
Amazon S3バケットに配信できるAWS Configデータのうち、「ConfigHistory」・「ConfigSnapshot」・「AWS CloudTrailを使用したConfig API呼び出しログ」の3つを比較してみた
はじめに
おのやんです。
みなさん、AWS Config(以下、Config)のデータをAmazon S3(以下、S3)バケットに配信したいと思ったことはありませんか?私はあります。
「Configのデータ」とふわっと言いましたが、他の場面では「Configのログ」と言うこともあったり、Configの何のデータを指すのか分からなくなることがあります。筆者自身、これらのデータについて曖昧な理解でごっちゃにしていた背景があり、今回はデータを3種類挙げてそれらの違いについてまとめていきたいと思います。
S3バケットに配信できるConfigのデータ3種
S3バケットに配信できるConfigのデータは3つです。
- ConfigHistory
- ConfigSnapshot
- AWS CloudTrail(以下、CloudTrail)を使用したConfig API呼び出しログ
です。細かく言えば他にもありはしますが、今回はこれらのデータをまとめていきます。
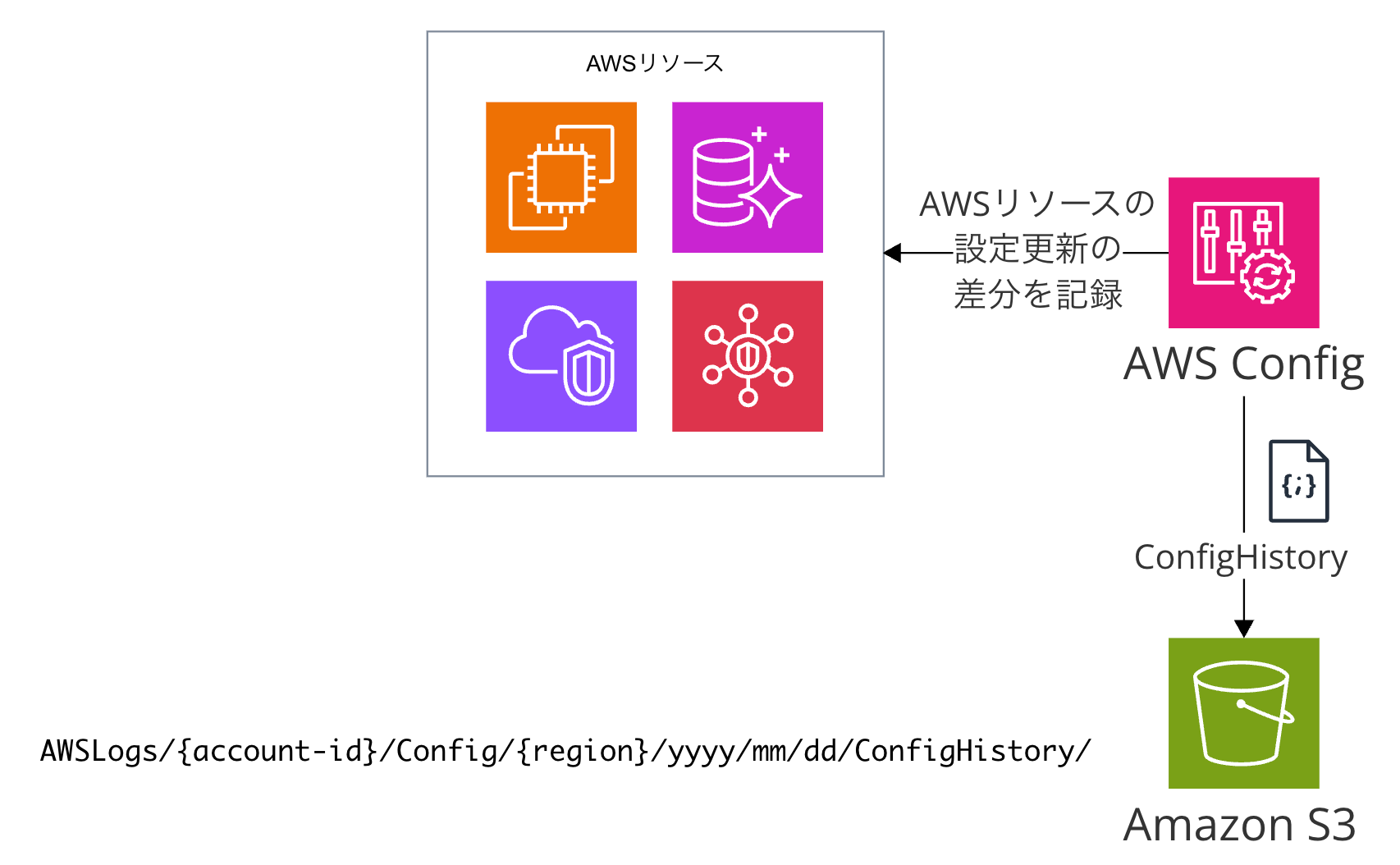
ConfigHistory
ConfigHistoryは、Configのサービスが生成するAWSリソース設定の変更履歴と変更前後の差分です。日本語のAWSドキュメントでは「設定履歴」と訳されています。
S3に保存する場合は、データの流れとしてはConfig → S3バケットです。Config用バケットにて、AWSLogs/{account-id}/Config/{region}/yyyy/mm/dd/ConfigHistory/のパスの直下に記録されます。
例えば、こんな感じのJSON形式で記述されます。
ConfigHistoryの例
{
"fileVersion": "1.0",
"configurationItems": [
{
"relatedEvents": [],
"relationships": [
{
"resourceId": "SecurityHubAccepter-LambdaFunction-TznYtfenhJP0",
"resourceType": "AWS::Lambda::Function",
"name": "Is associated with "
}
],
"configuration": {
"complianceType": "NON_COMPLIANT",
"targetResourceId": "SecurityHubAccepter-LambdaFunction-TznYtfenhJP0",
"targetResourceType": "AWS::Lambda::Function",
"configRuleList": [
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-9chg6a",
"configRuleId": "config-rule-9chg6a",
"configRuleName": "securityhub-lambda-function-settings-check-dffd84a5",
"complianceType": "NON_COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-jjgsho",
"configRuleId": "config-rule-jjgsho",
"configRuleName": "securityhub-lambda-function-public-access-prohibited-dd612fa0",
"complianceType": "COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-qqi2mk",
"configRuleId": "config-rule-qqi2mk",
"configRuleName": "securityhub-lambda-inside-vpc-02636789",
"complianceType": "NON_COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-ahsbwu",
"configRuleId": "config-rule-ahsbwu",
"configRuleName": "securityhub-lambda-function-xray-enabled-8b95331d",
"complianceType": "NON_COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-lvotoo",
"configRuleId": "config-rule-lvotoo",
"configRuleName": "securityhub-lambda-function-settings-check-27cb7b04",
"complianceType": "NON_COMPLIANT"
}
]
},
"supplementaryConfiguration": {},
"tags": {},
"configurationItemVersion": "1.3",
"configurationItemCaptureTime": "2026-01-13T07:22:34.366Z",
"configurationStateId": 1768288954366,
"awsAccountId": "XXXXXXXXXXXX",
"configurationItemStatus": "OK",
"resourceType": "AWS::Config::ResourceCompliance",
"resourceId": "AWS::Lambda::Function/SecurityHubAccepter-LambdaFunction-TznYtfenhJP0",
"awsRegion": "ap-northeast-1",
"configurationStateMd5Hash": ""
},
{
"relatedEvents": [],
"relationships": [
{
"resourceId": "SecurityHubAccepter-LambdaFunction-TznYtfenhJP0",
"resourceType": "AWS::Lambda::Function",
"name": "Is associated with "
}
],
"configuration": {
"complianceType": "NON_COMPLIANT",
"targetResourceId": "SecurityHubAccepter-LambdaFunction-TznYtfenhJP0",
"targetResourceType": "AWS::Lambda::Function",
"configRuleList": [
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-jjgsho",
"configRuleId": "config-rule-jjgsho",
"configRuleName": "securityhub-lambda-function-public-access-prohibited-dd612fa0",
"complianceType": "COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-qqi2mk",
"configRuleId": "config-rule-qqi2mk",
"configRuleName": "securityhub-lambda-inside-vpc-02636789",
"complianceType": "NON_COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-ahsbwu",
"configRuleId": "config-rule-ahsbwu",
"configRuleName": "securityhub-lambda-function-xray-enabled-8b95331d",
"complianceType": "NON_COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-lvotoo",
"configRuleId": "config-rule-lvotoo",
"configRuleName": "securityhub-lambda-function-settings-check-27cb7b04",
"complianceType": "NON_COMPLIANT"
}
]
},
"supplementaryConfiguration": {},
"tags": {},
"configurationItemVersion": "1.3",
"configurationItemCaptureTime": "2026-01-13T11:14:11.813Z",
"configurationStateId": 1768302851813,
"awsAccountId": "XXXXXXXXXXXX",
"configurationItemStatus": "OK",
"resourceType": "AWS::Config::ResourceCompliance",
"resourceId": "AWS::Lambda::Function/SecurityHubAccepter-LambdaFunction-TznYtfenhJP0",
"awsRegion": "ap-northeast-1",
"configurationStateMd5Hash": ""
},
{
"relatedEvents": [],
"relationships": [
{
"resourceId": "notify-aws-billing",
"resourceType": "AWS::Lambda::Function",
"name": "Is associated with "
}
],
"configuration": {
"complianceType": "NON_COMPLIANT",
"targetResourceId": "notify-aws-billing",
"targetResourceType": "AWS::Lambda::Function",
"configRuleList": [
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-9chg6a",
"configRuleId": "config-rule-9chg6a",
"configRuleName": "securityhub-lambda-function-settings-check-dffd84a5",
"complianceType": "COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-jjgsho",
"configRuleId": "config-rule-jjgsho",
"configRuleName": "securityhub-lambda-function-public-access-prohibited-dd612fa0",
"complianceType": "COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-qqi2mk",
"configRuleId": "config-rule-qqi2mk",
"configRuleName": "securityhub-lambda-inside-vpc-02636789",
"complianceType": "NON_COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-ahsbwu",
"configRuleId": "config-rule-ahsbwu",
"configRuleName": "securityhub-lambda-function-xray-enabled-8b95331d",
"complianceType": "COMPLIANT"
},
{
"configRuleArn": "arn:aws:config:ap-northeast-1:XXXXXXXXXXXX:config-rule/aws-service-rule/securityhub.amazonaws.com/config-rule-lvotoo",
"configRuleId": "config-rule-lvotoo",
"configRuleName": "securityhub-lambda-function-settings-check-27cb7b04",
"complianceType": "COMPLIANT"
}
]
},
"supplementaryConfiguration": {},
"tags": {},
"configurationItemVersion": "1.3",
"configurationItemCaptureTime": "2026-01-13T07:22:31.344Z",
"configurationStateId": 1768288951344,
"awsAccountId": "XXXXXXXXXXXX",
"configurationItemStatus": "OK",
"resourceType": "AWS::Config::ResourceCompliance",
"resourceId": "AWS::Lambda::Function/notify-aws-billing",
"awsRegion": "ap-northeast-1",
"configurationStateMd5Hash": ""
}
]
}
「Configのデータを有効化してS3に送信する」といった場合、多くのケースではこのConfigHistoryがS3に送信さることになると思います。
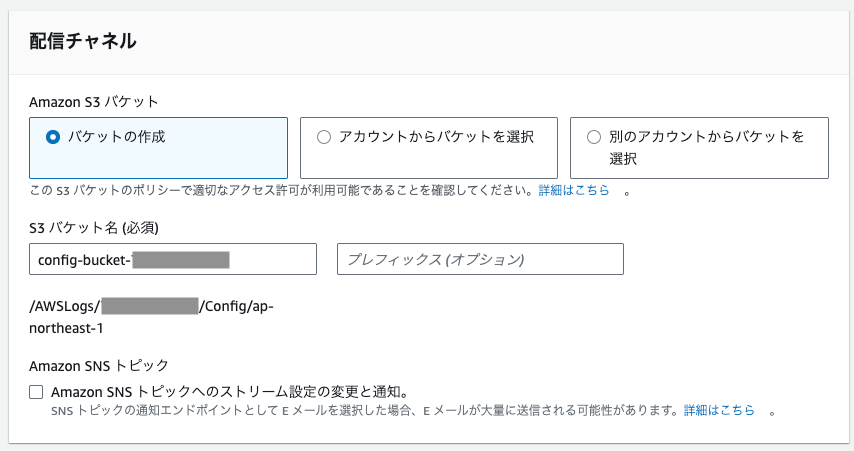
例えばAWSコンソール画面上でConfigを有効化する場合は、S3バケットを選択することができます。正常に有効化されると、ConfigHistoryをS3に送信できるようになります。
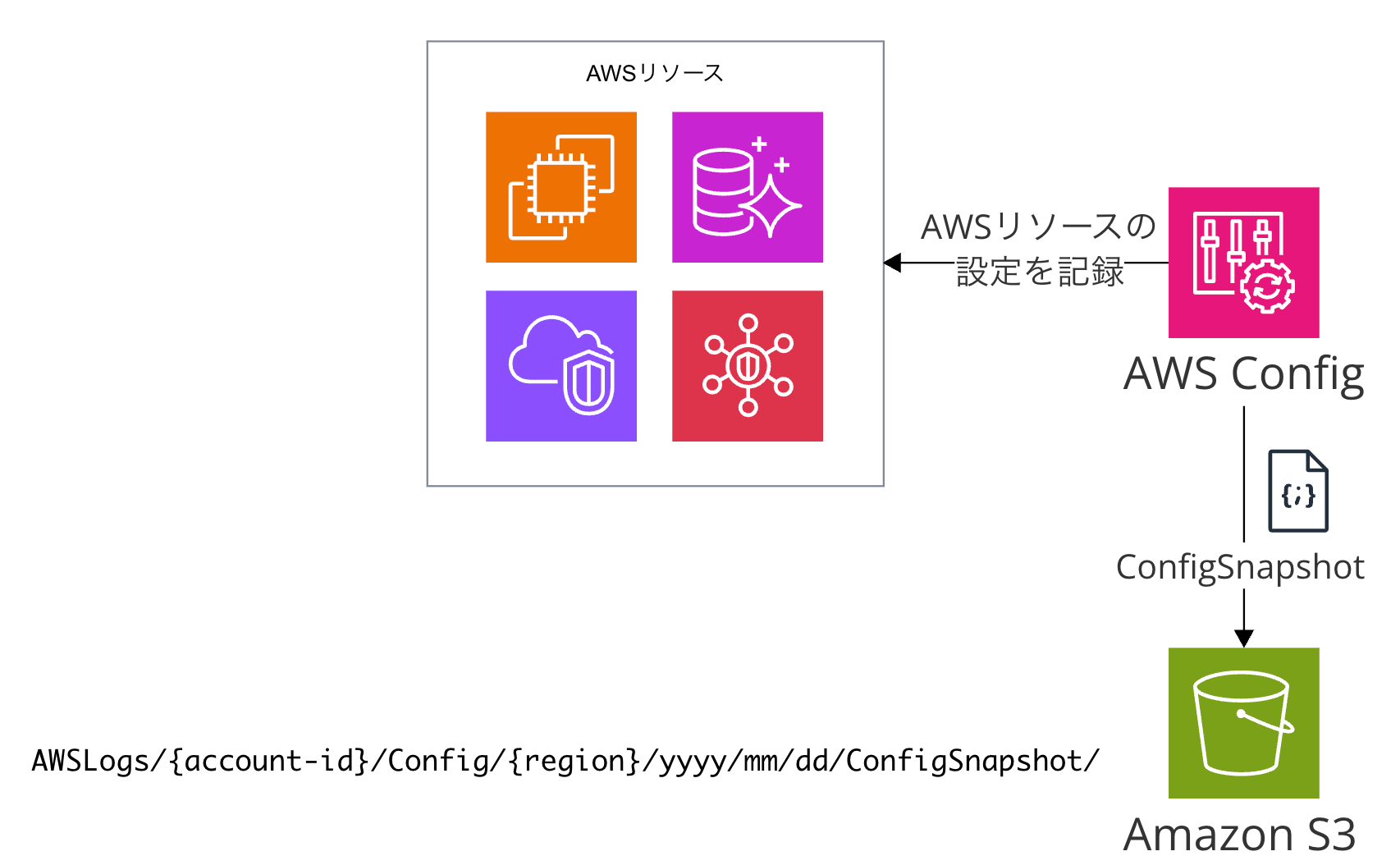
ConfigSnapshot
ConfigSnapshotは、Configのサービスが生成するAWSリソース設定の定期的なスナップショットです。日本語のAWSドキュメントでは「設定スナップショット」と訳されています。
S3に保存する場合は、データの流れとしてはConfig → S3バケットです。Config用バケットにて、AWSLogs/{account-id}/Config/{region}/yyyy/mm/dd/ConfigSnapshot/のパスの直下に記録されます。
例えば、こんな感じのJSON形式で記述されます。
ConfigSnapshotの例
{
"fileVersion": "1.0",
"requestId": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"configurationItems": [
{
"configurationItemVersion": "1.0",
"resourceId": "vol-XXXXXXXXXX",
"arn": "arn:aws:us-west-2b:XXXXXXXXXXXX:volume/vol-XXXXXXXXXX",
"accountId": "XXXXXXXXXXXX",
"configurationItemCaptureTime": "2014-03-07T23:47:08.918Z",
"configurationStateID": "YYYYYYYY-YYYY-YYYY-YYYY-YYYYYYYYYYYY",
"configurationItemStatus": "OK",
"relatedEvents": [
"AAAAAAAA-AAAA-AAAA-AAAA-AAAAAAAAAAAA",
"BBBBBBBB-BBBB-BBBB-BBBB-BBBBBBBBBBBB"
],
"availabilityZone": "us-west-2b",
"resourceType": "AWS::EC2::Volume",
"resourceCreationTime": "2014-02-27T21:43:53.885Z",
"tags": {},
"relationships": [
{
"resourceId": "i-XXXXXXXXXX",
"resourceType": "AWS::EC2::Instance",
"name": "Attached to Instance"
}
],
"configuration": {
"volumeId": "vol-XXXXXXXXXX",
"size": 1,
"snapshotId": "",
"availabilityZone": "us-west-2b",
"state": "in-use",
"createTime": "2014-02-27T21:43:53.0885+0000",
"attachments": [
{
"volumeId": "vol-XXXXXXXXXX",
"instanceId": "i-XXXXXXXXXX",
"device": "/dev/sdf",
"state": "attached",
"attachTime": "2014-03-07T23:46:28.0000+0000",
"deleteOnTermination": false
}
],
"tags": [
{
"tagName": "environment",
"tagValue": "PROD"
},
{
"tagName": "name",
"tagValue": "DataVolume1"
}
],
"volumeType": "standard"
}
},
{
"configurationItemVersion": "1.0",
"resourceId": "i-XXXXXXXXXX",
"accountId": "XXXXXXXXXXXX",
"arn": "arn:aws:ec2:us-west-2b:XXXXXXXXXXXX:instance/i-XXXXXXXXXX",
"configurationItemCaptureTime": "2014-03-07T23:47:09.523Z",
"configurationStateID": "ZZZZZZZZ-ZZZZ-ZZZZ-ZZZZ-ZZZZZZZZZZZZ",
"configurationItemStatus": "OK",
"relatedEvents": [
"AAAAAAAA-AAAA-AAAA-AAAA-AAAAAAAAAAAA",
"BBBBBBBB-BBBB-BBBB-BBBB-BBBBBBBBBBBB"
],
"availabilityZone": "us-west-2b",
"resourceType": "AWS::EC2::Instance",
"resourceCreationTime": "2014-02-26T22:56:35.000Z",
"tags": {
"Name": "integ-test-1",
"examplename": "examplevalue"
},
"relationships": [
{
"resourceId": "vol-XXXXXXXXXX",
"resourceType": "AWS::EC2::Volume",
"name": "Attached Volume"
},
{
"resourceId": "vol-YYYYYYYYYY",
"resourceType": "AWS::EC2::Volume",
"name": "Attached Volume",
"direction": "OUT"
},
{
"resourceId": "subnet-XXXXXXXXXX",
"resourceType": "AWS::EC2::SUBNET",
"name": "Is contained in Subnet",
"direction": "IN"
}
],
"configuration": {
"instanceId": "i-XXXXXXXXXX",
"imageId": "ami-XXXXXXXXXX",
"state": {
"code": 16,
"name": "running"
},
"privateDnsName": "ip-10-0-1-100.us-west-2.compute.internal",
"publicDnsName": "ec2-203-0-113-50.us-west-2.compute.amazonaws.com",
"stateTransitionReason": "",
"keyName": "example-key",
"amiLaunchIndex": 0,
"productCodes": [],
"instanceType": "t1.micro",
"launchTime": "2014-02-26T22:56:35.0000+0000",
"placement": {
"availabilityZone": "us-west-2b",
"groupName": "",
"tenancy": "default"
},
"kernelId": "aki-XXXXXXXXXX",
"monitoring": {
"state": "disabled"
},
"subnetId": "subnet-XXXXXXXXXX",
"vpcId": "vpc-XXXXXXXXXX",
"privateIpAddress": "10.0.1.100",
"publicIpAddress": "203.0.113.50",
"architecture": "x86_64",
"rootDeviceType": "ebs",
"rootDeviceName": "/dev/sda1",
"blockDeviceMappings": [
{
"deviceName": "/dev/sda1",
"ebs": {
"volumeId": "vol-YYYYYYYYYY",
"status": "attached",
"attachTime": "2014-02-26T22:56:38.0000+0000",
"deleteOnTermination": true
}
},
{
"deviceName": "/dev/sdf",
"ebs": {
"volumeId": "vol-XXXXXXXXXX",
"status": "attached",
"attachTime": "2014-03-07T23:46:28.0000+0000",
"deleteOnTermination": false
}
}
],
"virtualizationType": "paravirtual",
"clientToken": "example-token",
"tags": [
{
"key": "Name",
"value": "integ-test-1"
},
{
"key": "examplekey",
"value": "examplevalue"
}
],
"securityGroups": [
{
"groupName": "launch-wizard-2",
"groupId": "sg-XXXXXXXXXX"
}
],
"sourceDestCheck": true,
"hypervisor": "xen",
"networkInterfaces": [
{
"networkInterfaceId": "eni-XXXXXXXXXX",
"subnetId": "subnet-XXXXXXXXXX",
"vpcId": "vpc-XXXXXXXXXX",
"description": "",
"ownerId": "XXXXXXXXXXXX",
"status": "in-use",
"privateIpAddress": "10.0.1.100",
"privateDnsName": "ip-10-0-1-100.us-west-2.compute.internal",
"sourceDestCheck": true,
"groups": [
{
"groupName": "launch-wizard-2",
"groupId": "sg-XXXXXXXXXX"
}
],
"attachment": {
"attachmentId": "eni-attach-XXXXXXXXXX",
"deviceIndex": 0,
"status": "attached",
"attachTime": "2014-02-26T22:56:35.0000+0000",
"deleteOnTermination": true
},
"association": {
"publicIp": "203.0.113.50",
"publicDnsName": "ec2-203-0-113-50.us-west-2.compute.amazonaws.com",
"ipOwnerId": "amazon"
},
"privateIpAddresses": [
{
"privateIpAddress": "10.0.1.100",
"privateDnsName": "ip-10-0-1-100.us-west-2.compute.internal",
"primary": true,
"association": {
"publicIp": "203.0.113.50",
"publicDnsName": "ec2-203-0-113-50.us-west-2.compute.amazonaws.com",
"ipOwnerId": "amazon"
}
}
]
}
],
"ebsOptimized": false
}
}
]
}
ConfigHistoryがほぼデフォルトのような形でS3に配信される一方で、ConfigSnapshotはAWS CLI経由で有効化した場合のみS3に配信できます。
ConfigSnapshotは、AWSコンソール上では取得できません。DeliverConfigSnapshotアクションを呼び出すか、AWS CLIコマンドを実行することでのみ、ConfigSnapshotを生成できます。ConfigSnapshotが生成されたら、Configを有効にした際に指定したS3バケットに保存されます。
例えば、次のようなコマンドを実行することでConfigSnapshotを生成できます。詳細はAWSドキュメントを参照ください。
$ aws configservice deliver-config-snapshot --delivery-channel-name default
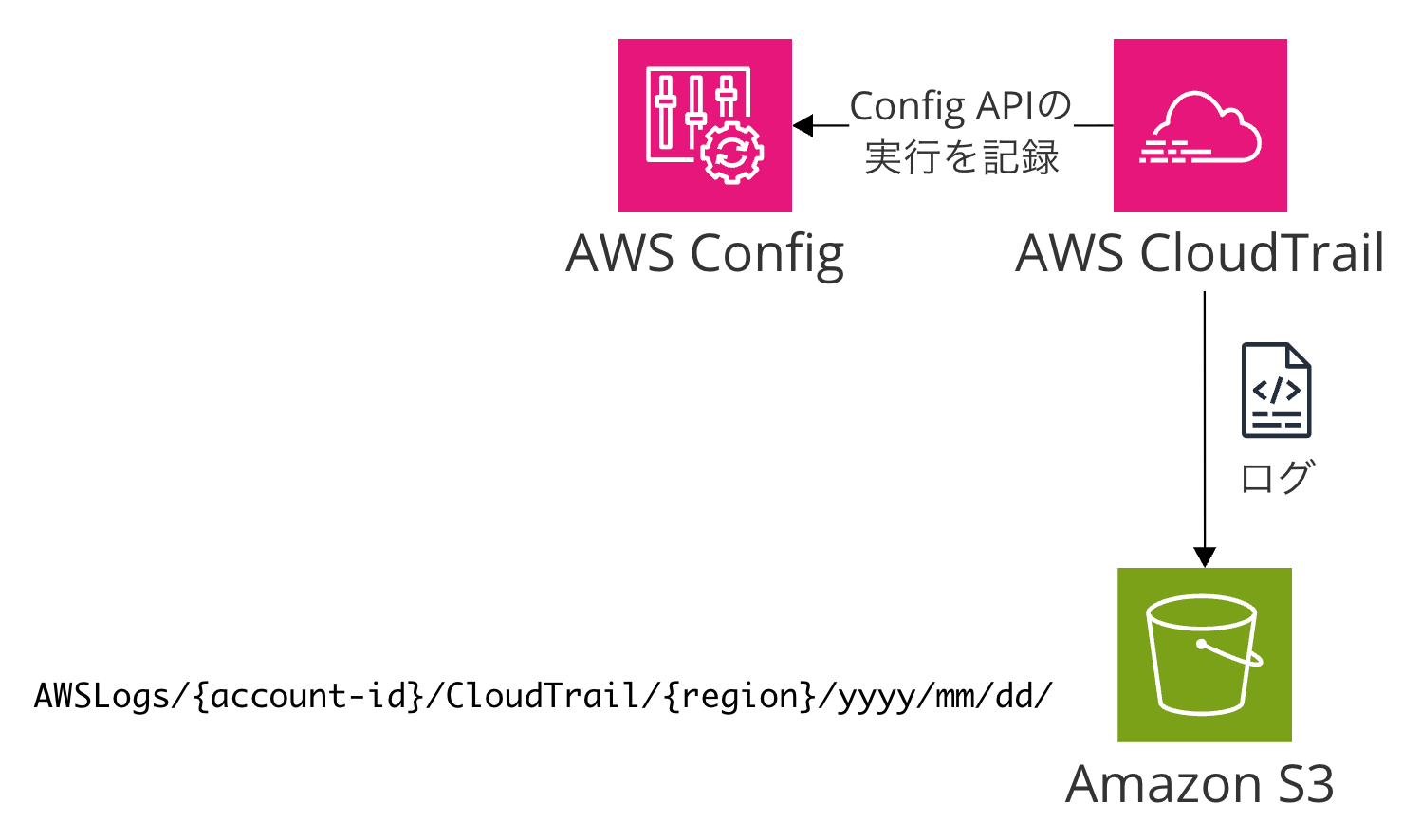
CloudTrailを使用したConfig API呼び出しログ
上記2つのデータは、Config自身が生成するデータでした。それに対して、Configというサービス自身のAPI呼び出しを記録する場合は、AWS CloudTrail(以下、CloudTrail)を使用してConfig API呼び出しログを記録する必要があります。
S3に保存する場合は、データの流れとしては、Config API呼び出し → CloudTrail → S3バケットです。CloudTrail用バケットにて、AWSLogs/{account-id}/CloudTrail/{region}/yyyy/mm/dd/のパスの直下に記録されます。ログを記録する主体はConfigではなくCloudTrailです。Config自身がログを生成するわけではないので、混同しないしようにしましょう。
データとしては、JSONの配列になります。
CloudTrailを使用したConfig API呼び出しログの例
{
"Records": [
{
"eventVersion": "1.11",
"userIdentity": {
"type": "AWSService",
"invokedBy": "cloudtrail.amazonaws.com"
},
"eventTime": "2026-01-27T04:29:55Z",
"eventSource": "kms.amazonaws.com",
"eventName": "GenerateDataKey",
"awsRegion": "ap-northeast-1",
"sourceIPAddress": "cloudtrail.amazonaws.com",
"userAgent": "cloudtrail.amazonaws.com",
"requestParameters": {
"encryptionContext": {
"aws:cloudtrail:arn": "arn:aws:cloudtrail:ap-northeast-1:XXXXXXXXXXXX:trail/Members",
"aws:s3:arn": "arn:aws:s3:::cm-members-cloudtrail-XXXXXXXXXXXX"
},
"keySpec": "AES_256",
"keyId": "arn:aws:kms:ap-northeast-1:XXXXXXXXXXXX:key/XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX"
},
"responseElements": null,
"additionalEventData": {
"keyMaterialId": "XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX"
},
"requestID": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"eventID": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"readOnly": true,
"resources": [
{
"accountId": "XXXXXXXXXXXX",
"type": "AWS::KMS::Key",
"ARN": "arn:aws:kms:ap-northeast-1:XXXXXXXXXXXX:key/XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX"
}
],
"eventType": "AwsApiCall",
"managementEvent": true,
"recipientAccountId": "XXXXXXXXXXXX",
"sharedEventID": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"eventCategory": "Management"
},
{
"eventVersion": "1.11",
"userIdentity": {
"type": "AWSAccount",
"principalId": "XXXXXXXXXXXXXXXXXXXXX",
"accountId": "XXXXXXXXXXXX",
"invokedBy": "AWS Internal"
},
"eventTime": "2026-01-27T04:30:41Z",
"eventSource": "sts.amazonaws.com",
"eventName": "AssumeRole",
"awsRegion": "ap-northeast-1",
"sourceIPAddress": "AWS Internal",
"userAgent": "AWS Internal",
"requestParameters": {
"roleArn": "arn:aws:iam::XXXXXXXXXXXX:role/cm-REDACTED_USER",
"roleSessionName": "cm-REDACTED_USER"
},
"responseElements": {
"credentials": {
"accessKeyId": "XXXXXXXXXXXXXXXXXXXX",
"sessionToken": "REDACTED_SESSION_TOKEN",
"expiration": "Jan 27, 2026, 5:30:41 AM"
},
"assumedRoleUser": {
"assumedRoleId": "XXXXXXXXXXXXXXXXXXXXX:cm-REDACTED_USER",
"arn": "arn:aws:sts::XXXXXXXXXXXX:assumed-role/cm-REDACTED_USER/cm-REDACTED_USER"
}
},
"additionalEventData": {
"ExtendedRequestId": "XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX"
},
"requestID": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"eventID": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"readOnly": true,
"resources": [
{
"accountId": "XXXXXXXXXXXX",
"type": "AWS::IAM::Role",
"ARN": "arn:aws:iam::XXXXXXXXXXXX:role/cm-REDACTED_USER"
}
],
"eventType": "AwsApiCall",
"managementEvent": true,
"recipientAccountId": "XXXXXXXXXXXX",
"sharedEventID": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"eventCategory": "Management"
},
{
"eventVersion": "1.11",
"userIdentity": {
"type": "AssumedRole",
"principalId": "XXXXXXXXXXXXXXXXXXXXX:cm-REDACTED_USER",
"arn": "arn:aws:sts::XXXXXXXXXXXX:assumed-role/cm-REDACTED_USER/cm-REDACTED_USER",
"accountId": "XXXXXXXXXXXX",
"accessKeyId": "XXXXXXXXXXXXXXXXXXXX",
"sessionContext": {
"sessionIssuer": {
"type": "Role",
"principalId": "XXXXXXXXXXXXXXXXXXXXX",
"arn": "arn:aws:iam::XXXXXXXXXXXX:role/cm-REDACTED_USER",
"accountId": "XXXXXXXXXXXX",
"userName": "cm-REDACTED_USER"
},
"attributes": {
"creationDate": "2026-01-27T04:30:41Z",
"mfaAuthenticated": "true"
}
}
},
"eventTime": "2026-01-27T04:30:44Z",
"eventSource": "ec2.amazonaws.com",
"eventName": "DescribeRegions",
"awsRegion": "ap-northeast-1",
"sourceIPAddress": "XXX.XXX.XXX.XXX",
"userAgent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/144.0.0.0 Safari/537.36",
"requestParameters": {
"regionSet": {},
"allRegions": true
},
"responseElements": null,
"requestID": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"eventID": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX",
"readOnly": true,
"eventType": "AwsApiCall",
"managementEvent": true,
"recipientAccountId": "XXXXXXXXXXXX",
"eventCategory": "Management",
"tlsDetails": {
"tlsVersion": "TLSv1.3",
"cipherSuite": "TLS_AES_128_GCM_SHA256",
"clientProvidedHostHeader": "ec2.ap-northeast-1.amazonaws.com"
},
"sessionCredentialFromConsole": "true"
}
]
}
「Configのログ」という呼び方ですと、筆者個人的にはこちらをイメージします。これ多分人によってイメージするデータが違う気がするので、「Config自体が生成するデータ」や「CloudTrailが記録するConfigのログ」というように、呼び方には注意した方がいいかもしれません。
これらの区別が必要になりそうな場面
例えばマルチアカウント環境などでConfig関連のデータを別アカウントに送信・複製する場合に、「Config関連のデータ」が何を指すかによって、設定するS3バケットが違ってきます。
Config自身が記録したデータ、すなわちConfigHistoryやConfigSnapshotを別アカウントに送信・複製したい場合は、Config用S3バケットの設定に変更を加える必要がありますし、Config自身が実行したアクション・APIを別アカウントに送信・複製したい場合は、CloudTrail用S3バケットの設定に変更を加える必要があります。
「Configデータ」などという呼び方には気をつけよう
状況によっては、「Configデータ」みたいな呼び方のデータが何を指すのか曖昧だと、どのAWSリソースの設定を変更すればいいかわからなくなります。
AWSサービスの概念の全体像を、改めて見直しできるとよさそうです。では!









