When using CodeCommit with Amplify, an error occurs with PowerUserAccess, so please provide a solution
この記事は公開されてから1年以上経過しています。情報が古い可能性がありますので、ご注意ください。
The issue
When an IAM user with PowerUserAccess tries to create an application in the Amplify console and selects CodeCommit as the Git repository, an error occurs.
fatal: unable to access 'https://git-codecommit.{region}.amazonaws.com/v1/repos/{repository-name}/': The requested URL returned error: 403
Please tell me the solution to the above error.
The solution
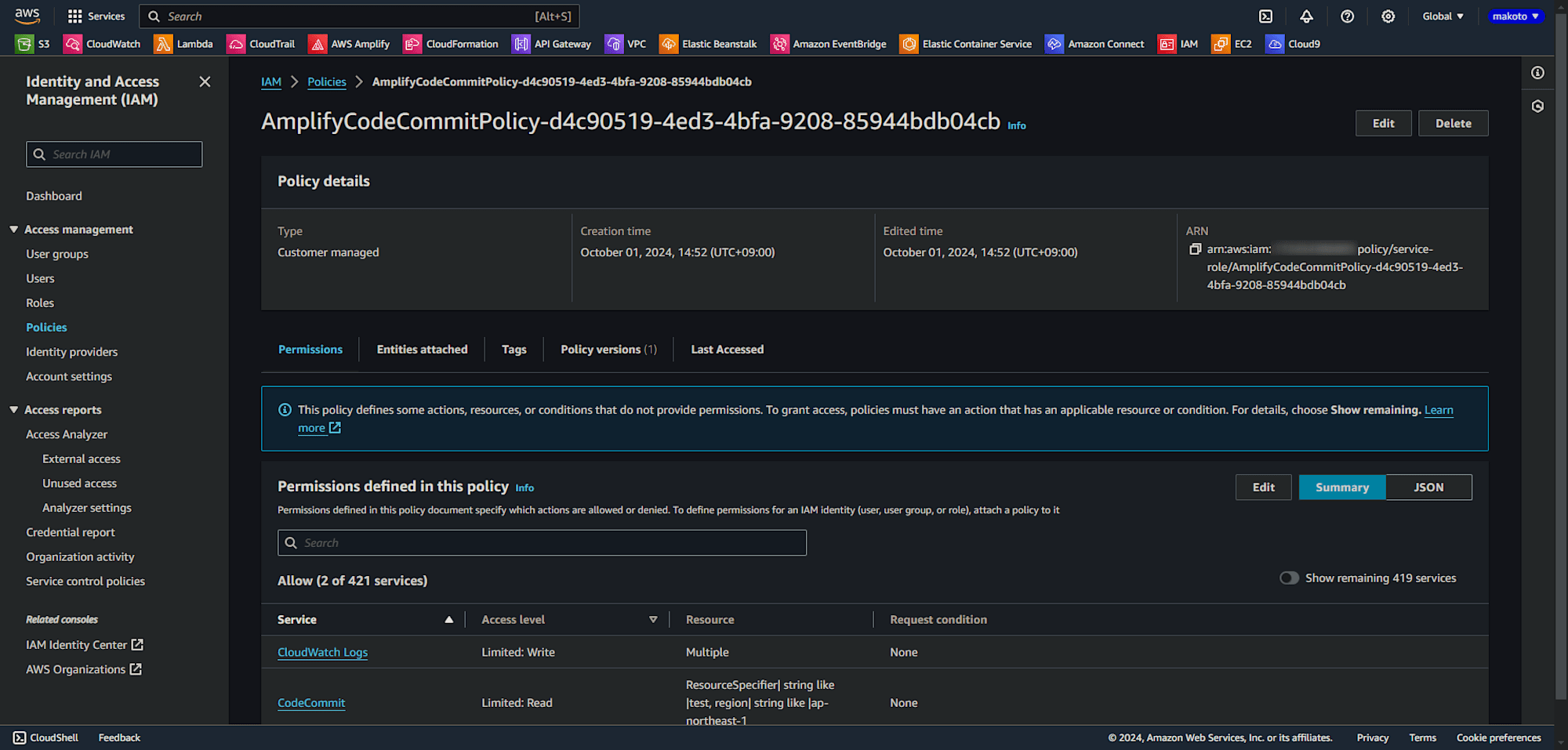
In addition to PowerUserAccess, please grant the following permissions.
- CreatePolicy
- CreateRole
- AttachRolePolicy
- PassRole
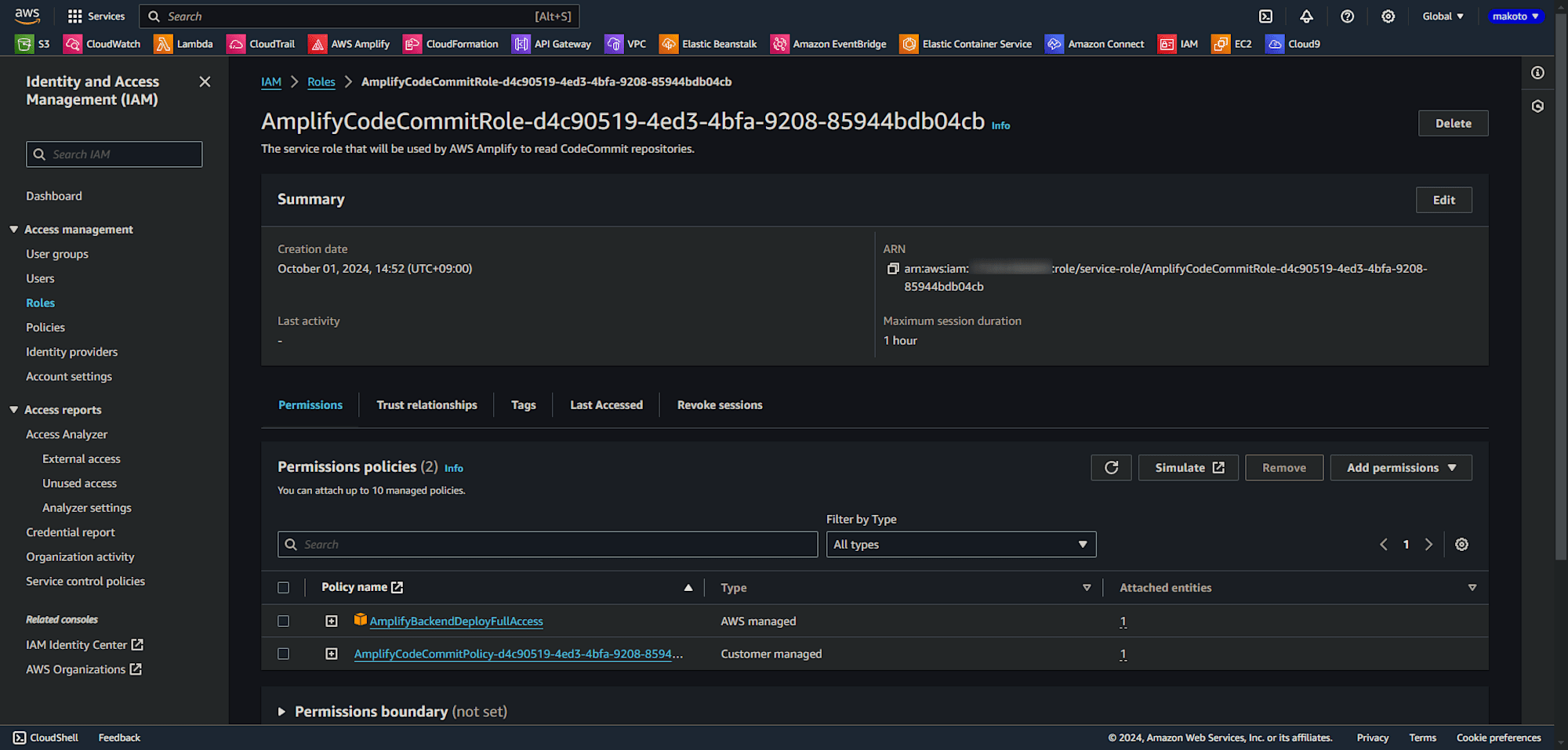
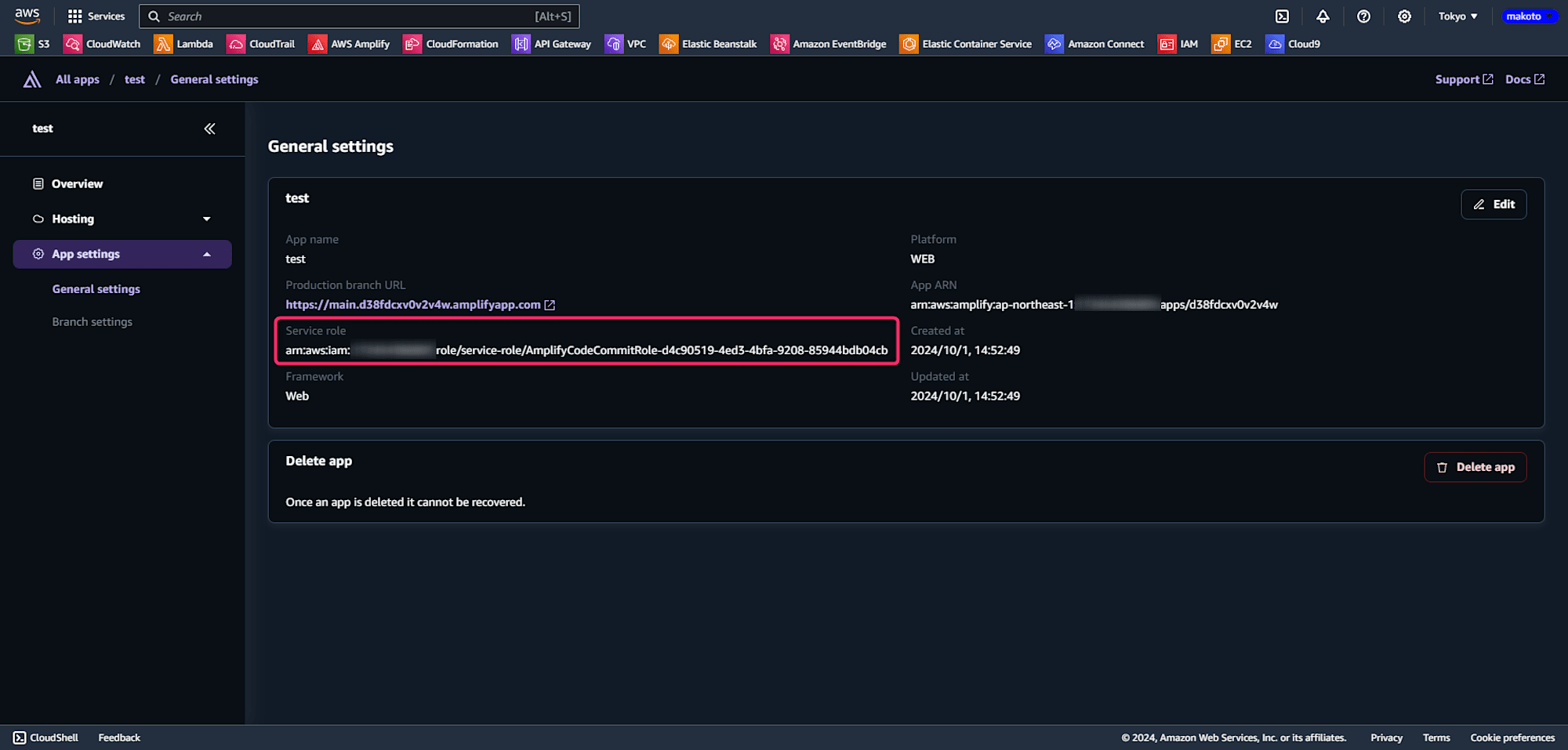
When creating an application in the Amplify console, the following IAM policy and IAM role are created, which become the service roles for Amplify.
- AmplifyCodeCommitPolicy-adb0db8d-df57-49bf-b038-817081c1742b
- AmplifyCodeCommitRole-adb0db8d-df57-49bf-b038-817081c1742b
To create the aforementioned IAM policy and IAM role and set them as the service role for Amplify, the four aforementioned IAM permissions are required.
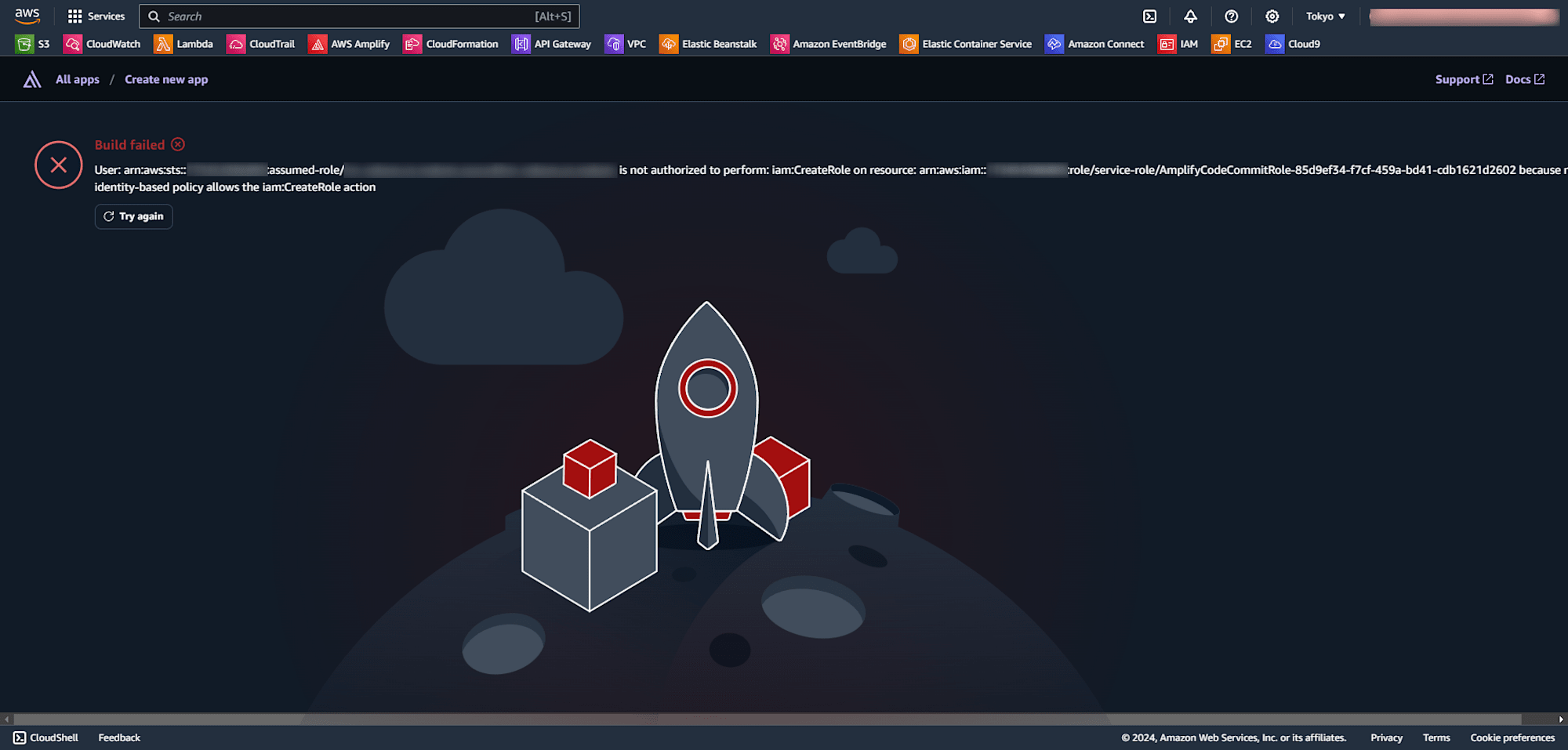
However, since PowerUserAccess does not include IAM-related permissions, an error occurs with PowerUserAccess alone.
I tried it
I tested both the pattern with only PowerUserAccess and the pattern with PowerUserAccess + the four additional permissions.
Note that the application has already been pushed to CodeCommit.
The pattern with only PowerUserAccess
When I tried to create an application in the Amplify console, the following error occurred.
The pattern with PowerUserAccess + 4 permissions
In addition to PowerUserAccess, grant the following permissions.
- CreatePolicy
- CreateRole
- AttachRolePolicy
- PassRole
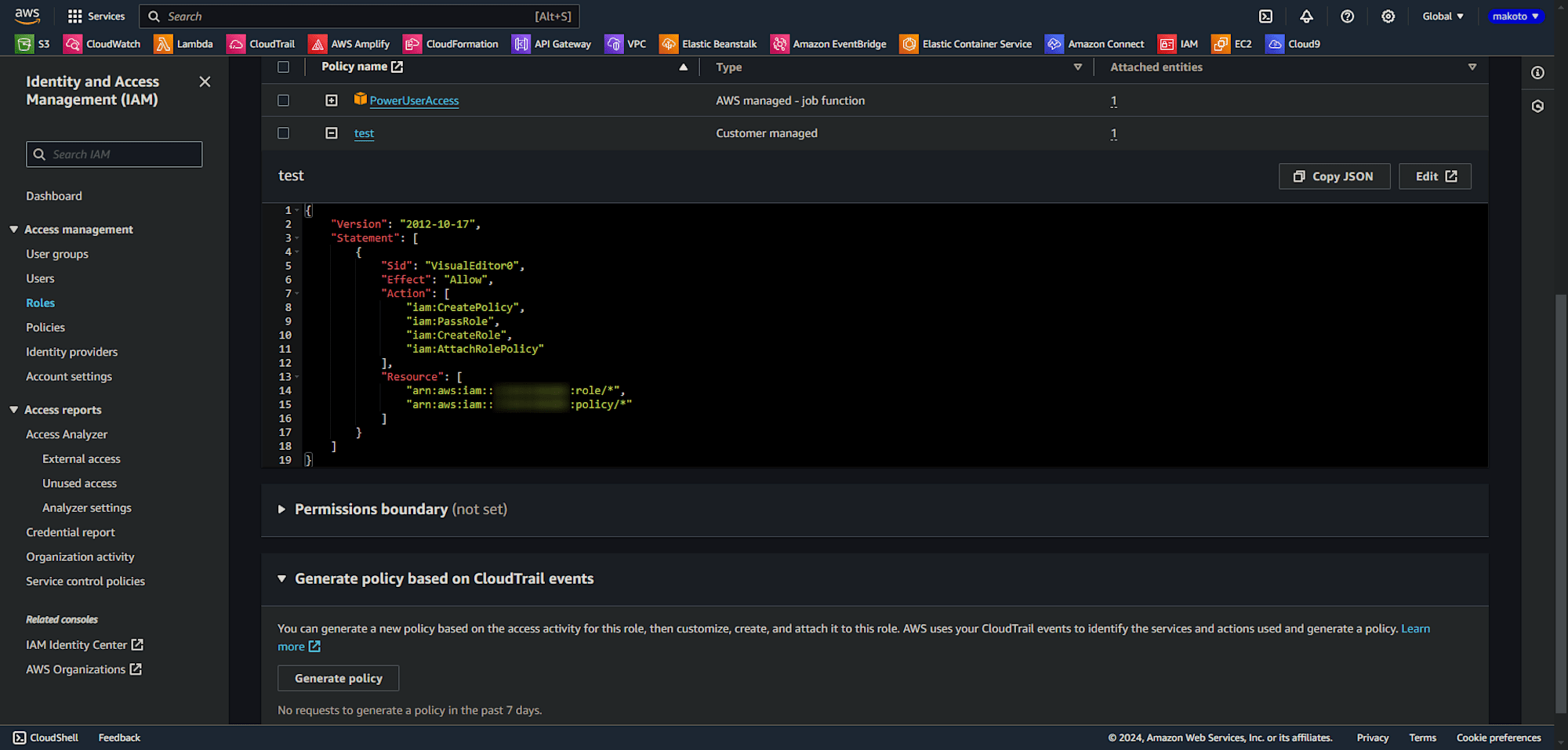
This time, I created the following IAM policy and attached it to the target IAM user.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"iam:CreatePolicy",
"iam:PassRole",
"iam:CreateRole",
"iam:AttachRolePolicy"
],
"Resource": [
"arn:aws:iam::{Accout-ID}:role/*",
"arn:aws:iam::{Accout-ID}:policy/*"
]
}
]
}
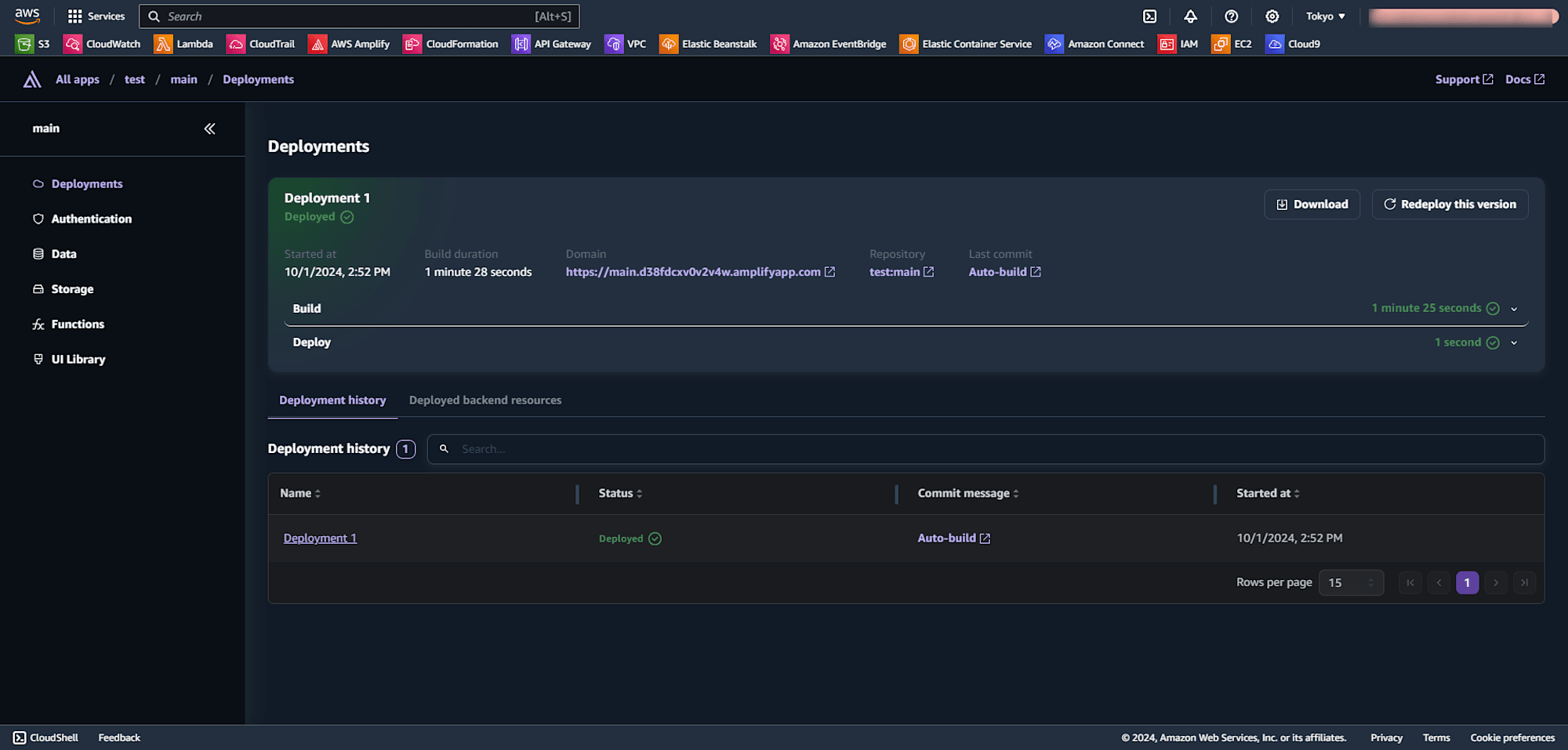
By deploying the Amplify application again from the console, I successfully created the application.
The IAM policy and IAM role were also created and associated with the application.