I tried AWS CLI configuration and multi-account switching with STS AssumeRole on Claude Code
Introduction
I'm Yamato from the Customer Success department.
When you need to access multiple AWS environments, it's important to balance security and convenience.
This time, I tried setting up AWS CLI on Claude Code and using STS AssumeRole to safely switch between multiple AWS accounts.
Environment Information (IAM Policy Settings)
1. Base Account (In this example: 333333333333)
- IAM User
- Permission to AssumeRole granted by custom policy
- Example of permission policy attached to IAM user in the base account:
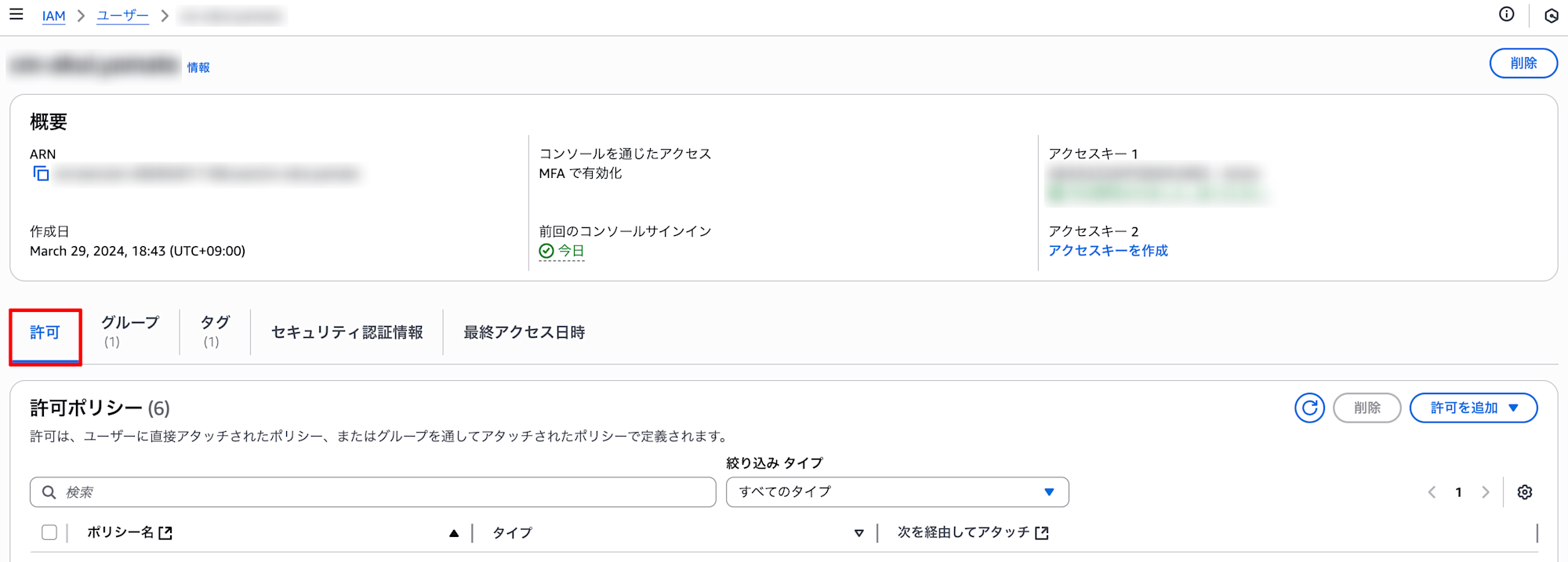
- Example of permission policy attached to IAM user in the base account:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": [
"*"
]
}
]
}
- Access key issued, MFA device configured
2. Target Accounts to Access (In this example: 111111111111, 222222222222)
- IAM roles created (In this example: RoleA, RoleReadOnly)
- Appropriate permissions attached to permission policies (e.g., S3 read access)
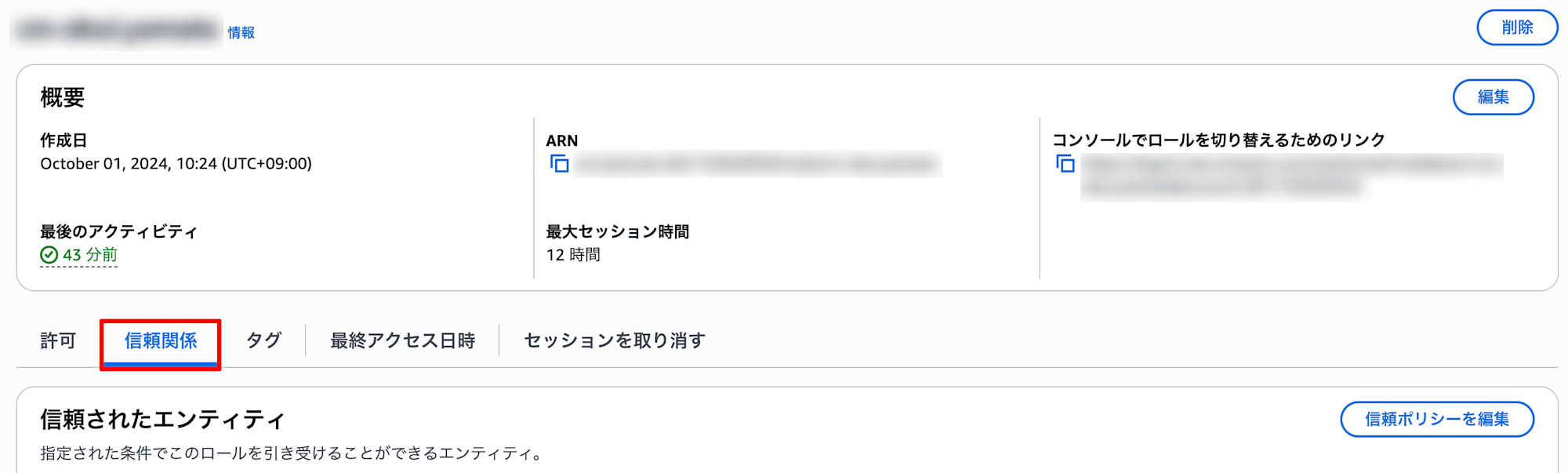
- Trust relationship policy configured (trusts users from the base account)
- Example of trust policy for IAM role in target account:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::333333333333:user/example.user"
},
"Action": "sts:AssumeRole",
"Condition": {
"Bool": {
"aws:MultiFactorAuthPresent": "true"
}
}
}
]
}
- Allows AssumeRole with MFA condition
Basic Policy
- All access to multiple environments is done through AssumeRole
- Execute with short expiration + MFA required + minimal privileges
- Restrict permissions
- Access with read-only permissions
- Escalate only when necessary, with MFA authentication required each time
- Set time-limited access using duration_seconds
- Operational considerations
- Always explicitly specify the profile
Configuration Setup
~/.aws/config Settings
[default]
region = ap-northeast-1
source_profile = base
role_arn = arn:aws:iam::111111111111:role/RoleA
mfa_serial = arn:aws:iam::333333333333:mfa/example.user
duration_seconds = 900
[profile CustomerA]
region = ap-northeast-1
source_profile = Access CustomerA
role_arn = arn:aws:iam::222222222222:role/RoleReadOnly
mfa_serial = arn:aws:iam::333333333333:mfa/example.user
duration_seconds = 900
```### ~/.aws/credentials Configuration
```ini
[base]
aws_access_key_id = "access key ID"
aws_secret_access_key = "secret access key"
[Access CustomerA]
aws_access_key_id = "access key ID"
aws_secret_access_key = "secret access key"
Actual Operation Verification on Claude Code
1. Access Confirmation with default Profile
Open a new terminal window and authenticate with default profile
aws sts get-caller-identity --profile default
Execution result:
Enter MFA code for arn:aws:iam::333333333333:mfa/example.user: ######
{
"UserId": "AROA...:botocore-session-...",
"Account": "111111111111",
"Arn": "arn:aws:sts::111111111111:assumed-role/RoleA/botocore-session-..."
}
If you authenticate AWS with MFA, you will be prompted for a one-time password (######).
2. Run Claude Code
Open a new window separate from the window created above, and launch Claude Code.
claude
"As an access test, please retrieve the list of S3 buckets in the default profile environment"
2-1. Claude Code Access "Profile: Retrieving S3 bucket list in default environment"
AWS_PROFILE=default aws s3 ls --no-cli-auto-prompt
Execution result (abbreviated example):
2025-01-02 12:22:22 example-bucket-111111111111
2025-07-03 12:33:33 example-bucket-111111111111-ap-northeast-1
2024-12-01 12:11:11 example-bucket-templates-111111111111-ap-northeast-1
...
3. Access Confirmation with CustomerA Profile
Execute in a separate terminal window where Claude Code is not running (in the terminal window used in step 1, or open a new window and execute)
aws sts get-caller-identity --profile CustomerA
Execution result:
Enter MFA code for arn:aws:iam::333333333333:mfa/example.user: ######
{
"UserId": "AROZ...:botocore-session-...",
"Account": "222222222222",
"Arn": "arn:aws:sts::222222222222:assumed-role/RoleReadOnly/botocore-session-..."
}
Similarly, a one-time password (######) was requested.### 4. Run Claude Code
Run Claude Code in the opened terminal
"Again, as an access test, please get a list of S3 buckets in the CustomerA profile environment"
4.1 Claude Code access "Profile: Getting S3 bucket list in CustomerA environment"
AWS_PROFILE=CustomerA aws s3 ls --no-cli-auto-prompt
Temporarily specifying an environment variable to run aws s3 ls using CustomerA authentication information
Execution results (partially omitted example):
2024-11-01 14:00:10 customer-a-waf-logs-app1
2024-11-02 14:00:20 customer-a-waf-logs-app2
2024-11-03 14:00:30 customer-a-analytics-logs
...
Notes for execution
- Explicitly specify the profile
- aws sts get-caller-identity --profile default
- aws sts get-caller-identity --profile CustomerA
- To check current authentication and settings, use:
- echo $AWS_PROFILE
- aws sts get-caller-identity
※ The authentication resolution priority of AWS CLI is --profile > environment variable (AWS_PROFILE). To prevent the risk of accidentally running other tasks or scripts with a fixed environment variable in a "different account", it is recommended to explicitly specify with --profile.
Troubleshooting
- AccessDenied
- Check trust policy, permission policy, and MFA conditions
- MFA error
- Check the ARN of mfa_serial, device synchronization, and terminal time synchronization
- DurationSeconds excess
- Adjust duration_seconds for each profile on the CLI side and the maximum session time on the role side
Summary
- Profile separation + AssumeRole + MFA + short sessions are effective as a basic strategy for multi-account switching.
- Claude Code worked with the same priority as AWS CLI.
- Safe multi-account operation is possible with explicit specification using
--profile.
References
About Annotation Corporation
Annotation Corporation is a Classmethod Group company specializing in operations. Our specialized support, operation, development maintenance, information systems, and back-office teams use the latest IT technology, high technical capabilities, and accumulated know-how to solve our customers' problems. We are recruiting members for various positions. If you are interested in our culture, mechanisms, and work style that realize both "Operation Excellence" and "Work like yourself, live like yourself," please visit the Annotation Corporation Recruitment Site.