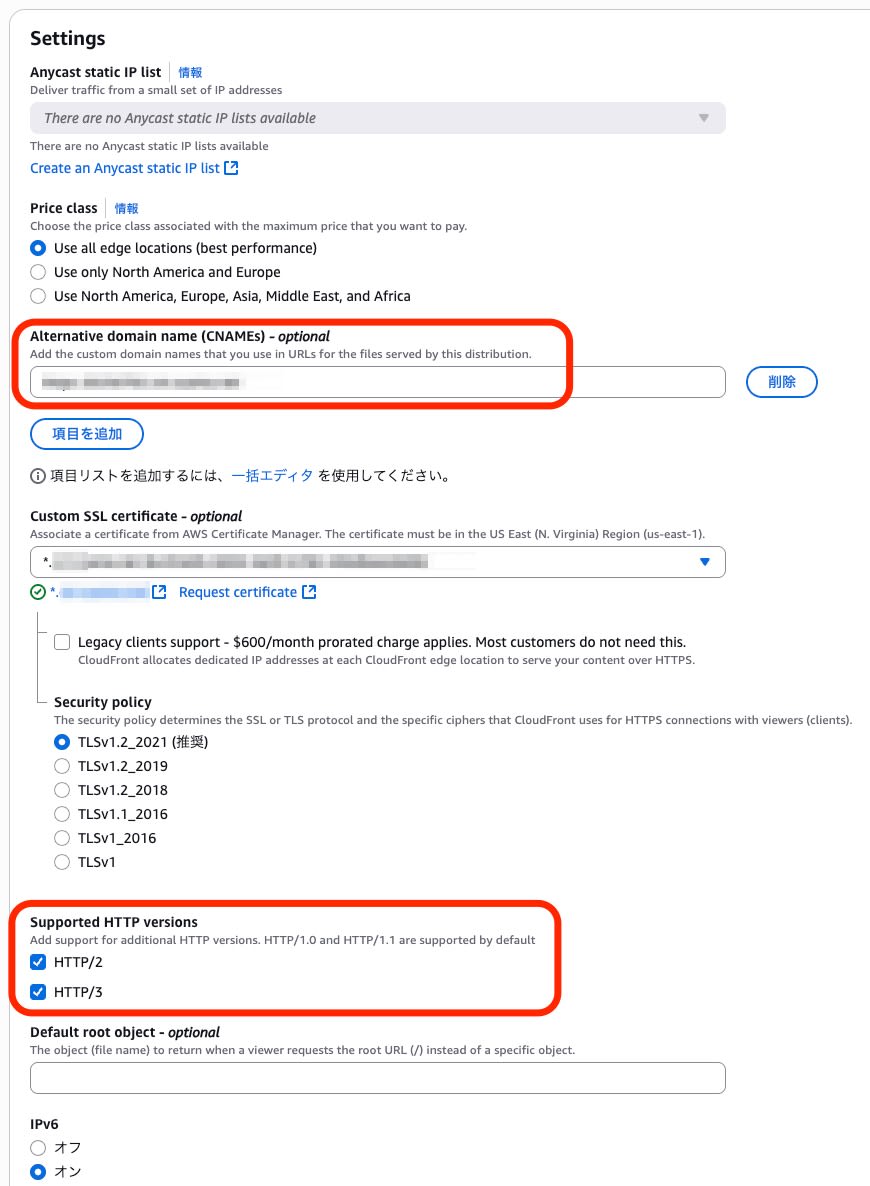
For HTTP version support, I enabled HTTP/2, HTTP/3, and IPv6.
Route53 Configuration
In the hosted zone settings, I created an HTTPS record alias targeting CloudFront.
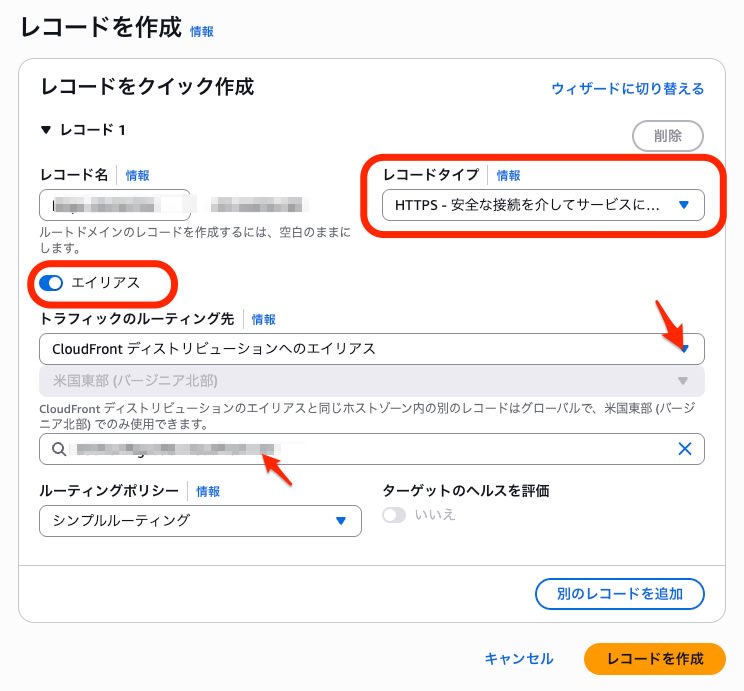
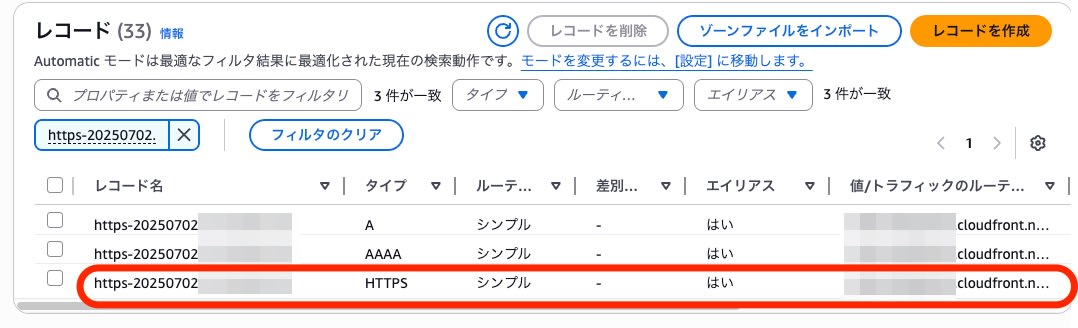
I created the following three types of alias records:
- A
- AAAA
- HTTPS
Testing
I verified the functionality of the HTTPS record alias using the drill command from the ldns-utils package on Ubuntu.
$ drill https xxx.example.com.
;; ->>HEADER<<- opcode: QUERY, rcode: NOERROR, id: 3329
;; flags: qr rd ra ; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;; xxx.example.com. IN HTTPS
;; ANSWER SECTION:
xxx.example.com. 60 IN HTTPS 1 . alpn=h2,h3
;; AUTHORITY SECTION:
;; ADDITIONAL SECTION:
;; Query time: 5 msec
;; SERVER: 127.0.0.53
;; WHEN: Wed Jul 2 04:11:17 2025
;; MSG SIZE rcvd: 70
I received the expected response from the alias record targeting CloudFront:
- SvcPriority: "1" (highest priority value in service mode)
- SvcParams (service parameters): The ALPN (Application-Layer Protocol Negotiation) correctly reflected HTTP/2 (h2) and HTTP/3 (h3) as configured in CloudFront.
I confirmed that changing HTTP support versions in CloudFront settings is reflected in the HTTPS record's ALPN:
- When HTTP/2 is unchecked (alpn=h3 only)
;; ANSWER SECTION:
xxx.example.com. 60 IN HTTPS 1 . alpn=h3
- When both HTTP/2 and HTTP/3 are unchecked
;; ANSWER SECTION:
xxx.example.com. 60 IN HTTPS 1 . alpn=http/1.1
Conclusion
By implementing HTTPS records that notify clients in advance about supported protocols, browsers that support HTTPS records can optimize connection negotiation, leading to improved performance.
While Route 53 has supported HTTPS records since October 2023, CloudFront's new support makes it possible to use HTTPS records as aliases, enabling simpler configuration without additional Route 53 charges.
For environments using Route 53 for CloudFront name resolution, I recommend adding HTTPS records as aliases in addition to A and AAAA records.


