
I tried subscribing to Terraform MCP Server on AWS Marketplace and setting it up with Amazon Bedrock AgentCore
Recently, Terraform MCP Server was added to AWS Marketplace.
Build secure, AI-driven workflows with Terraform and Vault MCP servers
In this article, I'll subscribe to it and set it up using Amazon Bedrock Agent Core.
Terraform MCP Server
By using Terraform MCP Server, AI can read information from the Terraform Registry and generate responses.
For more details, please check the following:
What is Amazon Bedrock Agent Core
Announced in July 2025 (preview), it's a service equipped with various features necessary to build and publish AI agents.
Let's try it
Subscribe to Terraform MCP Server on AWS Marketplace
Search for Terraform MCP Server on AWS Marketplace and select it.
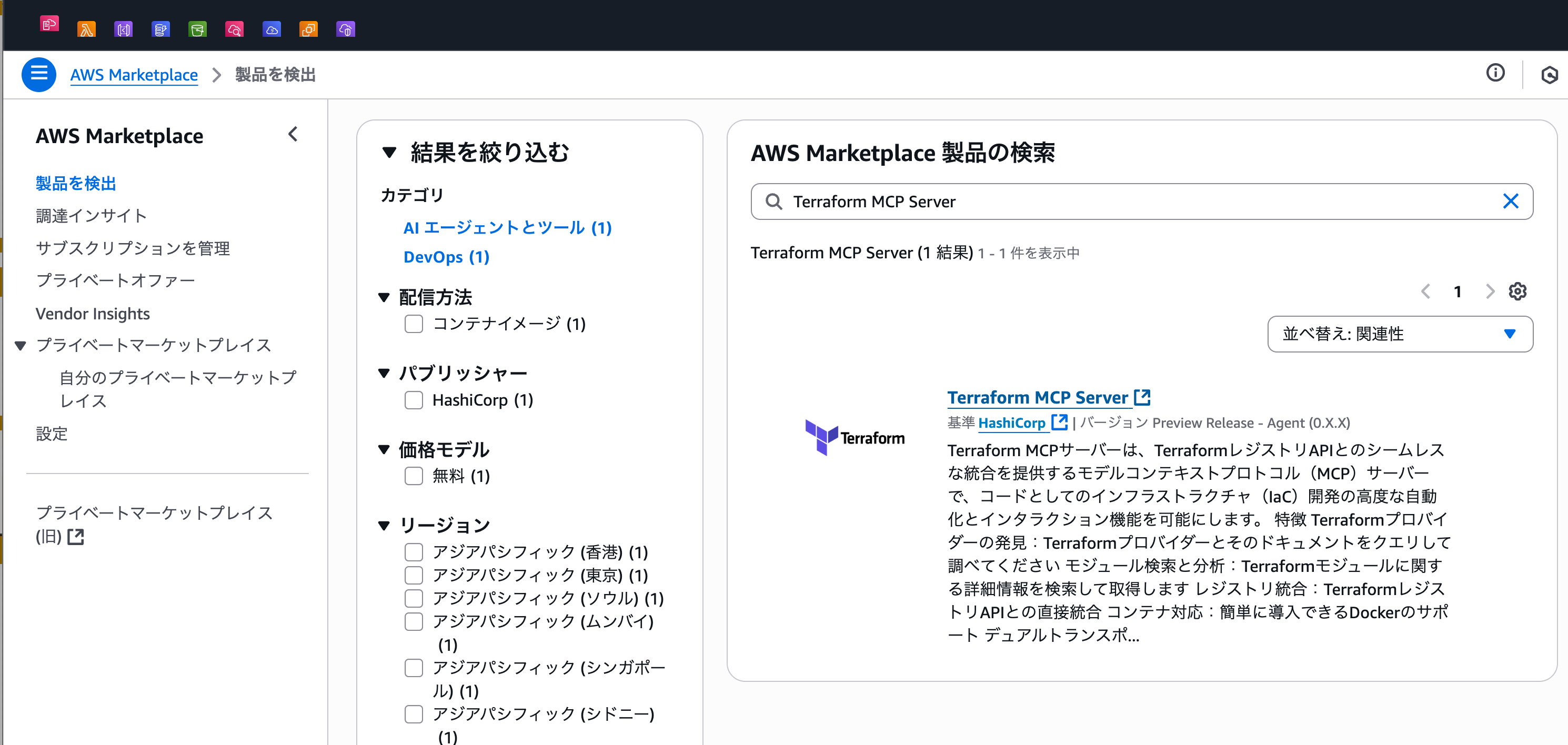
You can also access it from the following link:
AWS Marketplace: Terraform MCP Server
This product can be subscribed to for free.
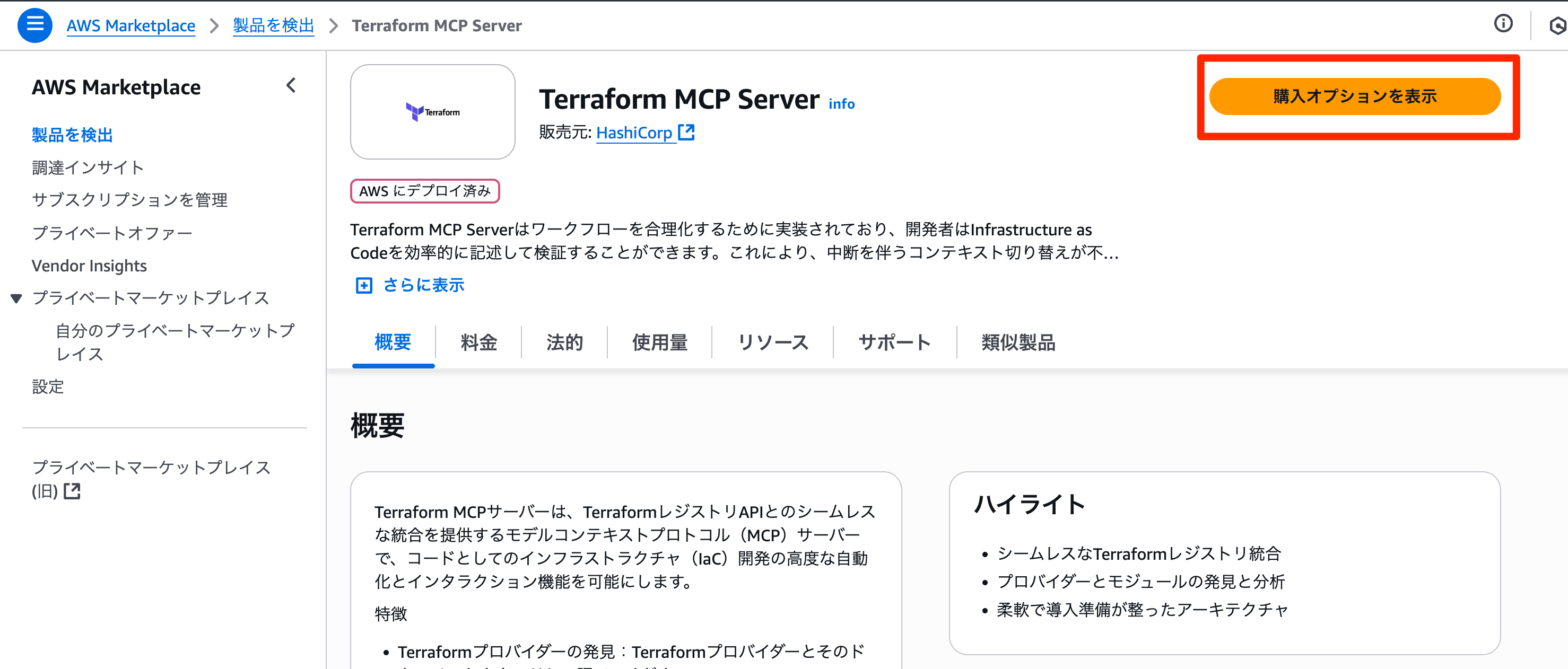
Proceed to the subscription screen from View purchase options and subscribe.
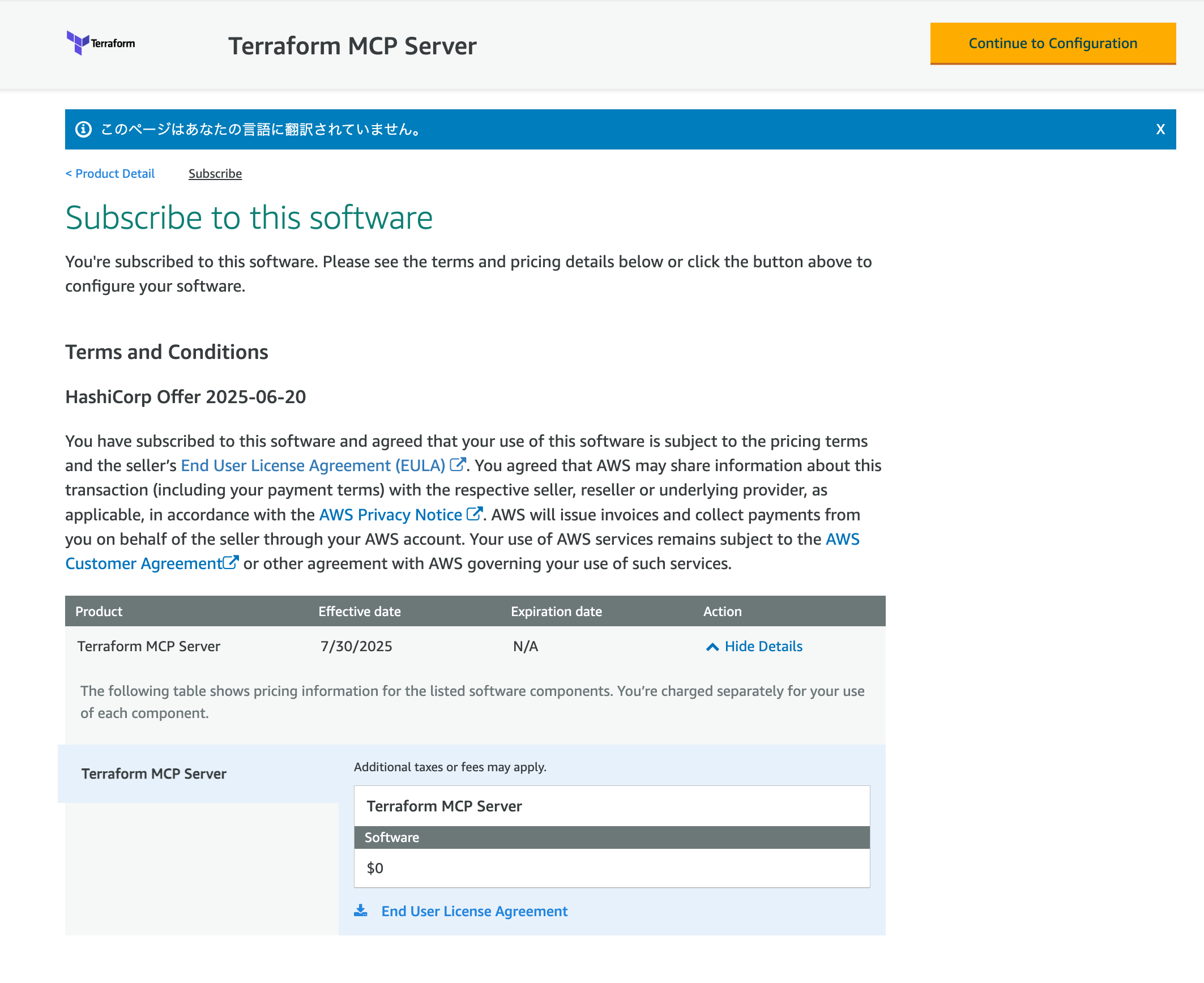
Proceed to configuration from Continue to Configuration.
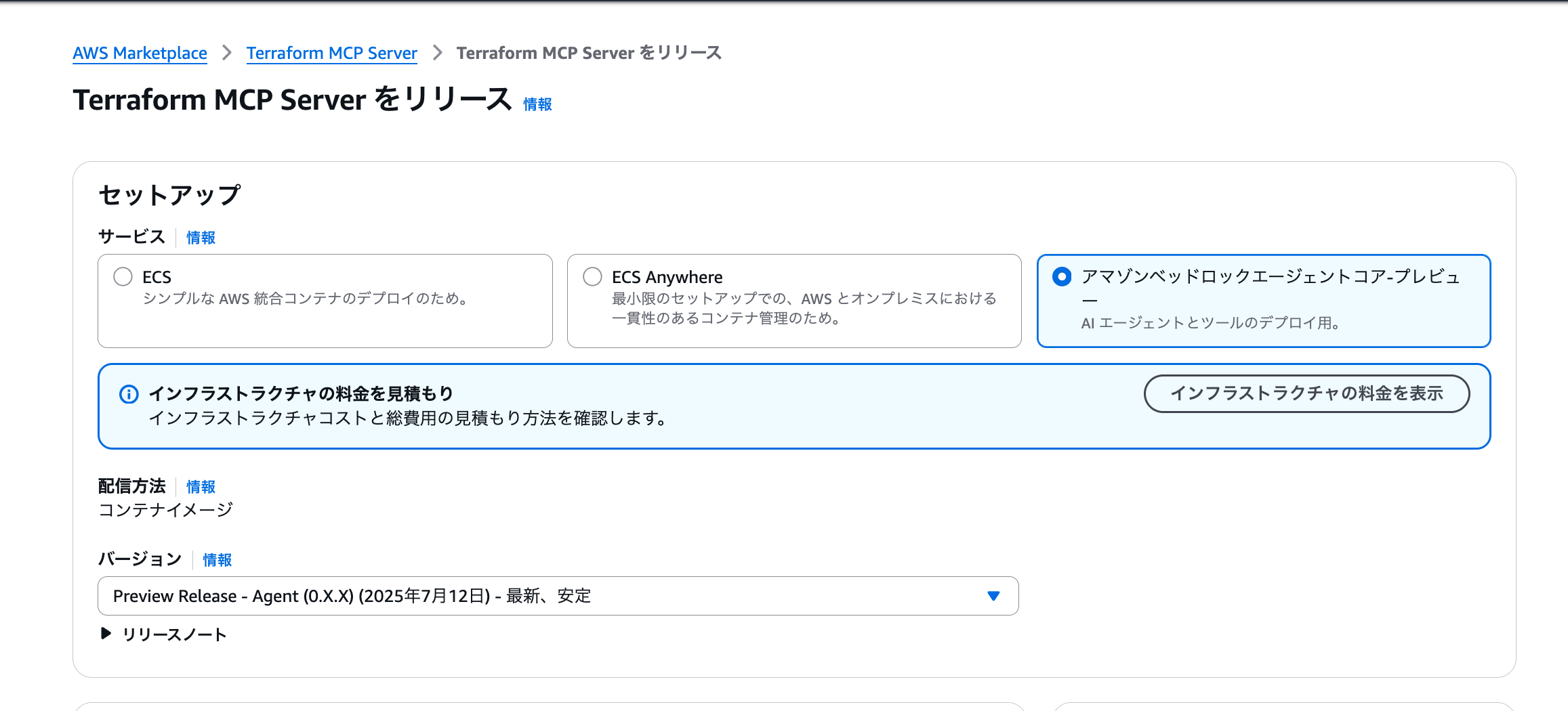
A deployment guide will be displayed as follows.
We'll proceed with deploying to Amazon Bedrock Agent Core according to the guide.
 ### Creating IAM Role for Agent Runtime
### Creating IAM Role for Agent Runtime
We need to create an IAM Role for Agent Runtime.
The IAM Role name is AmazonBedrockAgentCoreRuntimeServiceRole-TerraformMCPServer.
We will create an IAM Role with the following content. Please modify the <accountId> and <region> parts according to your environment.
For <Terraform MCP Server ECR Repo ARN>, the Amazon ECR image URL will be displayed in the guide after subscribing in AWS Marketplace, so convert it to ARN and set it.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "ECRImageAccess",
"Effect": "Allow",
"Action": [
"ecr:BatchGetImage",
"ecr:GetDownloadUrlForLayer"
],
"Resource": [
"<Terraform MCP Server ECR Repo ARN>"
]
},
{
"Effect": "Allow",
"Action": [
"logs:DescribeLogStreams",
"logs:CreateLogGroup"
],
"Resource": [
"arn:aws:logs:<region>:<accountId>:log-group:/aws/bedrock-agentcore/runtimes/*"
]
},
{
"Effect": "Allow",
"Action": [
"logs:DescribeLogGroups"
],
"Resource": [
"arn:aws:logs:<region>:<accountId>:log-group:*"
]
},
{
"Effect": "Allow",
"Action": [
"logs:CreateLogStream",
"logs:PutLogEvents"
],
"Resource": [
"arn:aws:logs:<region>:<accountId>:log-group:/aws/bedrock-agentcore/runtimes/*:log-stream:*"
]
},
{
"Sid": "ECRTokenAccess",
"Effect": "Allow",
"Action": [
"ecr:GetAuthorizationToken"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"xray:PutTraceSegments",
"xray:PutTelemetryRecords",
"xray:GetSamplingRules",
"xray:GetSamplingTargets"
],
"Resource": [ "*" ]
},
{
"Effect": "Allow",
"Resource": "*",
"Action": "cloudwatch:PutMetricData",
"Condition": {
"StringEquals": {
"cloudwatch:namespace": "bedrock-agentcore"
}
}
},
{
"Sid": "GetAgentAccessToken",
"Effect": "Allow",
"Action": [
"bedrock-agentcore:GetWorkloadAccessToken",
"bedrock-agentcore:GetWorkloadAccessTokenForJWT",
"bedrock-agentcore:GetWorkloadAccessTokenForUserId"
],
"Resource": [
"arn:aws:bedrock-agentcore:<region>:<accountId>:workload-identity-directory/default",
"arn:aws:bedrock-agentcore:<region>:<accountId>:workload-identity-directory/default/workload-identity/terraform-mcp*"
]
},
{"Sid": "BedrockModelInvocation",
"Effect": "Allow",
"Action": [
"bedrock:InvokeModel",
"bedrock:InvokeModelWithResponseStream"
],
"Resource": [
"arn:aws:bedrock:*::foundation-model/*",
"arn:aws:bedrock:<region>:<accountId>:*"
]
}
]
}
``````json: Trust relationship
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AssumeRolePolicy",
"Effect": "Allow",
"Principal": {
"Service": "bedrock-agentcore.amazonaws.com"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"aws:SourceAccount": "<accountId>"
},
"ArnLike": {
"aws:SourceArn": "arn:aws:bedrock-agentcore:<region>:<accountId>:*"
}
}
}
]
}
Permissions for AgentCore Runtime - Amazon Bedrock AgentCore
Deploy Terraform MCP to Amazon Bedrock Agent Core
Run the following command to create an Agent Runtime.
aws bedrock-agentcore-control create-agent-runtime \
--region us-east-1 \
--agent-runtime-name "terraform_mcp_server" \
--description "terraform_mcp_server" \
--agent-runtime-artifact '{
"containerConfiguration": {
"containerUri": "<Terraform MCP Server ECR Image URI>"
}
}' \
--role-arn "arn:aws:iam::<accdountId>:role/service-role/AmazonBedrockAgentCoreRuntimeDefaultServiceRole-TerraformMCPServer" \
--network-configuration '{
"networkMode": "PUBLIC"
}' \
--protocol-configuration '{
"serverProtocol": "MCP"
}' \
--environment-variables '{
"MCP_SESSION_MODE": "stateless",
"MCP_CORS_MODE": "strict",
"MCP_ALLOWED_ORIGINS": "http://127.0.0.1:8000",
"TRANSPORT_MODE": "streamable-http",
"TRANSPORT_HOST": "0.0.0.0",
"TRANSPORT_PORT": "8000"
}'
I was able to confirm that the Agent Runtime was created in the management console and that its Status was Ready.
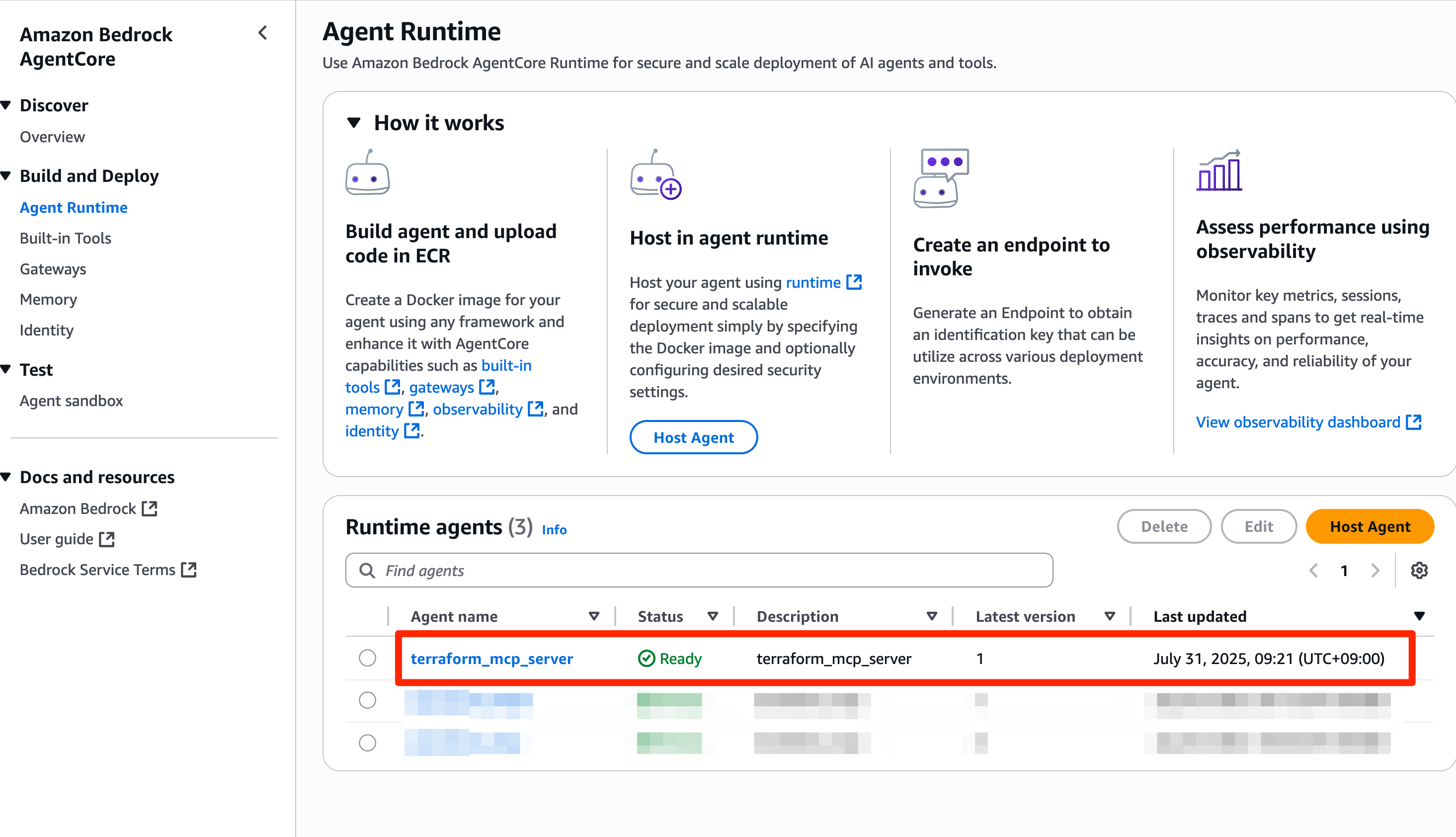 ### Verification: Calling Agent Runtime
### Verification: Calling Agent Runtime
Let's call the deployed Agent Runtime.
Execute the following command. We'll request tools/list to get a list of tools available in the terraform-mcp-server.
export AGENT_RUNTIME_ARN=$(aws bedrock-agentcore-control list-agent-runtimes --query "agentRuntimes[?agentRuntimeName=='terraform_mcp_server'].agentRuntimeArn" --output text)
export PAYLOAD='{ "jsonrpc": "2.0", "id": 1, "method": "tools/list", "params": { "_meta": { "progressToken": 1}}}'
aws bedrock-agentcore invoke-agent-runtime \
--agent-runtime-arn $AGENT_RUNTIME_ARN \
--content-type "application/json" \
--accept "application/json, text/event-stream" \
--payload "$(echo -n "$PAYLOAD" | base64)" output.json
The response is output to output.json.
Let's check the contents to see the tool list.
cat output.json
Output example
{"jsonrpc":"2.0","id":1,"result":{"tools":[{"annotations":{"title":"Fetch detailed Terraform provider documentation using a document ID","readOnlyHint":false,"destructiveHint":true,"idempotentHint":false,"openWorldHint":true},"description":"Fetches up-to-date documentation for a specific service from a Terraform provider. You must call 'resolveProviderDocID' first to obtain the exact tfprovider-compatible providerDocID required to use this tool.","inputSchema":{"properties":{"providerDocID":{"description":"Exact tfprovider-compatible providerDocID, (e.g., '8894603', '8906901') retrieved from 'resolveProviderDocID'","type":"string"}},"required":["providerDocID"],"type":"object"},"name":"getProviderDocs"},{"annotations":{"title":"Retrieve documentation for a specific Terraform module","readOnlyHint":false,"destructiveHint":true,"idempotentHint":false,"openWorldHint":true},"description":"Fetches up-to-date documentation on how to use a Terraform module. You must call 'searchModules' first to obtain the exact valid and compatible moduleID required to use this tool.","inputSchema":{"properties":{"moduleID":{"description":"Exact valid and compatible moduleID retrieved from searchModules (e.g., 'squareops/terraform-kubernetes-mongodb/mongodb/2.1.1', 'GoogleCloudPlatform/vertex-ai/google/0.2.0')","type":"string"}},"required":["moduleID"],"type":"object"},"name":"moduleDetails"},{"annotations":{"title":"Fetch detailed Terraform policy documentation using a terraformPolicyID","readOnlyHint":false,"destructiveHint":true,"idempotentHint":false,"openWorldHint":true},"description":"Fetches up-to-date documentation for a specific policy from the Terraform registry. You must call 'searchPolicies' first to obtain the exact terraformPolicyID required to use this tool.","inputSchema":{"properties":{"terraformPolicyID":{"description":"Matching terraformPolicyID retrieved from the 'searchPolicies' tool (e.g., 'policies/hashicorp/CIS-Policy-Set-for-AWS-Terraform/1.0.1')","type":"string"}},"required":["terraformPolicyID"],"type":"object"},"name":"policyDetails"},{"annotations":{"title":"Identify the most relevant provider document ID for a Terraform service","readOnlyHint":true,"destructiveHint":true,"idempotentHint":false,"openWorldHint":true},"description":"This tool retrieves a list of potential documents based on the serviceSlug and providerDataType provided. You MUST call this function before 'getProviderDocs' to obtain a valid tfprovider-compatible providerDocID. \n\t\t\tUse the most relevant single word as the search query for serviceSlug, if unsure about the serviceSlug, use the providerName for its value.\n\t\t\tWhen selecting the best match, consider: - Title similarity to the query - Category relevance Return the selected providerDocID and explain your choice. \n\t\t\tIf there are multiple good matches, mention this but proceed with the most relevant one.","inputSchema":{"properties":{"providerDataType":{"default":"resources","description":"The type of the document to retrieve, for general information use 'guides', for deploying resources use 'resources', for reading pre-deployed resources use 'data-sources', for functions use 'functions', and for overview of the provider use 'overview'","enum":["resources","data-sources","functions","guides","overview"],"type":"string"},"providerName":{"description":"The name of the Terraform provider to perform the read or deployment operation","type":"string"},"providerNamespace":{"description":"The publisher of the Terraform provider, typically the name of the company, or their GitHub organization name that created the provider","type":"string"},"providerVersion":{"description":"The version of the Terraform provider to retrieve in the format 'x.y.z', or 'latest' to get the latest version","type":"string"},"serviceSlug":{"description":"The slug of the service you want to deploy or read using the Terraform provider, prefer using a single word, use underscores for multiple words and if unsure about the serviceSlug, use the providerName for its value","type":"string"}},"required":["providerName","providerNamespace","serviceSlug"],"type":"object"},"name":"resolveProviderDocID"},{"annotations":{"title":"Search and match Terraform modules based on name and relevance","readOnlyHint":false,"destructiveHint":true,"idempotentHint":false,"openWorldHint":true},"description":"Resolves a Terraform module name to obtain a compatible moduleID for the moduleDetails tool and returns a list of matching Terraform modules. You MUST call this function before 'moduleDetails' to obtain a valid and compatible moduleID. When selecting the best match, consider: - Name similarity to the query - Description relevance - Verification status (verified) - Download counts (popularity) Return the selected moduleID and explain your choice. If there are multiple good matches, mention this but proceed with the most relevant one. If no modules were found, reattempt the search with a new moduleName query.","inputSchema":{"properties":{"currentOffset":{"default":0,"description":"Current offset for pagination","minimum":0,"type":"number"},"moduleQuery":{"description":"The query to search for Terraform modules.","type":"string"}},"required":["moduleQuery"],"type":"object"},"name":"searchModules"},{"annotations":{"title":"Search and match Terraform policies based on name and relevance","readOnlyHint":false,"destructiveHint":true,"idempotentHint":false,"openWorldHint":true},"description":"Searches for Terraform policies based on a query string. This tool returns a list of matching policies, which can be used to retrieve detailed policy information using the 'policyDetails' tool. \n\t\t\tYou MUST call this function before 'policyDetails' to obtain a valid terraformPolicyID.\n\t\t\tWhen selecting the best match, consider: - Name similarity to the query - Title relevance - Verification status (verified) - Download counts (popularity) Return the selected policyID and explain your choice. \n\t\t\tIf there are multiple good matches, mention this but proceed with the most relevant one. If no policies were found, reattempt the search with a new policyQuery.","inputSchema":{"properties":{"policyQuery":{"description":"The query to search for Terraform modules.","type":"string"}},"required":["policyQuery"],"type":"object"},"name":"searchPolicies"}]}}
Conclusion
Terraform MCP Server has been added to the AWS Marketplace.
It has previously been available on GitHub.
Now that it's also published in the Marketplace, it has become an AWS certified solution, making it safer to use.
This was my first time using Amazon Bedrock AgentCore.
I was able to set up a remote MCP server with simple configuration - just preparing a Docker image and IAM role.
Amazon Bedrock AgentCore is available for free trial in preview until September 16, 2025, so I'm looking forward to trying various things during this opportunity.






![[アップデート]TerraformのAWS Transfer Family用のモジュールがSFTPコネクタに対応しました。](https://images.ctfassets.net/ct0aopd36mqt/wp-thumbnail-dd57f8260eaf825c214225faa0278acc/c6d3e347c61a60abea783c1132a311be/aws-transfer-family)
