I tested extended scanning of container images containing tinycolor which had an NPM supply chain attack
This page has been translated by machine translation. View original
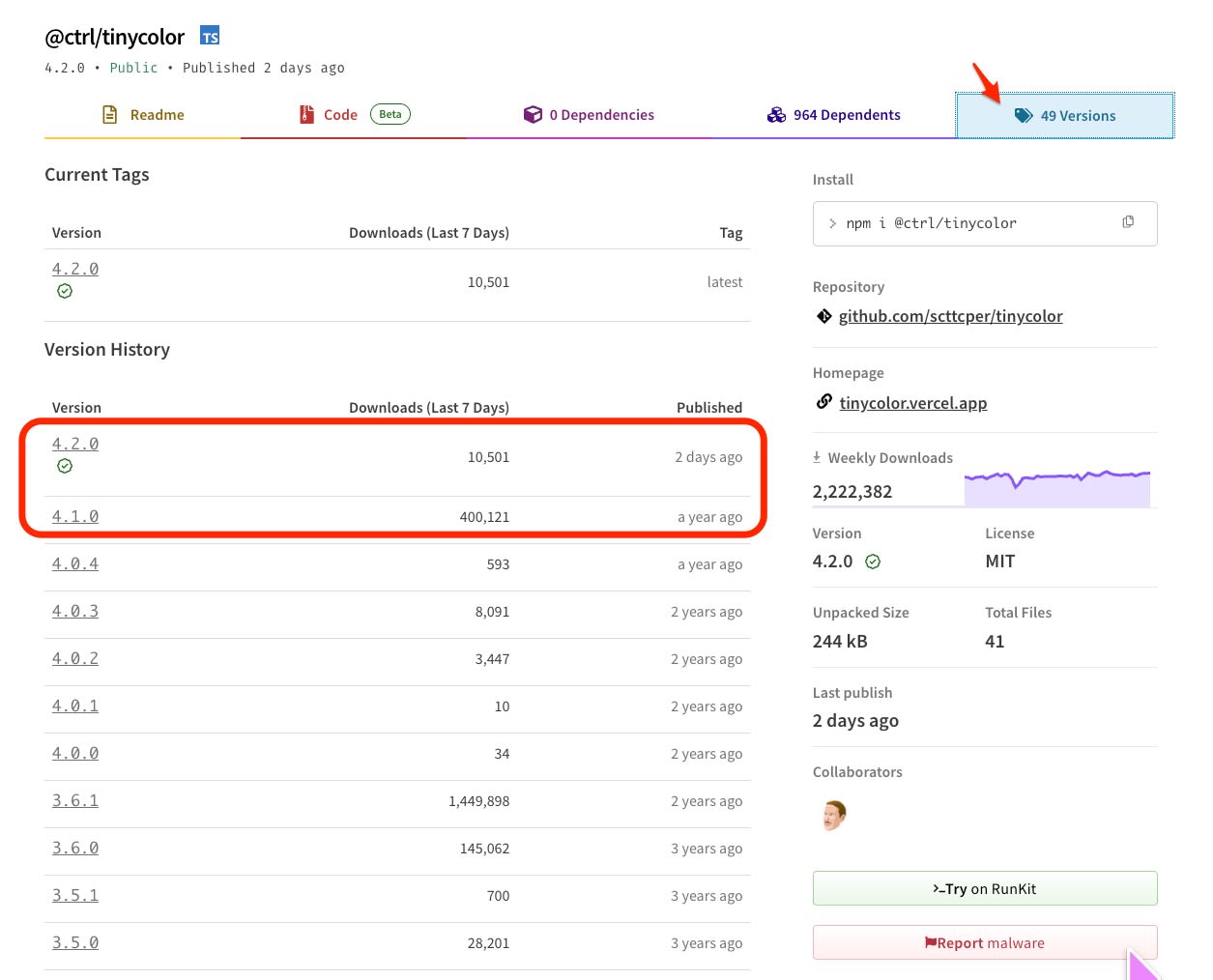
On September 15, 2025, StepSecurity's blog reported that the popular NPM package @ctrl/tinycolor, which is downloaded over 2 million times weekly, along with many other packages, fell victim to a supply chain attack.
ctrl/tinycolor and 40+ NPM Packages Compromised
The popular @ctrl/tinycolor package with over 2 million weekly downloads has been compromised alongside 40+ other NPM packages in a sophisticated supply chain attack dubbed "Shai-Hulud". The malware self-propagates across maintainer packages, harvests AWS/GCP/Azure credentials using TruffleHog, and establishes persistence through GitHub Actions backdoors - representing a major escalation in NPM ecosystem threats.
https://www.stepsecurity.io/blog/ctrl-tinycolor-and-40-npm-packages-compromised#affected-packages
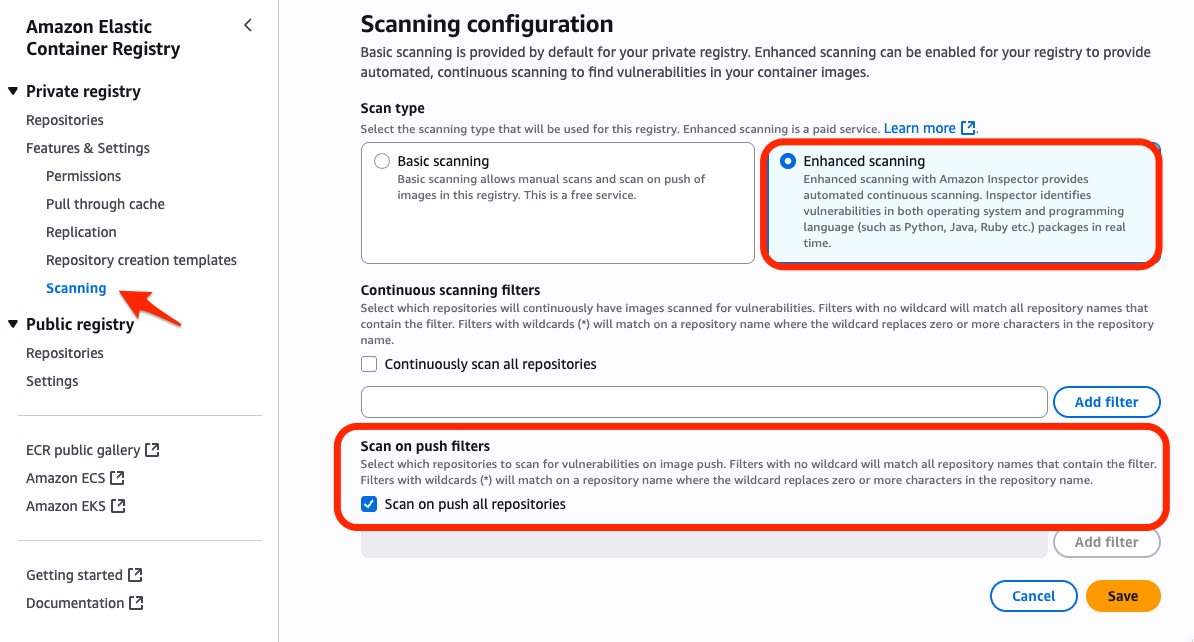
By enabling enhanced scanning in Amazon ECR (Elastic Container Registry), Amazon Inspector can detect vulnerabilities in OS and programming language packages (Python, Java, Ruby, etc.) within container images.
In this article, I pushed a container image containing @ctrl/tinycolor to ECR and verified how vulnerabilities would be detected by Amazon Inspector scanning.
Test Environment
Scan Configuration
I enabled enhanced scanning using the ECR dashboard.
I configured it to scan on push to private repositories.
Creating Test Images
The compromised versions 4.1.1 and 4.1.2 have already been removed from the repository. Currently, version 4.2.0, which has fixed the issues, is available as the latest version.
For this test, I prepared two types of images: the latest version (4.2.0) and version 4.1.0 (pre-compromise) for comparison.
package.json (example: using 4.2.0)
{
"name": "sample-app",
"version": "1.0.0",
"dependencies": {
"@ctrl/tinycolor": "4.2.0"
}
}
I prepared a simple Dockerfile that just installs the @ctrl/tinycolor package.
FROM node:alpine
WORKDIR /app
COPY package.json ./
RUN npm install
CMD ["node", "--version"]
Scan Results
4.2.0 (Latest Version)
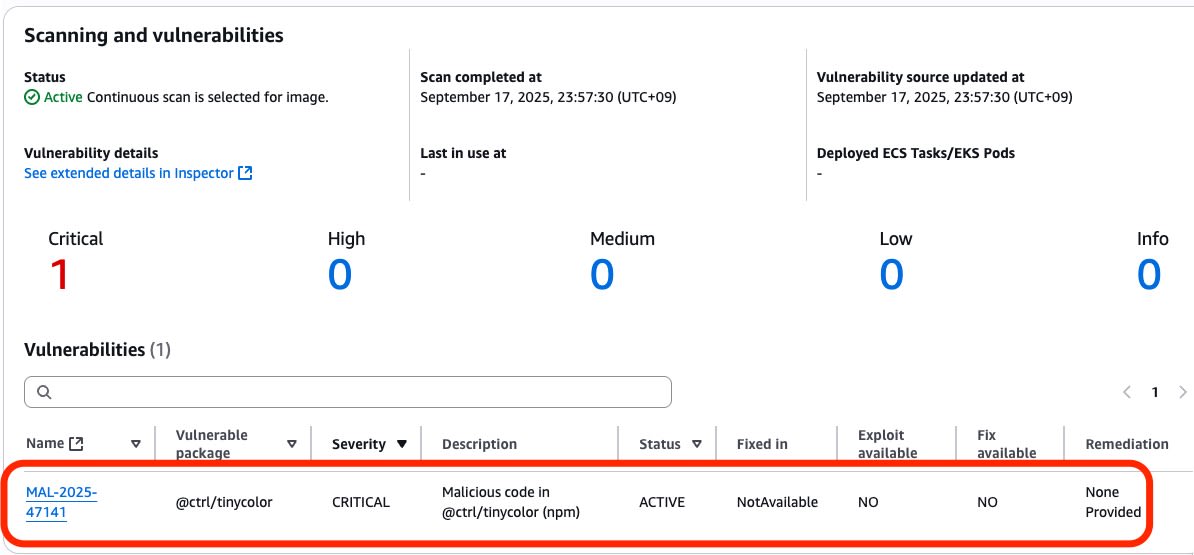
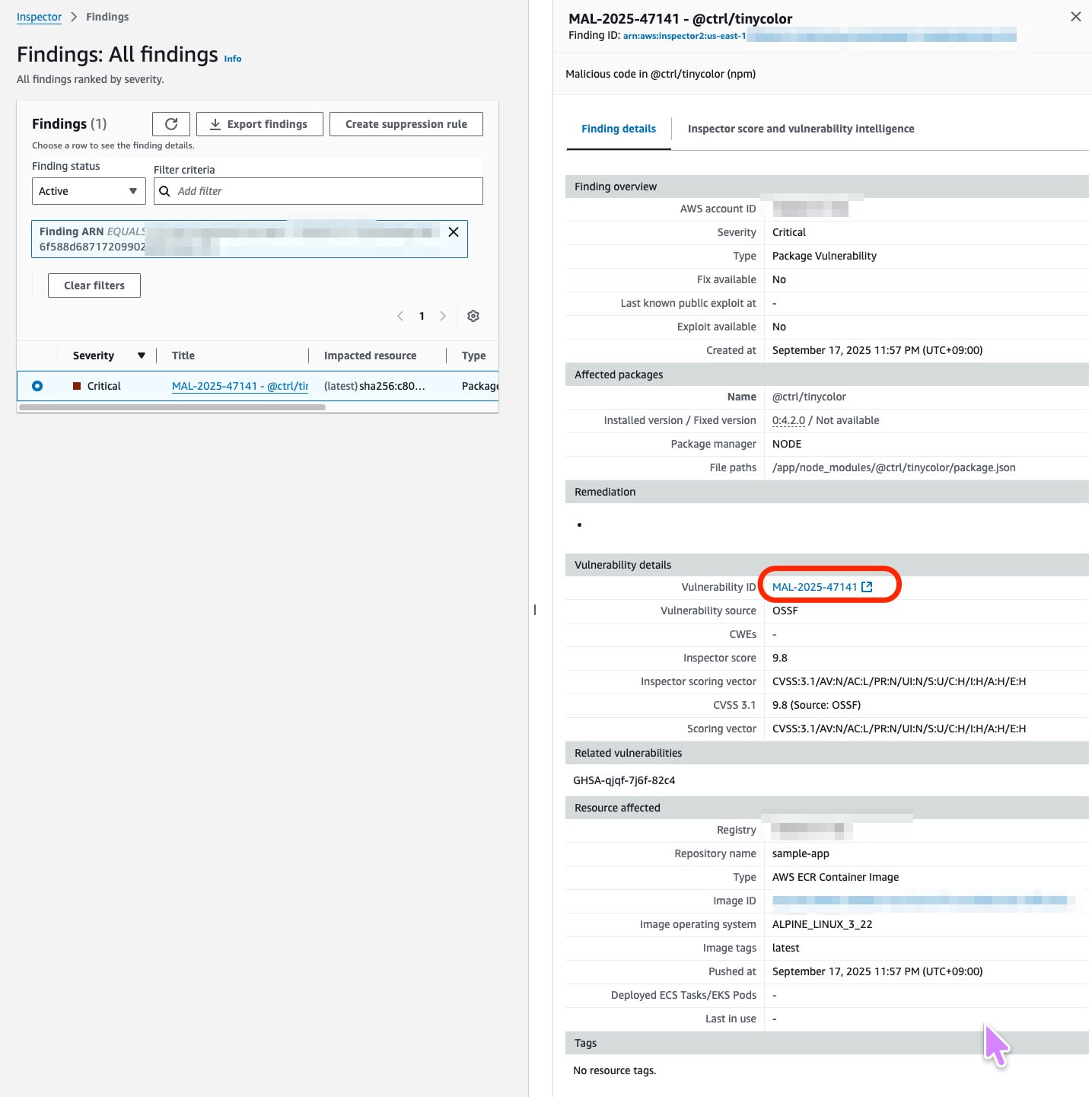
Scanning the image containing the latest version 4.2.0 detected a CRITICAL issue as follows:
- Name: MAL-2025-47141
- Vulnerable package: @ctrl/tinycolor
- Severity: CRITICAL
- Description: Malicious code in @ctrl/tinycolor (npm)
4.1.0 (Pre-compromise Version)
No vulnerabilities were detected in the image containing version 4.1.0 from before the compromise.
Conclusion
In this test, Amazon Inspector's scan resulted in a "false positive" by identifying the supposedly fixed latest version 4.2.0 as vulnerable.
The cause is likely that the vulnerability database referenced by Inspector had not yet been updated with the information that "4.2.0 is safe."
Following the Vulnerability ID MAL-2025-47141 from the Inspector report leads to the OSSF database information, which showed a last update time of 2025-09-17T06:23:36Z at the time of testing (9/18). This data probably did not yet include the fix information for 4.2.0.
Update date information for MAL-2025-47141 as of 9/18:
"modified": "2025-09-17T06:23:36Z",
"published": "2025-09-15T23:42:49Z",
Despite the false positive issue, the pre-compromise version was correctly identified as "safe," confirming the effectiveness of ECR enhanced scanning as a means to detect packages compromised by supply chain attacks.
For workloads that use numerous NPM packages, it's essential to constantly prepare for supply chain attack risks like this one. Consider enabling ECR enhanced scanning or incorporating scanning processes into your CI/CD pipeline.
Note that ECR enhanced scanning is a paid feature. When using on-push scanning in the Tokyo region, a charge of $0.11 (as of September 2025) is incurred for each image pushed. Please be mindful of costs in environments where images are pushed frequently.