
ダウンロードした RDS の証明書バンドルを利用できない場合の対処方法
困っていた内容
下記 AWS ドキュメント記載のリンクから入手したルート CA 証明書をアプリケーションへ配置しましたが、「証明書が無効」とのエラーが発生して SSL/TLS 接続ができません。
アプリケーションが参照するトラストストアの設定以外で、見直す場所や何か良い方法があれば教えてください。
回答
AWS リージョンごとの証明書バンドルをダウンロードした場合、バンドルには 3 つの証明機関のルート CA 証明書が含まれています。
- rds-ca-rsa2048-g1
- rds-ca-rsa4096-g1
- rds-ca-ecc384-g1
RDS で利用している認証機関のルート CA 証明書のみを切り出したファイルを配置して、SSL/TLS 接続が可能かお試しください。
やってみた
1. AWS ドキュメント記載のリンクより ap-northeast-1-bundle.pem をダウンロード
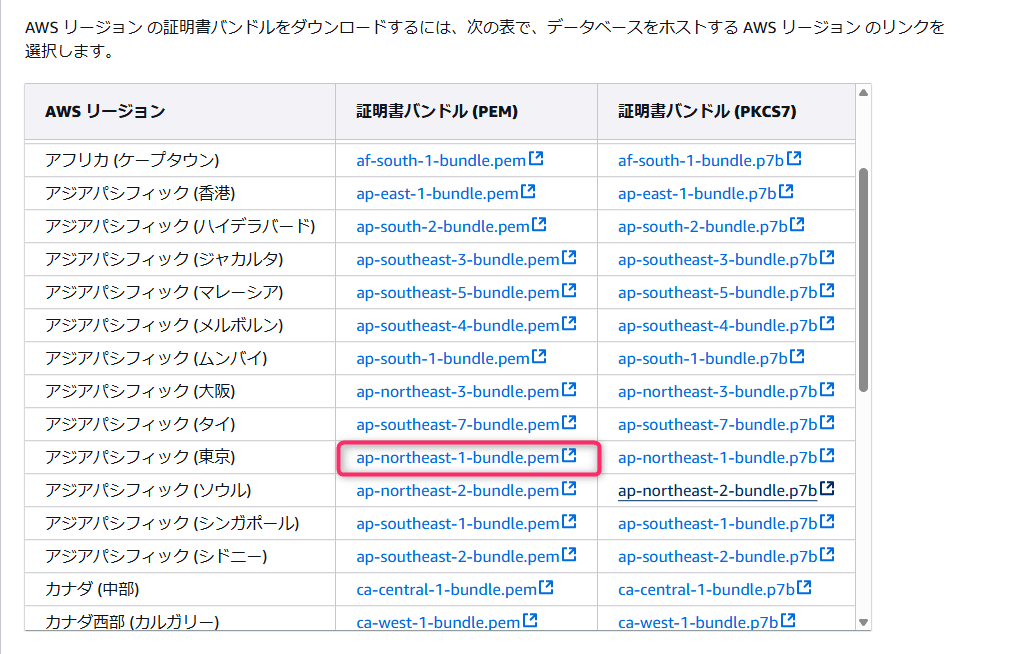
2. pem ファイルから RDS で利用している認証機関のルート CA 証明書のみを切り出す
ダウンロードした pem ファイルをテキストエディタで開いてみると 3 つの証明書がバンドルされていることが分かります。
-----BEGIN CERTIFICATE-----
MIIGCTCCA/GgAwIBAgIRAOXxJuyXVkbfhZCkS/dOpfEwDQYJKoZIhvcNAQEMBQAw
gZwxCzAJBgNVBAYTAlVTMSIwIAYDVQQKDBlBbWF6b24gV2ViIFNlcnZpY2VzLCBJ
bmMuMRMwEQYDVQQLDApBbWF6b24gUkRTMQswCQYDVQQIDAJXQTE1MDMGA1UEAwws
QW1hem9uIFJEUyBhcC1ub3J0aGVhc3QtMSBSb290IENBIFJTQTQwOTYgRzExEDAO
BgNVBAcMB1NlYXR0bGUwIBcNMjEwNTI1MjE1OTEwWhgPMjEyMTA1MjUyMjU5MTBa
MIGcMQswCQYDVQQGEwJVUzEiMCAGA1UECgwZQW1hem9uIFdlYiBTZXJ2aWNlcywg
SW5jLjETMBEGA1UECwwKQW1hem9uIFJEUzELMAkGA1UECAwCV0ExNTAzBgNVBAMM
LEFtYXpvbiBSRFMgYXAtbm9ydGhlYXN0LTEgUm9vdCBDQSBSU0E0MDk2IEcxMRAw
DgYDVQQHDAdTZWF0dGxlMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA
xiP4RDYm4tIS12hGgn1csfO8onQDmK5SZDswUpl0HIKXOUVVWkHNlINkVxbdqpqH
FhbyZmNN6F/EWopotMDKe1B+NLrjNQf4zefv2vyKvPHJXhxoKmfyuTd5Wk8k1F7I
lNwLQzznB+ElhrLIDJl9Ro8t31YBBNFRGAGEnxyACFGcdkjlsa52UwfYrwreEg2l
gW5AzqHgjFfj9QRLydeU/n4bHm0F1adMsV7P3rVwilcUlqsENDwXnWyPEyv3sw6F
wNemLEs1129mB77fwvySb+lLNGsnzr8w4wdioZ74co+T9z2ca+eUiP+EQccVw1Is
D4Fh57IjPa6Wuc4mwiUYKkKY63+38aCfEWb0Qoi+zW+mE9nek6MOQ914cN12u5LX
dBoYopphRO5YmubSN4xcBy405nIdSdbrAVWwxXnVVyjqjknmNeqQsPZaxAhdoKhV
AqxNr8AUAdOAO6Sz3MslmcLlDXFihrEEOeUbpg/m1mSUUHGbu966ajTG1FuEHHwS
7WB52yxoJo/tHvt9nAWnh3uH5BHmS8zn6s6CGweWKbX5yICnZ1QFR1e4pogxX39v
XD6YcNOO+Vn+HY4nXmjgSYVC7l+eeP8eduMg1xJujzjrbmrXU+d+cBObgdTOAlpa
JFHaGwYw1osAwPCo9cZ2f04yitBfj9aPFia8ASKldakCAwEAAaNCMEAwDwYDVR0T
AQH/BAUwAwEB/zAdBgNVHQ4EFgQUqKS+ltlior0SyZKYAkJ/efv55towDgYDVR0P
AQH/BAQDAgGGMA0GCSqGSIb3DQEBDAUAA4ICAQAdElvp8bW4B+Cv+1WSN87dg6TN
wGyIjJ14/QYURgyrZiYpUmZpj+/pJmprSWXu4KNyqHftmaidu7cdjL5nCAvAfnY5
/6eDDbX4j8Gt9fb/6H9y0O0dn3mUPSEKG0crR+JRFAtPhn/2FNvst2P82yguWLv0
pHjHVUVcq+HqDMtUIJsTPYjSh9Iy77Q6TOZKln9dyDOWJpCSkiUWQtMAKbCSlvzd
zTs/ahqpT+zLfGR1SR+T3snZHgQnbnemmz/XtlKl52NxccARwfcEEKaCRQyGq/pR
0PVZasyJS9JY4JfQs4YOdeOt4UMZ8BmW1+BQWGSkkb0QIRl8CszoKofucAlqdPcO
IT/ZaMVhI580LFGWiQIizWFskX6lqbCyHqJB3LDl8gJISB5vNTHOHpvpMOMs5PYt
cRl5Mrksx5MKMqG7y5R734nMlZxQIHjL5FOoOxTBp9KeWIL/Ib89T2QDaLw1SQ+w
ihqWBJ4ZdrIMWYpP3WqM+MXWk7WAem+xsFJdR+MDgOOuobVQTy5dGBlPks/6gpjm
rO9TjfQ36ppJ3b7LdKUPeRfnYmlR5RU4oyYJ//uLbClI443RZAgxaCXX/nyc12lr
eVLUMNF2abLX4/VF63m2/Z9ACgMRfqGshPssn1NN33OonrotQoj4S3N9ZrjvzKt8
iHcaqd60QKpfiH2A3A==
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIICuDCCAj2gAwIBAgIQPaVGRuu86nh/ylZVCLB0MzAKBggqhkjOPQQDAzCBmzEL
MAkGA1UEBhMCVVMxIjAgBgNVBAoMGUFtYXpvbiBXZWIgU2VydmljZXMsIEluYy4x
EzARBgNVBAsMCkFtYXpvbiBSRFMxCzAJBgNVBAgMAldBMTQwMgYDVQQDDCtBbWF6
b24gUkRTIGFwLW5vcnRoZWFzdC0xIFJvb3QgQ0EgRUNDMzg0IEcxMRAwDgYDVQQH
DAdTZWF0dGxlMCAXDTIxMDUyNTIyMDMxNloYDzIxMjEwNTI1MjMwMzE2WjCBmzEL
MAkGA1UEBhMCVVMxIjAgBgNVBAoMGUFtYXpvbiBXZWIgU2VydmljZXMsIEluYy4x
EzARBgNVBAsMCkFtYXpvbiBSRFMxCzAJBgNVBAgMAldBMTQwMgYDVQQDDCtBbWF6
b24gUkRTIGFwLW5vcnRoZWFzdC0xIFJvb3QgQ0EgRUNDMzg0IEcxMRAwDgYDVQQH
DAdTZWF0dGxlMHYwEAYHKoZIzj0CAQYFK4EEACIDYgAEexNURoB9KE93MEtEAlJG
obz4LS/pD2hc8Gczix1WhVvpJ8bN5zCDXaKdnDMCebetyRQsmQ2LYlfmCwpZwSDu
0zowB11Pt3I5Avu2EEcuKTlKIDMBeZ1WWuOd3Tf7MEAMo0IwQDAPBgNVHRMBAf8E
BTADAQH/MB0GA1UdDgQWBBSaYbZPBvFLikSAjpa8mRJvyArMxzAOBgNVHQ8BAf8E
BAMCAYYwCgYIKoZIzj0EAwMDaQAwZgIxAOEJkuh3Zjb7Ih/zuNRd1RBqmIYcnyw0
nwUZczKXry+9XebYj3VQxSRNadrarPWVqgIxAMg1dyGoDAYjY/L/9YElyMnvHltO
PwpJShmqHvCLc/mXMgjjYb/akK7yGthvW6j/uQ==
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIECTCCAvGgAwIBAgIRAIbsx8XOl0sgTNiCN4O+18QwDQYJKoZIhvcNAQELBQAw
gZwxCzAJBgNVBAYTAlVTMSIwIAYDVQQKDBlBbWF6b24gV2ViIFNlcnZpY2VzLCBJ
bmMuMRMwEQYDVQQLDApBbWF6b24gUkRTMQswCQYDVQQIDAJXQTE1MDMGA1UEAwws
QW1hem9uIFJEUyBhcC1ub3J0aGVhc3QtMSBSb290IENBIFJTQTIwNDggRzExEDAO
BgNVBAcMB1NlYXR0bGUwIBcNMjEwNTI1MjE1NDU4WhgPMjA2MTA1MjUyMjU0NTha
MIGcMQswCQYDVQQGEwJVUzEiMCAGA1UECgwZQW1hem9uIFdlYiBTZXJ2aWNlcywg
SW5jLjETMBEGA1UECwwKQW1hem9uIFJEUzELMAkGA1UECAwCV0ExNTAzBgNVBAMM
LEFtYXpvbiBSRFMgYXAtbm9ydGhlYXN0LTEgUm9vdCBDQSBSU0EyMDQ4IEcxMRAw
DgYDVQQHDAdTZWF0dGxlMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA
tROxwXWCgn5R9gI/2Ivjzaxc0g95ysBjoJsnhPdJEHQb7w3y2kWrVWU3Y9fOitgb
CEsnEC3PrhRnzNVW0fPsK6kbvOeCmjvY30rdbxbc8h+bjXfGmIOgAkmoULEr6Hc7
G1Q/+tvv4lEwIs7bEaf+abSZxRJbZ0MBxhbHn7UHHDiMZYvzK+SV1MGCxx7JVhrm
xWu3GC1zZCsGDhB9YqY9eR6PmjbqA5wy8vqbC57dZZa1QVtWIQn3JaRXn+faIzHx
nLMN5CEWihsdmHBXhnRboXprE/OS4MFv1UrQF/XM/h5RBeCywpHePpC+Oe1T3LNC
iP8KzRFrjC1MX/WXJnmOVQIDAQABo0IwQDAPBgNVHRMBAf8EBTADAQH/MB0GA1Ud
DgQWBBS33XbXAUMs1znyZo4B0+B3D68WFTAOBgNVHQ8BAf8EBAMCAYYwDQYJKoZI
hvcNAQELBQADggEBADuadd2EmlpueY2VlrIIPC30QkoA1EOSoCmZgN6124apkoY1
HiV4r+QNPljN4WP8gmcARnNkS7ZeR4fvWi8xPh5AxQCpiaBMw4gcbTMCuKDV68Pw
P2dZCTMspvR3CDfM35oXCufdtFnxyU6PAyINUqF/wyTHguO3owRFPz64+sk3r2pT
WHmJjG9E7V+KOh0s6REgD17Gqn6C5ijLchSrPUHB0wOIkeLJZndHxN/76h7+zhMt
fFeNxPWHY2MfpcaLjz4UREzZPSB2U9k+y3pW1omCIcl6MQU9itGx/LpQE+H3ZeX2
M2bdYd5L+ow+bdbGtsVKOuN+R9Dm17YpswF+vyQ=
-----END CERTIFICATE-----
とりあえず、一つ目の証明書のみを切り出した pem ファイルを作成して保存します。
-----BEGIN CERTIFICATE-----
MIIGCTCCA/GgAwIBAgIRAOXxJuyXVkbfhZCkS/dOpfEwDQYJKoZIhvcNAQEMBQAw
gZwxCzAJBgNVBAYTAlVTMSIwIAYDVQQKDBlBbWF6b24gV2ViIFNlcnZpY2VzLCBJ
bmMuMRMwEQYDVQQLDApBbWF6b24gUkRTMQswCQYDVQQIDAJXQTE1MDMGA1UEAwws
QW1hem9uIFJEUyBhcC1ub3J0aGVhc3QtMSBSb290IENBIFJTQTQwOTYgRzExEDAO
BgNVBAcMB1NlYXR0bGUwIBcNMjEwNTI1MjE1OTEwWhgPMjEyMTA1MjUyMjU5MTBa
MIGcMQswCQYDVQQGEwJVUzEiMCAGA1UECgwZQW1hem9uIFdlYiBTZXJ2aWNlcywg
SW5jLjETMBEGA1UECwwKQW1hem9uIFJEUzELMAkGA1UECAwCV0ExNTAzBgNVBAMM
LEFtYXpvbiBSRFMgYXAtbm9ydGhlYXN0LTEgUm9vdCBDQSBSU0E0MDk2IEcxMRAw
DgYDVQQHDAdTZWF0dGxlMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA
xiP4RDYm4tIS12hGgn1csfO8onQDmK5SZDswUpl0HIKXOUVVWkHNlINkVxbdqpqH
FhbyZmNN6F/EWopotMDKe1B+NLrjNQf4zefv2vyKvPHJXhxoKmfyuTd5Wk8k1F7I
lNwLQzznB+ElhrLIDJl9Ro8t31YBBNFRGAGEnxyACFGcdkjlsa52UwfYrwreEg2l
gW5AzqHgjFfj9QRLydeU/n4bHm0F1adMsV7P3rVwilcUlqsENDwXnWyPEyv3sw6F
wNemLEs1129mB77fwvySb+lLNGsnzr8w4wdioZ74co+T9z2ca+eUiP+EQccVw1Is
D4Fh57IjPa6Wuc4mwiUYKkKY63+38aCfEWb0Qoi+zW+mE9nek6MOQ914cN12u5LX
dBoYopphRO5YmubSN4xcBy405nIdSdbrAVWwxXnVVyjqjknmNeqQsPZaxAhdoKhV
AqxNr8AUAdOAO6Sz3MslmcLlDXFihrEEOeUbpg/m1mSUUHGbu966ajTG1FuEHHwS
7WB52yxoJo/tHvt9nAWnh3uH5BHmS8zn6s6CGweWKbX5yICnZ1QFR1e4pogxX39v
XD6YcNOO+Vn+HY4nXmjgSYVC7l+eeP8eduMg1xJujzjrbmrXU+d+cBObgdTOAlpa
JFHaGwYw1osAwPCo9cZ2f04yitBfj9aPFia8ASKldakCAwEAAaNCMEAwDwYDVR0T
AQH/BAUwAwEB/zAdBgNVHQ4EFgQUqKS+ltlior0SyZKYAkJ/efv55towDgYDVR0P
AQH/BAQDAgGGMA0GCSqGSIb3DQEBDAUAA4ICAQAdElvp8bW4B+Cv+1WSN87dg6TN
wGyIjJ14/QYURgyrZiYpUmZpj+/pJmprSWXu4KNyqHftmaidu7cdjL5nCAvAfnY5
/6eDDbX4j8Gt9fb/6H9y0O0dn3mUPSEKG0crR+JRFAtPhn/2FNvst2P82yguWLv0
pHjHVUVcq+HqDMtUIJsTPYjSh9Iy77Q6TOZKln9dyDOWJpCSkiUWQtMAKbCSlvzd
zTs/ahqpT+zLfGR1SR+T3snZHgQnbnemmz/XtlKl52NxccARwfcEEKaCRQyGq/pR
0PVZasyJS9JY4JfQs4YOdeOt4UMZ8BmW1+BQWGSkkb0QIRl8CszoKofucAlqdPcO
IT/ZaMVhI580LFGWiQIizWFskX6lqbCyHqJB3LDl8gJISB5vNTHOHpvpMOMs5PYt
cRl5Mrksx5MKMqG7y5R734nMlZxQIHjL5FOoOxTBp9KeWIL/Ib89T2QDaLw1SQ+w
ihqWBJ4ZdrIMWYpP3WqM+MXWk7WAem+xsFJdR+MDgOOuobVQTy5dGBlPks/6gpjm
rO9TjfQ36ppJ3b7LdKUPeRfnYmlR5RU4oyYJ//uLbClI443RZAgxaCXX/nyc12lr
eVLUMNF2abLX4/VF63m2/Z9ACgMRfqGshPssn1NN33OonrotQoj4S3N9ZrjvzKt8
iHcaqd60QKpfiH2A3A==
-----END CERTIFICATE-----
3 つの認証機関 rds-ca-rsa2048-g1、rds-ca-rsa4096-g1、rds-ca-ecc384-g1 の内、どの認証機関のルート CA 証明書かを OpenSSL コマンドを利用して確認します。
$ openssl x509 -in first.pem -text -noout
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
e5:f1:26:ec:97:56:46:df:85:90:a4:4b:f7:4e:a5:f1
> Signature Algorithm: sha384WithRSAEncryption
> Issuer: C = US, O = "Amazon Web Services, Inc.", OU = Amazon RDS, ST = WA, CN = Amazon RDS ap-northeast-1 Root CA RSA4096 G1, L = Seattle
Validity
Not Before: May 25 21:59:10 2021 GMT
Not After : May 25 22:59:10 2121 GMT
Subject: C = US, O = "Amazon Web Services, Inc.", OU = Amazon RDS, ST = WA, CN = Amazon RDS ap-northeast-1 Root CA RSA4096 G1, L = Seattle
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (4096 bit)
Modulus:
00:c6:23:f8:44:36:26:e2:d2:12:d7:68:46:82:7d:
5c:b1:f3:bc:a2:74:03:98:ae:52:64:3b:30:52:99:
74:1c:82:97:39:45:55:5a:41:cd:94:83:64:57:16:
dd:aa:9a:87:16:16:f2:66:63:4d:e8:5f:c4:5a:8a:
68:b4:c0:ca:7b:50:7e:34:ba:e3:35:07:f8:cd:e7:
ef:da:fc:8a:bc:f1:c9:5e:1c:68:2a:67:f2:b9:37:
79:5a:4f:24:d4:5e:c8:94:dc:0b:43:3c:e7:07:e1:
25:86:b2:c8:0c:99:7d:46:8f:2d:df:56:01:04:d1:
51:18:01:84:9f:1c:80:08:51:9c:76:48:e5:b1:ae:
76:53:07:d8:af:0a:de:12:0d:a5:81:6e:40:ce:a1:
e0:8c:57:e3:f5:04:4b:c9:d7:94:fe:7e:1b:1e:6d:
05:d5:a7:4c:b1:5e:cf:de:b5:70:8a:57:14:96:ab:
04:34:3c:17:9d:6c:8f:13:2b:f7:b3:0e:85:c0:d7:
a6:2c:4b:35:d7:6f:66:07:be:df:c2:fc:92:6f:e9:
4b:34:6b:27:ce:bf:30:e3:07:62:a1:9e:f8:72:8f:
93:f7:3d:9c:6b:e7:94:88:ff:84:41:c7:15:c3:52:
2c:0f:81:61:e7:b2:23:3d:ae:96:b9:ce:26:c2:25:
18:2a:42:98:eb:7f:b7:f1:a0:9f:11:66:f4:42:88:
be:cd:6f:a6:13:d9:de:93:a3:0e:43:dd:78:70:dd:
76:bb:92:d7:74:1a:18:a2:9a:61:44:ee:58:9a:e6:
d2:37:8c:5c:07:2e:34:e6:72:1d:49:d6:eb:01:55:
b0:c5:79:d5:57:28:ea:8e:49:e6:35:ea:90:b0:f6:
5a:c4:08:5d:a0:a8:55:02:ac:4d:af:c0:14:01:d3:
80:3b:a4:b3:dc:cb:25:99:c2:e5:0d:71:62:86:b1:
04:39:e5:1b:a6:0f:e6:d6:64:94:50:71:9b:bb:de:
ba:6a:34:c6:d4:5b:84:1c:7c:12:ed:60:79:db:2c:
68:26:8f:ed:1e:fb:7d:9c:05:a7:87:7b:87:e4:11:
e6:4b:cc:e7:ea:ce:82:1b:07:96:29:b5:f9:c8:80:
a7:67:54:05:47:57:b8:a6:88:31:5f:7f:6f:5c:3e:
98:70:d3:8e:f9:59:fe:1d:8e:27:5e:68:e0:49:85:
42:ee:5f:9e:78:ff:1e:76:e3:20:d7:12:6e:8f:38:
eb:6e:6a:d7:53:e7:7e:70:13:9b:81:d4:ce:02:5a:
5a:24:51:da:1b:06:30:d6:8b:00:c0:f0:a8:f5:c6:
76:7f:4e:32:8a:d0:5f:8f:d6:8f:16:26:bc:01:22:
a5:75:a9
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Subject Key Identifier:
A8:A4:BE:96:D9:62:A2:BD:12:C9:92:98:02:42:7F:79:FB:F9:E6:DA
X509v3 Key Usage: critical
Digital Signature, Certificate Sign, CRL Sign
Signature Algorithm: sha384WithRSAEncryption
Signature Value:
1d:12:5b:e9:f1:b5:b8:07:e0:af:fb:55:92:37:ce:dd:83:a4:
cd:c0:6c:88:8c:9d:78:fd:06:14:46:0c:ab:66:26:29:52:66:
69:8f:ef:e9:26:6a:6b:49:65:ee:e0:a3:72:a8:77:ed:99:a8:
9d:bb:b7:1d:8c:be:67:08:0b:c0:7e:76:39:ff:a7:83:0d:b5:
f8:8f:c1:ad:f5:f6:ff:e8:7f:72:d0:ed:1d:9f:79:94:3d:21:
0a:1b:47:2b:47:e2:51:14:0b:4f:86:7f:f6:14:db:ec:b7:63:
fc:db:28:2e:58:bb:f4:a4:78:c7:55:45:5c:ab:e1:ea:0c:cb:
54:20:9b:13:3d:88:d2:87:d2:32:ef:b4:3a:4c:e6:4a:96:7f:
5d:c8:33:96:26:90:92:92:25:16:42:d3:00:29:b0:92:96:fc:
dd:cd:3b:3f:6a:1a:a9:4f:ec:cb:7c:64:75:49:1f:93:de:c9:
d9:1e:04:27:6e:77:a6:9b:3f:d7:b6:52:a5:e7:63:71:71:c0:
11:c1:f7:04:10:a6:82:45:0c:86:ab:fa:51:d0:f5:59:6a:cc:
89:4b:d2:58:e0:97:d0:b3:86:0e:75:e3:ad:e1:43:19:f0:19:
96:d7:e0:50:58:64:a4:91:bd:10:21:19:7c:0a:cc:e8:2a:87:
ee:70:09:6a:74:f7:0e:21:3f:d9:68:c5:61:23:9f:34:2c:51:
96:89:02:22:cd:61:6c:91:7e:a5:a9:b0:b2:1e:a2:41:dc:b0:
e5:f2:02:48:48:1e:6f:35:31:ce:1e:9b:e9:30:e3:2c:e4:f6:
2d:71:19:79:32:b9:2c:c7:93:0a:32:a1:bb:cb:94:7b:df:89:
cc:95:9c:50:20:78:cb:e4:53:a8:3b:14:c1:a7:d2:9e:58:82:
ff:21:bf:3d:4f:64:03:68:bc:35:49:0f:b0:8a:1a:96:04:9e:
19:76:b2:0c:59:8a:4f:dd:6a:8c:f8:c5:d6:93:b5:80:7a:6f:
b1:b0:52:5d:47:e3:03:80:e3:ae:a1:b5:50:4f:2e:5d:18:19:
4f:92:cf:fa:82:98:e6:ac:ef:53:8d:f4:37:ea:9a:49:dd:be:
cb:74:a5:0f:79:17:e7:62:69:51:e5:15:38:a3:26:09:ff:fb:
8b:6c:29:48:e3:8d:d1:64:08:31:68:25:d7:fe:7c:9c:d7:69:
6b:79:52:d4:30:d1:76:69:b2:d7:e3:f5:45:eb:79:b6:fd:9f:
40:0a:03:11:7e:a1:ac:84:fb:2c:9f:53:4d:df:73:a8:9e:ba:
2d:42:88:f8:4b:73:7d:66:b8:ef:cc:ab:7c:88:77:1a:a9:de:
b4:40:aa:5f:88:7d:80:dc
コマンド実行結果より、1 つ目の証明書は、認証機関 rds-ca-rsa4096-g1 のルート CA 証明書であることが確認できました。
CN = Amazon RDS ap-northeast-1 Root CA RSA4096 G1
| 認証局 (CA) | 説明 | 共通名 (CN) |
|---|---|---|
| rds-ca-rsa4096-g1 | RSA 4096 プライベートキーアルゴリズムと SHA384 署名アルゴリズムを備えた認証局を使用します。この CA はサーバー証明書の自動ローテーションをサポートします | Amazon RDS region-identifier RSA4096 G1 |
多くても上記の手順を 2 回実施することで、バンドルされている証明書のうち必要なルート CA 証明書を特定することができます。
まとめ
この記事がどなたかのお役に立てば幸いです。









