
I tried securely connecting Amazon GameLift Servers and TiDB Cloud Dedicated using PrivateLink + VPC peering
Hello, this is Irii from the Game Solutions Department.
In this article, I will explain how to securely connect from a game server created with Amazon GameLift Servers to a TiDB Cloud Dedicated cluster.
Overview
For this verification, I used the following configuration.
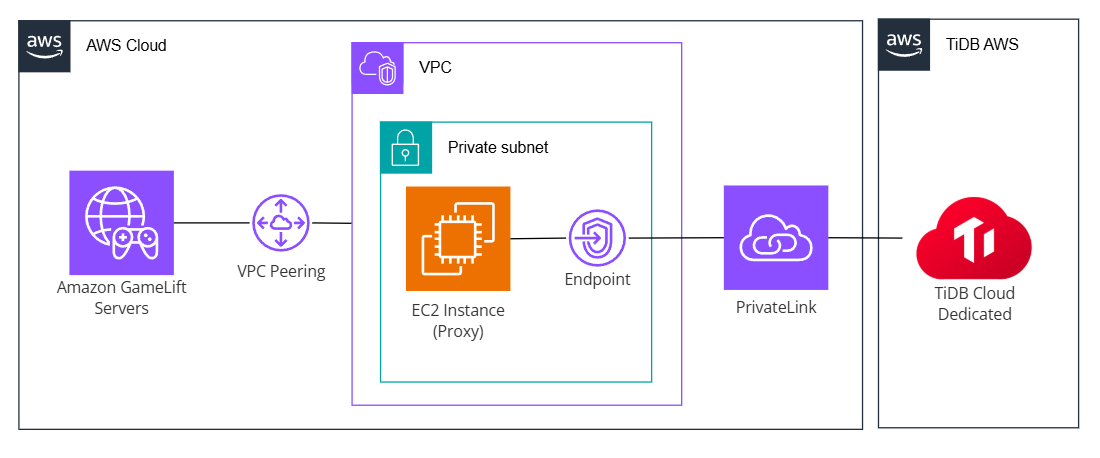
As shown in the diagram, there is an intermediary VPC between GameLift Servers and TiDB Cloud. While this results in a roundabout connection, this configuration was necessary due to GameLift Servers constraints.
GameLift Servers has a VPC peering feature, which allows you to connect the VPC where game server instances run with other VPCs. However, this feature is primarily designed for connecting with regular VPCs and does not support special configurations like VPC peering with TiDB.
Therefore, I decided to place an intermediary VPC between GameLift Servers and TiDB Cloud. This VPC connects to GameLift Servers via VPC peering and to TiDB Cloud via PrivateLink. When accessing TiDB Cloud from GameLift Servers instances, the communication goes through a proxy server on the intermediary VPC.
While this increases costs due to running the proxy server, this configuration enables private connections from GameLift to TiDB Cloud without worrying about GameLift Servers' VPC peering constraints.
Configuration Method
From here, I'll introduce the specific configuration methods.
Creating the Intermediary VPC and Subnet
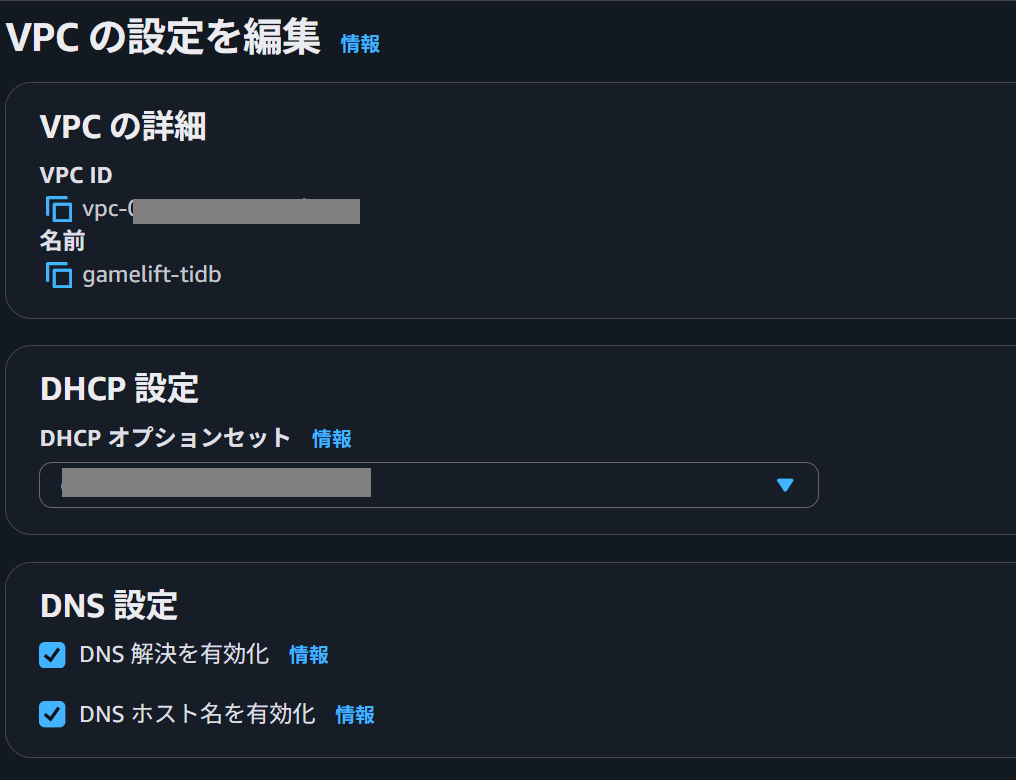
First, create a VPC and Subnet to serve as the intermediary between GameLift Servers and TiDB Cloud. The Subnet will be linked to Proxy Server instances and PrivateLink endpoints in later steps.
No special configuration is required, but to resolve names when accessing TiDB Cloud via Private Link, you need to enable DNS-related settings as shown in the image below.
 ### GameLift Servers Fleet VPC Peering Configuration
### GameLift Servers Fleet VPC Peering Configuration
For this verification, we will proceed with VPC peering configuration using managed EC2 fleet. (The specific creation method is omitted.)
The procedure differs slightly from normal VPC peering, and after creating the fleet where the target game server will launch, you need to follow these steps:
- Reserve VPC peering connection authorization
- Request VPC peering connection
First, use the create-vpc-peering-authorization command to pre-authorize the VPC to accept VPC peering connection requests from GameLift Servers.
Specify the AWS account ID using GameLift Servers with the --game-lift-aws-account-id option, and specify the transit VPC ID for the connection with the --peer-vpc-id option.
aws gamelift create-vpc-peering-authorization --game-lift-aws-account-id 11111111111 --peer-vpc-id vpc-01aaaaaaa
When executed successfully, authorization results are returned as a response.
{
"VpcPeeringAuthorization": {
"GameLiftAwsAccountId": "11111111111",
"PeerVpcAwsAccountId": "11111111111",
"PeerVpcId": "vpc-01aaaaaaa",
"CreationTime": "2025-08-12T09:31:18.099000+00:00",
"ExpirationTime": "2025-08-13T09:31:18+00:00"
}
}
Next, use the create-vpc-peering-connection command to create a peering connection to the previously authorized VPC.
Specify the AWS account ID of the target VPC with the --peer-vpc-aws-account-id option, the transit VPC ID for the connection with the --peer-vpc-id option, and the fleet ID of the GameLift Servers to connect with the --fleet-id option.
aws gamelift create-vpc-peering-connection --fleet-id fleet-99999999 --peer-vpc-aws-account-id 11111111111 --peer-vpc-id vpc-01aaaaaaa
When the connection is successful, you can get information about active peering connections with the aws gamelift describe-vpc-peering-connections command as follows:
{
"VpcPeeringConnections": [
{
"FleetId": "fleet-99999999",
"FleetArn": "arn:aws:gamelift:ap-northeast-1:11111111111:fleet/fleet-99999999",
"IpV4CidrBlock": "11.11.111.1/18",
"VpcPeeringConnectionId": "pcx-07777777777",
"Status": {
"Code": "active",
"Message": "Active"
},
"PeerVpcId": "vpc-01aaaaaaaaa",
"GameLiftVpcId": "vpc-02bbbbbbbb"
}
]
}
Reference documentation
https://docs.aws.amazon.com/ja_jp/gameliftservers/latest/developerguide/vpc-peering.html### TiDB Cloud Dedicated PrivateLink Configuration
Next, we will configure the PrivateLink between TiDB Cloud and the relay VPC we created earlier. (This assumes you have already created a Cluster)
Please note that PrivateLink is only available with Dedicated Clusters. It cannot be used with Serverless Clusters.
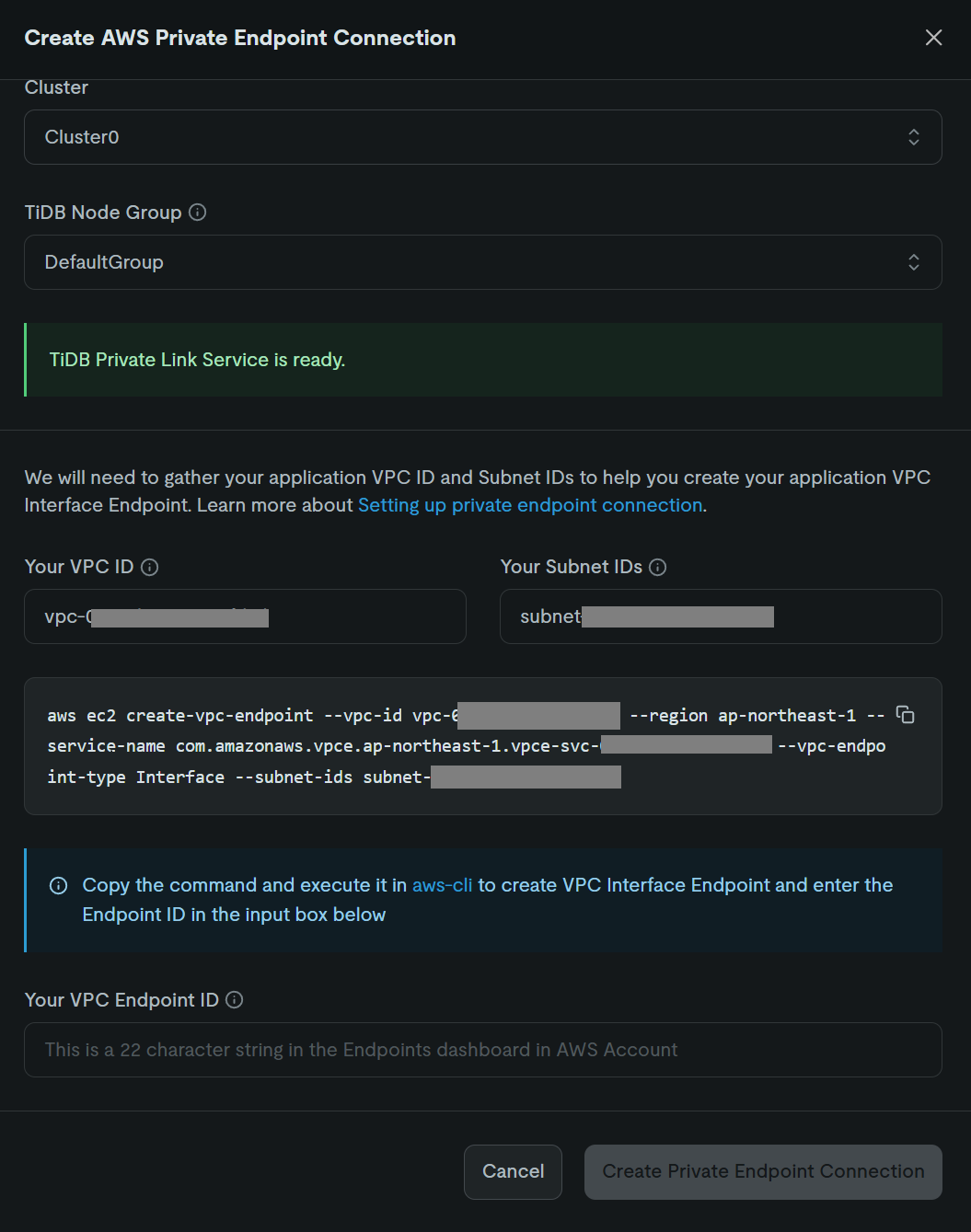
On the TiDB Cloud project management screen, click Project Settings->Network Access, select the Private Endpoint and AWS tabs, then click the Create Private Endpoint Connection button.

When the dialog appears, select the Cluster you want to connect with the VPC, confirm that "TiDB Private Link Service is ready" is displayed, and enter the relay VPC and Subnet IDs in their respective fields.
This will generate an aws cli command to create a VPC endpoint. Run this command in the AWS account of the relay VPC, enter the VPC Endpoint ID received in the response into the dialog, and click "Create Private Endpoint Connection".
Finally, a command to enable the private DNS feature for the created VPC endpoint will be displayed. Run this command as well.
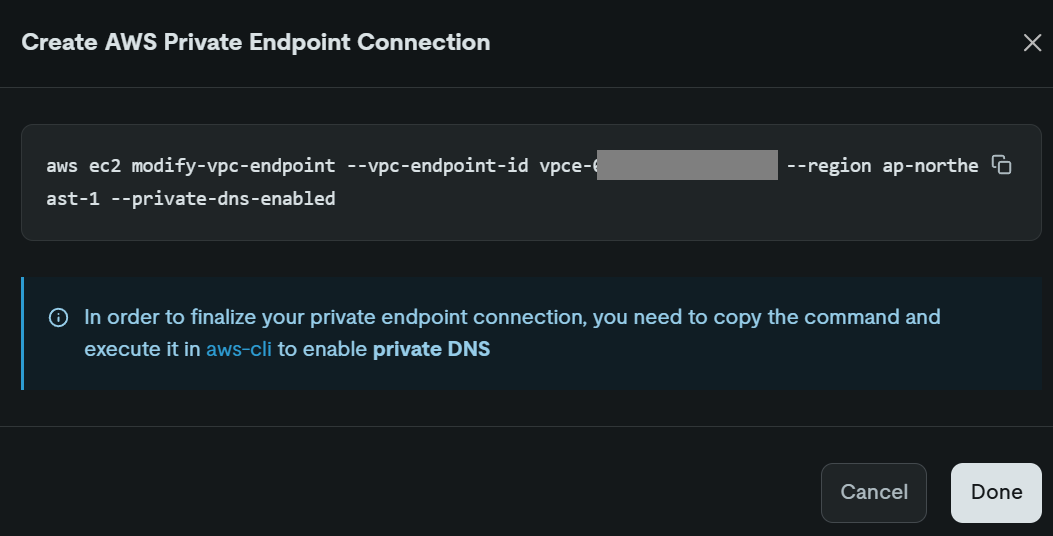
By completing these steps, the PrivateLink configuration between the relay VPC and TiDB Cloud is complete.
Reference documentation
https://docs.pingcap.com/ja/tidbcloud/set-up-private-endpoint-connections/### Proxy EC2 Instance and Security Group Configuration
Next, we will launch an EC2 instance in the relay VPC subnet to use as a Proxy Server.
When creating the instance, configure the security group as follows:
- Inbound rules
- Type: Custom TCP
- Port range: 4000 (TiDB standard port)
- Source: GameLift Servers VPC CIDR (can be confirmed from the VPC peering connection settings)
- Outbound rules
- Type: Custom TCP
- Port range: 4000
- Destination: Private IP address of the PrivateLink endpoint
This enables receiving access to port 4000 from GameLift Servers instances and sending to the PrivateLink's port 4000.
Additionally, set up SSH access to the EC2 instance.
For the OS, choose according to the proxy tool you want to use. I proceeded with Amazon Linux 2023.
SSH into the EC2 instance and run the proxy tool. In this case, I used a tool called socat.
After installing it, execute the command as shown below to forward external access on port 4000 to TiDB Host's port 4000. TiDB Host information can be obtained from the connection dialog in the TiDB Cluster settings screen.
sudo dnf install socat -y
socat TCP-LISTEN:4000,fork TCP:[TiDB Host info]:4000
Also, configure the security group associated with the PrivateLink endpoint as follows:
- Inbound rules
- Type: Custom TCP
- Port range: 4000
- Source: Private IP address of the Proxy Server EC2 instance
- Outbound rules: Not required### Connection Test from GameLift Servers Instance
Now that preparations are complete, we will test the connection from GameLift Servers instance to TiDB Cloud.
For this verification, we'll test by directly entering MySQL commands from the instance, but in actual use, access would typically be from the game server program. Note that to use MySQL commands within the instance, you need to include mysql installation commands in the game server build's installation script.
You can log in to the GameLift Servers instance by following the procedure described in the documentation below:
After logging in, access the TiDB Cloud DB server by entering the mysql command as follows:
sh-5.2$ mysql --comments -u [username] -h [Proxy Server IP] -P 4000 -D 'test' -p[password]
The request will then be forwarded from the Proxy Server to TiDB Cloud, and you will successfully log in to the DB server as shown below:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 11111
Server version: 8.0.11-TiDB-v8.5.2 TiDB Server (Apache License 2.0) Enterprise Edition, MySQL 8.0 compatible
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
Finally
By using a configuration like the one described above, you can establish a secure connection from game servers running on Amazon GameLift Servers to TiDB.
Additionally, while we used an EC2 instance as a Proxy Server for simple verification this time, using serverless options like AWS Fargate could reduce effort and costs while improving availability.

