
「aws-guardrails-XXXXXX」は何なのか?Control Tower 環境に存在する SCP を調査した
コーヒーが好きな emi です。
Control Tower はマルチアカウント管理を楽にしてくれる便利なサービスですが、裏で様々なサービスがセットアップされるため仕組みを理解するのにコツがいるサービスでもあります。
今回は Control Tower をセットアップした際に自動で作成されている「aws-guardrails-」で始まるサービスコントロールポリシー(SCP)について調査したことをメモしておきます。
「aws-guardrails-XXXXXX」の確認方法
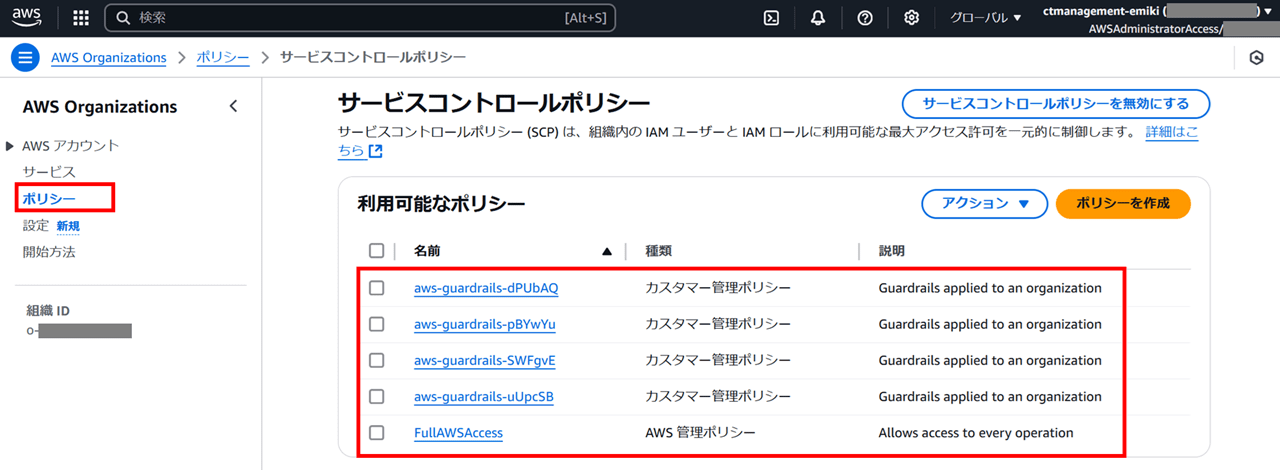
SCP は Organizations コンソールで「ポリシー」を開くと確認できます。
以下のように、「aws-guardrails-XXXXXX」というポリシーが 4 つありました。「FullAWSAccess」は AWS 側で作成されるポリシーで、ユーザー側で編集することができません。
ちなみに Control Tower を有効化している場合は Organizations を直接操作することは少ないかなと思います。Control Tower 側で良きに設定してくれるので、基本は Control Tower 側から操作します。
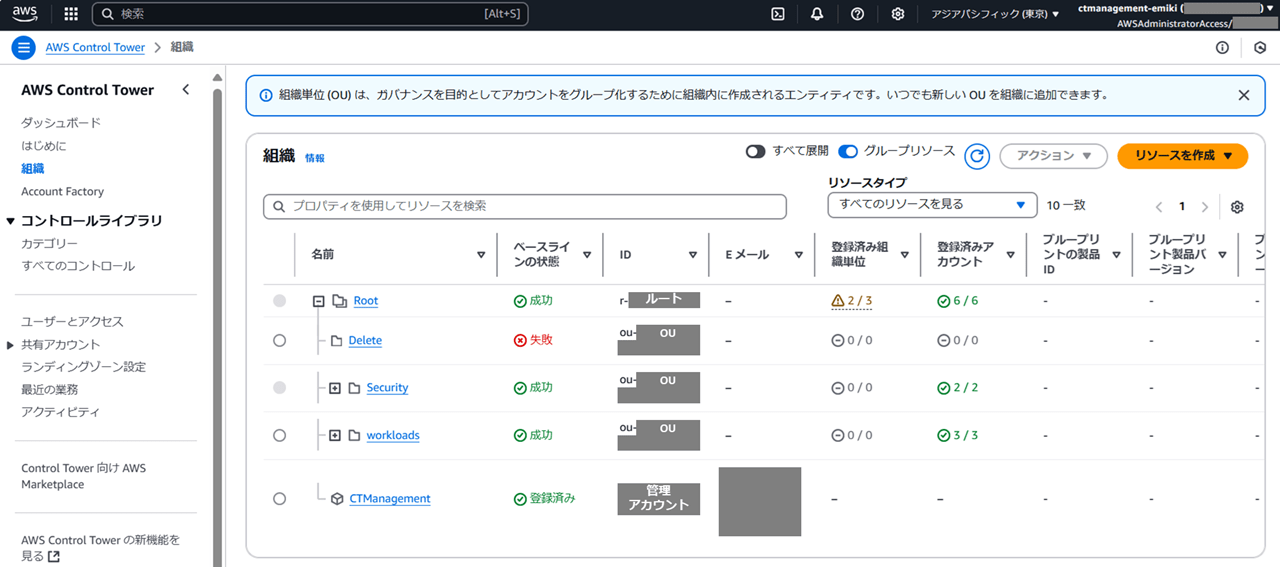
今回は以下のような OU 構成になっています。(Delete OU は削除済みの AWS アカウントを一時的に置いておく用途で作成しているのですが、登録失敗しているのはご愛敬…)
「aws-guardrails-XXXXXX」は何なのか?
「aws-guardrails-xxxxxx」は Control Tower が管理している SCP です。
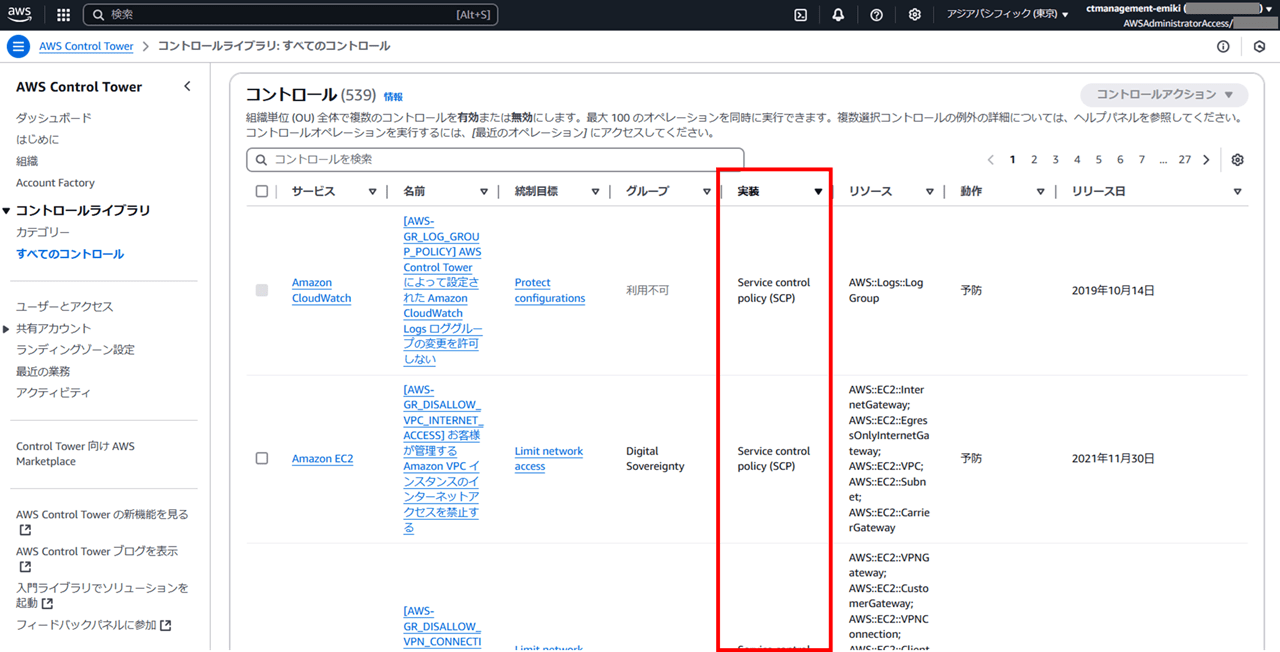
どのような SCP が設定されるのかは以下のコントロールライブラリのドキュメントに記載があります。
Control Tower を有効化した OU に対して、「aws-guardrails-XXXXXX」が基本は 2 つずつアタッチされます。
「基本は」と書いた通り、アタッチされる「aws-guardrails-XXXXXX」の数は増減します。 Control Tower 側で OU ごとに有効にするコントロールを増やしたり減らしたり変更すると、これに応じてアタッチされる「aws-guardrails-XXXXXX」の数は増減します。
Control Tower のコントロールは実装先がいくつかあり、その中でもサービスコントロールポリシー(SCP)となっているものを有効化すると、裏側では SCP 「aws-guardrails-XXXXXX」に設定が追記されていきます。
Organizations コンソールで確認
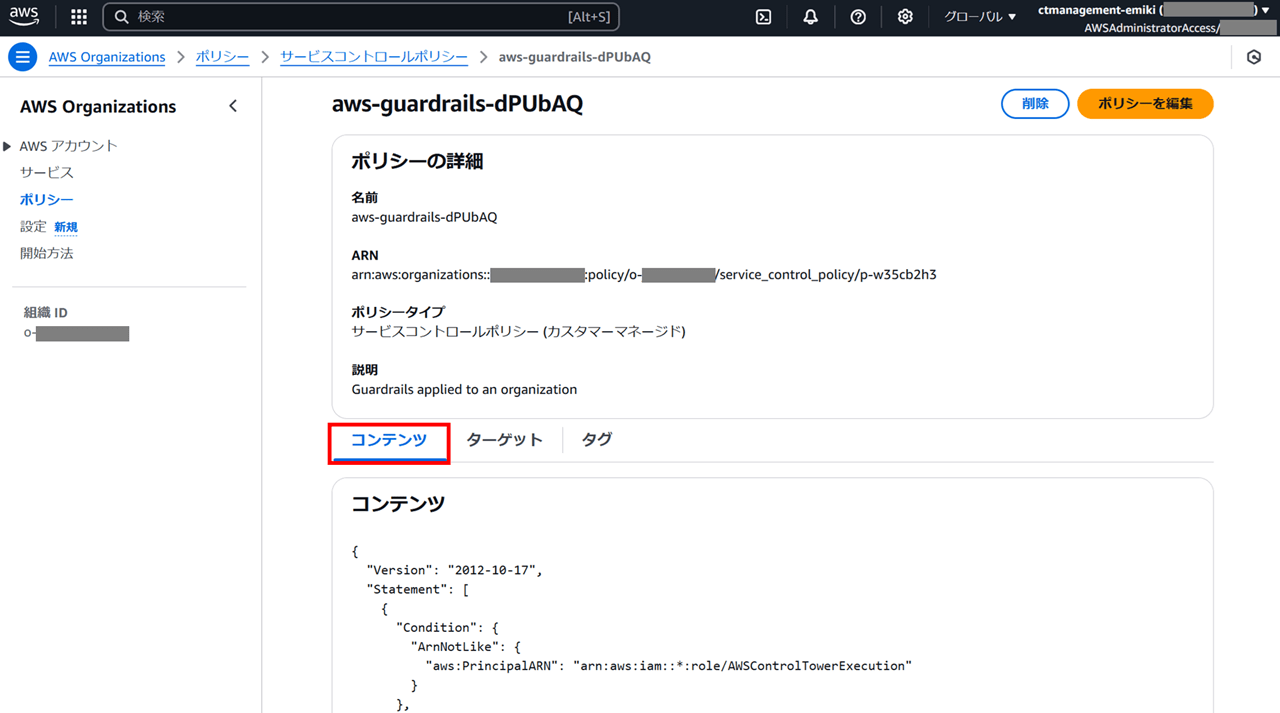
今回 4 つ存在していた SCP 「aws-guardrails-XXXXXX」の中身を見ていきます。
「コンテンツ」タブには、SCP のポリシーが JSON 形式で書かれています。
「ターゲット」タブには、この SCP が適用される適用先が書かれています。
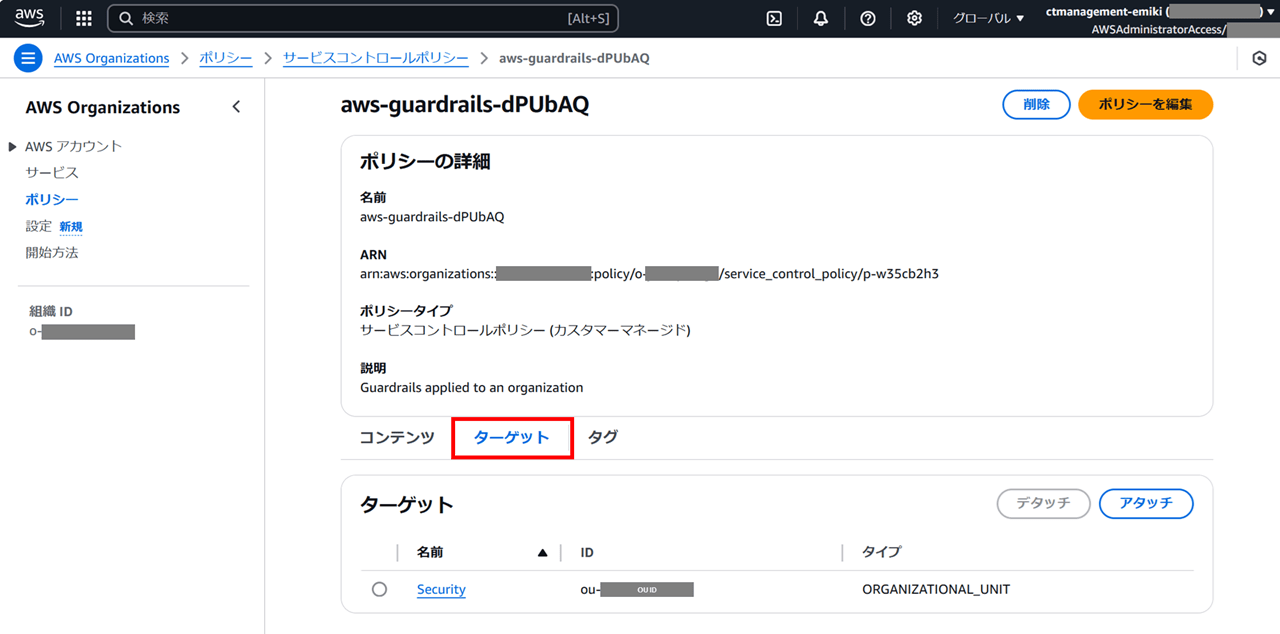
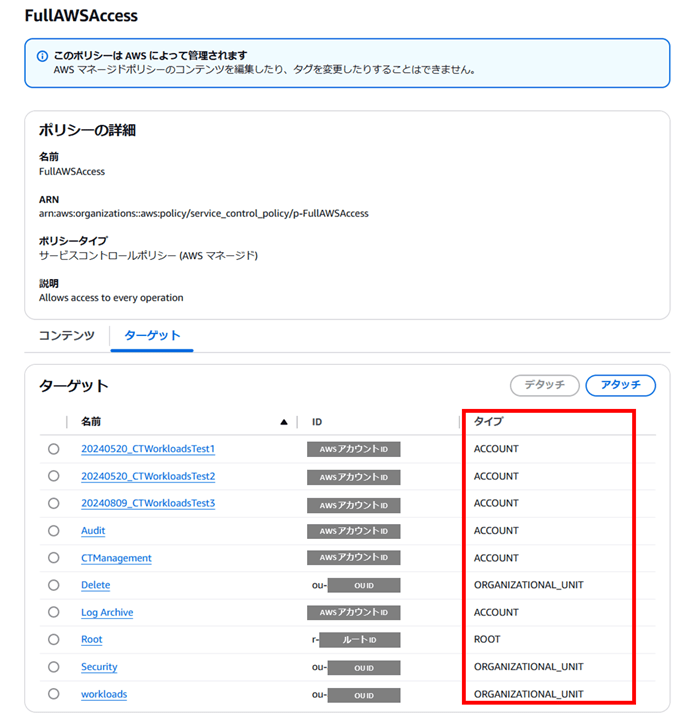
SCP が適用される適用先は「タイプ」で表わされていて、以下 3 種類あります。
- ROOT
- ACCOUNT
- ORGANIZATIONAL_UNIT(OU)
「AWSFullAccess」を開くと全種類確認できて分かりやすいですね。
SCP 「aws-guardrails-XXXXXX」 の JSON テキスト
私の環境で確認できた中身を一応貼ってみますが、この SCP の中身を直接 JSON で読むより Control Tower 側で「有効なコントロール」を確認した方が分かりやすいと思います。有効化するコントロール次第で中身も変わりますしね。
aws-guardrails-dPUbAQ.json
- ターゲット
- ORGANIZATIONAL_UNIT(OU)
- Security
- ORGANIZATIONAL_UNIT(OU)
{
"Version": "2012-10-17",
"Statement": [
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"s3:DeleteBucket"
],
"Resource": [
"arn:aws:s3:::aws-controltower*"
],
"Effect": "Deny",
"Sid": "GRAUDITBUCKETDELETIONPROHIBITED"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"cloudtrail:DeleteTrail",
"cloudtrail:PutEventSelectors",
"cloudtrail:StopLogging",
"cloudtrail:UpdateTrail"
],
"Resource": [
"arn:aws:cloudtrail:*:*:trail/aws-controltower-*"
],
"Effect": "Deny",
"Sid": "GRCLOUDTRAILENABLED"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"events:PutRule",
"events:PutTargets",
"events:RemoveTargets",
"events:DisableRule",
"events:DeleteRule"
],
"Resource": [
"arn:aws:events:*:*:rule/aws-controltower-*"
],
"Effect": "Deny",
"Sid": "GRCLOUDWATCHEVENTPOLICY"
},
{
"Condition": {
"StringLike": {
"aws:ResourceTag/aws-control-tower": "managed-by-control-tower"
},
"ArnNotLike": {
"aws:PrincipalArn": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"config:DeleteAggregationAuthorization"
],
"Resource": [
"arn:aws:config:*:*:aggregation-authorization*"
],
"Effect": "Deny",
"Sid": "GRCONFIGAGGREGATIONAUTHORIZATIONPOLICY"
},
{
"Condition": {
"ForAllValues:StringEquals": {
"aws:TagKeys": "aws-control-tower"
},
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"config:TagResource",
"config:UntagResource"
],
"Resource": [
"*"
],
"Effect": "Deny",
"Sid": "GRCONFIGRULETAGSPOLICY"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"config:DeleteConfigurationRecorder",
"config:DeleteDeliveryChannel",
"config:DeleteRetentionConfiguration",
"config:PutConfigurationRecorder",
"config:PutDeliveryChannel",
"config:PutRetentionConfiguration",
"config:StopConfigurationRecorder"
],
"Resource": [
"*"
],
"Effect": "Deny",
"Sid": "GRCONFIGENABLED"
},
{
"Condition": {
"StringEquals": {
"aws:ResourceTag/aws-control-tower": "managed-by-control-tower"
},
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"config:PutConfigRule",
"config:DeleteConfigRule",
"config:DeleteEvaluationResults",
"config:DeleteConfigurationAggregator",
"config:PutConfigurationAggregator"
],
"Resource": [
"*"
],
"Effect": "Deny",
"Sid": "GRCONFIGRULEPOLICY"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"s3:PutEncryptionConfiguration"
],
"Resource": [
"arn:aws:s3:::aws-controltower*"
],
"Effect": "Deny",
"Sid": "GRCTAUDITBUCKETENCRYPTIONCHANGESPROHIBITED"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"s3:PutLifecycleConfiguration"
],
"Resource": [
"arn:aws:s3:::aws-controltower*"
],
"Effect": "Deny",
"Sid": "GRCTAUDITBUCKETLIFECYCLECONFIGURATIONCHANGESPROHIBITED"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"s3:PutBucketLogging"
],
"Resource": [
"arn:aws:s3:::aws-controltower*"
],
"Effect": "Deny",
"Sid": "GRCTAUDITBUCKETLOGGINGCONFIGURATIONCHANGESPROHIBITED"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"s3:PutBucketPolicy",
"s3:DeleteBucketPolicy"
],
"Resource": [
"arn:aws:s3:::aws-controltower*"
],
"Effect": "Deny",
"Sid": "GRCTAUDITBUCKETPOLICYCHANGESPROHIBITED"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalArn": [
"arn:aws:iam::*:role/AWSControlTowerExecution",
"arn:aws:iam::*:role/stacksets-exec-*"
]
}
},
"Action": [
"iam:AttachRolePolicy",
"iam:CreateRole",
"iam:DeleteRole",
"iam:DeleteRolePermissionsBoundary",
"iam:DeleteRolePolicy",
"iam:DetachRolePolicy",
"iam:PutRolePermissionsBoundary",
"iam:PutRolePolicy",
"iam:UpdateAssumeRolePolicy",
"iam:UpdateRole",
"iam:UpdateRoleDescription"
],
"Resource": [
"arn:aws:iam::*:role/aws-controltower-*",
"arn:aws:iam::*:role/*AWSControlTower*",
"arn:aws:iam::*:role/stacksets-exec-*"
],
"Effect": "Deny",
"Sid": "GRIAMROLEPOLICY"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"lambda:AddPermission",
"lambda:CreateEventSourceMapping",
"lambda:CreateFunction",
"lambda:DeleteEventSourceMapping",
"lambda:DeleteFunction",
"lambda:DeleteFunctionConcurrency",
"lambda:PutFunctionConcurrency",
"lambda:RemovePermission",
"lambda:UpdateEventSourceMapping",
"lambda:UpdateFunctionCode",
"lambda:UpdateFunctionConfiguration"
],
"Resource": [
"arn:aws:lambda:*:*:function:aws-controltower-*"
],
"Effect": "Deny",
"Sid": "GRLAMBDAFUNCTIONPOLICY"
},
{
"Condition": {
"StringNotLike": {
"aws:PrincipalArn": [
"arn:aws:iam::*:role/AWSControlTowerExecution"
]
}
},
"Action": [
"logs:DeleteLogGroup",
"logs:PutRetentionPolicy"
],
"Resource": [
"arn:aws:logs:*:*:log-group:*aws-controltower*"
],
"Effect": "Deny",
"Sid": "GRLOGGROUPPOLICY"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"sns:AddPermission",
"sns:CreateTopic",
"sns:DeleteTopic",
"sns:RemovePermission",
"sns:SetTopicAttributes"
],
"Resource": [
"arn:aws:sns:*:*:aws-controltower-*"
],
"Effect": "Deny",
"Sid": "GRSNSTOPICPOLICY"
}
]
}
aws-guardrails-pBYwYu.json
- ターゲット
- このポリシーは、ルート、組織単位、またはアカウントにはアタッチされません。
{
"Version": "2012-10-17",
"Statement": [
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"cloudtrail:DeleteTrail",
"cloudtrail:PutEventSelectors",
"cloudtrail:StopLogging",
"cloudtrail:UpdateTrail"
],
"Resource": [
"arn:aws:cloudtrail:*:*:trail/aws-controltower-*"
],
"Effect": "Deny",
"Sid": "GRCLOUDTRAILENABLED"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"events:PutRule",
"events:PutTargets",
"events:RemoveTargets",
"events:DisableRule",
"events:DeleteRule"
],
"Resource": [
"arn:aws:events:*:*:rule/aws-controltower-*"
],
"Effect": "Deny",
"Sid": "GRCLOUDWATCHEVENTPOLICY"
},
{
"Condition": {
"StringLike": {
"aws:ResourceTag/aws-control-tower": "managed-by-control-tower"
},
"ArnNotLike": {
"aws:PrincipalArn": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"config:DeleteAggregationAuthorization"
],
"Resource": [
"arn:aws:config:*:*:aggregation-authorization*"
],
"Effect": "Deny",
"Sid": "GRCONFIGAGGREGATIONAUTHORIZATIONPOLICY"
},
{
"Condition": {
"ForAllValues:StringEquals": {
"aws:TagKeys": "aws-control-tower"
},
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"config:TagResource",
"config:UntagResource"
],
"Resource": [
"*"
],
"Effect": "Deny",
"Sid": "GRCONFIGRULETAGSPOLICY"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"config:DeleteConfigurationRecorder",
"config:DeleteDeliveryChannel",
"config:DeleteRetentionConfiguration",
"config:PutConfigurationRecorder",
"config:PutDeliveryChannel",
"config:PutRetentionConfiguration",
"config:StopConfigurationRecorder"
],
"Resource": [
"*"
],
"Effect": "Deny",
"Sid": "GRCONFIGENABLED"
},
{
"Condition": {
"StringEquals": {
"aws:ResourceTag/aws-control-tower": "managed-by-control-tower"
},
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"config:PutConfigRule",
"config:DeleteConfigRule",
"config:DeleteEvaluationResults",
"config:DeleteConfigurationAggregator",
"config:PutConfigurationAggregator"
],
"Resource": [
"*"
],
"Effect": "Deny",
"Sid": "GRCONFIGRULEPOLICY"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalArn": [
"arn:aws:iam::*:role/AWSControlTowerExecution",
"arn:aws:iam::*:role/stacksets-exec-*"
]
}
},
"Action": [
"iam:AttachRolePolicy",
"iam:CreateRole",
"iam:DeleteRole",
"iam:DeleteRolePermissionsBoundary",
"iam:DeleteRolePolicy",
"iam:DetachRolePolicy",
"iam:PutRolePermissionsBoundary",
"iam:PutRolePolicy",
"iam:UpdateAssumeRolePolicy",
"iam:UpdateRole",
"iam:UpdateRoleDescription"
],
"Resource": [
"arn:aws:iam::*:role/aws-controltower-*",
"arn:aws:iam::*:role/*AWSControlTower*",
"arn:aws:iam::*:role/stacksets-exec-*"
],
"Effect": "Deny",
"Sid": "GRIAMROLEPOLICY"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"lambda:AddPermission",
"lambda:CreateEventSourceMapping",
"lambda:CreateFunction",
"lambda:DeleteEventSourceMapping",
"lambda:DeleteFunction",
"lambda:DeleteFunctionConcurrency",
"lambda:PutFunctionConcurrency",
"lambda:RemovePermission",
"lambda:UpdateEventSourceMapping",
"lambda:UpdateFunctionCode",
"lambda:UpdateFunctionConfiguration"
],
"Resource": [
"arn:aws:lambda:*:*:function:aws-controltower-*"
],
"Effect": "Deny",
"Sid": "GRLAMBDAFUNCTIONPOLICY"
},
{
"Condition": {
"StringNotLike": {
"aws:PrincipalArn": [
"arn:aws:iam::*:role/AWSControlTowerExecution"
]
}
},
"Action": [
"logs:DeleteLogGroup",
"logs:PutRetentionPolicy"
],
"Resource": [
"arn:aws:logs:*:*:log-group:*aws-controltower*"
],
"Effect": "Deny",
"Sid": "GRLOGGROUPPOLICY"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"sns:AddPermission",
"sns:CreateTopic",
"sns:DeleteTopic",
"sns:RemovePermission",
"sns:SetTopicAttributes"
],
"Resource": [
"arn:aws:sns:*:*:aws-controltower-*"
],
"Effect": "Deny",
"Sid": "GRSNSTOPICPOLICY"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"sns:Subscribe",
"sns:Unsubscribe"
],
"Resource": [
"arn:aws:sns:*:*:aws-controltower-SecurityNotifications"
],
"Effect": "Deny",
"Sid": "GRSNSSUBSCRIPTIONPOLICY"
}
]
}
aws-guardrails-SWFgvE.json
- ターゲット
- ORGANIZATIONAL_UNIT(OU)
- workloads
- ORGANIZATIONAL_UNIT(OU)
{
"Version": "2012-10-17",
"Statement": [
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"lambda:AddPermission",
"lambda:CreateEventSourceMapping",
"lambda:CreateFunction",
"lambda:DeleteEventSourceMapping",
"lambda:DeleteFunction",
"lambda:DeleteFunctionConcurrency",
"lambda:PutFunctionConcurrency",
"lambda:RemovePermission",
"lambda:UpdateEventSourceMapping",
"lambda:UpdateFunctionCode",
"lambda:UpdateFunctionConfiguration"
],
"Resource": [
"arn:aws:lambda:*:*:function:aws-controltower-*"
],
"Effect": "Deny",
"Sid": "GRLAMBDAFUNCTIONPOLICY"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalArn": [
"arn:aws:iam::*:role/AWSControlTowerExecution",
"arn:aws:iam::*:role/stacksets-exec-*"
]
}
},
"Action": [
"iam:AttachRolePolicy",
"iam:CreateRole",
"iam:DeleteRole",
"iam:DeleteRolePermissionsBoundary",
"iam:DeleteRolePolicy",
"iam:DetachRolePolicy",
"iam:PutRolePermissionsBoundary",
"iam:PutRolePolicy",
"iam:UpdateAssumeRolePolicy",
"iam:UpdateRole",
"iam:UpdateRoleDescription"
],
"Resource": [
"arn:aws:iam::*:role/aws-controltower-*",
"arn:aws:iam::*:role/*AWSControlTower*",
"arn:aws:iam::*:role/stacksets-exec-*"
],
"Effect": "Deny",
"Sid": "GRIAMROLEPOLICY"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"config:DeleteConfigurationRecorder",
"config:DeleteDeliveryChannel",
"config:DeleteRetentionConfiguration",
"config:PutConfigurationRecorder",
"config:PutDeliveryChannel",
"config:PutRetentionConfiguration",
"config:StopConfigurationRecorder"
],
"Resource": [
"*"
],
"Effect": "Deny",
"Sid": "GRCONFIGENABLED"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"sns:Subscribe",
"sns:Unsubscribe"
],
"Resource": [
"arn:aws:sns:*:*:aws-controltower-SecurityNotifications"
],
"Effect": "Deny",
"Sid": "GRSNSSUBSCRIPTIONPOLICY"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"cloudtrail:DeleteTrail",
"cloudtrail:PutEventSelectors",
"cloudtrail:StopLogging",
"cloudtrail:UpdateTrail"
],
"Resource": [
"arn:aws:cloudtrail:*:*:trail/aws-controltower-*"
],
"Effect": "Deny",
"Sid": "GRCLOUDTRAILENABLED"
},
{
"Condition": {
"StringLike": {
"aws:ResourceTag/aws-control-tower": "managed-by-control-tower"
},
"ArnNotLike": {
"aws:PrincipalArn": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"config:DeleteAggregationAuthorization"
],
"Resource": [
"arn:aws:config:*:*:aggregation-authorization*"
],
"Effect": "Deny",
"Sid": "GRCONFIGAGGREGATIONAUTHORIZATIONPOLICY"
},
{
"Condition": {
"ForAnyValue:StringEquals": {
"aws:TagKeys": "aws-control-tower"
},
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"config:TagResource",
"config:UntagResource"
],
"Resource": "*",
"Effect": "Deny",
"Sid": "GRCONFIGRULETAGSPOLICY"
},
{
"Condition": {
"StringEquals": {
"aws:ResourceTag/aws-control-tower": "managed-by-control-tower"
},
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"config:PutConfigRule",
"config:DeleteConfigRule",
"config:DeleteEvaluationResults",
"config:DeleteConfigurationAggregator",
"config:PutConfigurationAggregator"
],
"Resource": [
"*"
],
"Effect": "Deny",
"Sid": "GRCONFIGRULEPOLICY"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"events:PutRule",
"events:PutTargets",
"events:RemoveTargets",
"events:DisableRule",
"events:DeleteRule"
],
"Resource": [
"arn:aws:events:*:*:rule/aws-controltower-*"
],
"Effect": "Deny",
"Sid": "GRCLOUDWATCHEVENTPOLICY"
},
{
"Condition": {
"StringNotLike": {
"aws:PrincipalArn": [
"arn:aws:iam::*:role/AWSControlTowerExecution"
]
}
},
"Action": [
"logs:DeleteLogGroup",
"logs:PutRetentionPolicy"
],
"Resource": [
"arn:aws:logs:*:*:log-group:*aws-controltower*"
],
"Effect": "Deny",
"Sid": "GRLOGGROUPPOLICY"
},
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"sns:AddPermission",
"sns:CreateTopic",
"sns:DeleteTopic",
"sns:RemovePermission",
"sns:SetTopicAttributes"
],
"Resource": [
"arn:aws:sns:*:*:aws-controltower-*"
],
"Effect": "Deny",
"Sid": "GRSNSTOPICPOLICY"
}
]
}
aws-guardrails-uUpcSB.json
- ターゲット
- ORGANIZATIONAL_UNIT(OU)
- Security
- ORGANIZATIONAL_UNIT(OU)
{
"Version": "2012-10-17",
"Statement": [
{
"Condition": {
"ArnNotLike": {
"aws:PrincipalARN": "arn:aws:iam::*:role/AWSControlTowerExecution"
}
},
"Action": [
"sns:Subscribe",
"sns:Unsubscribe"
],
"Resource": [
"arn:aws:sns:*:*:aws-controltower-SecurityNotifications"
],
"Effect": "Deny",
"Sid": "GRSNSSUBSCRIPTIONPOLICY"
}
]
}
FullAWSAccess.json
- ターゲット
- ROOT
- Root
- ACCOUNT
- 20240520_CTWorkloadsTest1
- 20240520_CTWorkloadsTest2
- 20240809_CTWorkloadsTest3
- Audit
- Log Archive
- CTManagement
- ORGANIZATIONAL_UNIT(OU)
- Delete
- Security
- workloads
- ROOT
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*"
}
]
}
おわりに
本記事への質問やご要望については画面下部のお問い合わせ「DevelopersIO について」からご連絡ください。記事に関してお問い合わせいただけます。
参考








