
AWS Backupが作成するデフォルトのロールを使用すると、S3のバックアップ取得時に権限不足でエラーになる
はじめに
AWS BackupのバックプランをS3に割り当てる際、自動的に作成されるデフォルトロールを使用すると権限不足でバックアップが失敗することがあったので、原因と対策を調べてみました。
先に結論
AWS BackupでS3バケットのバックアップを取得するにはAWSBackupServiceRolePolicyForS3BackupとAWSBackupServiceRolePolicyForS3Restoreというポリシーが必要です。
このポリシーはデフォルのロールにはアタッチされていないため、追加でアタッチする必要があります。
リソースの割り当て
今回のエラーを再現するために、マネジメントコンソール画面よりAWS Backupで作成したバックアッププランをS3に割り当てます。
この時、アタッチするIAMロールにデフォルトのロールを選択します。(下図参照)
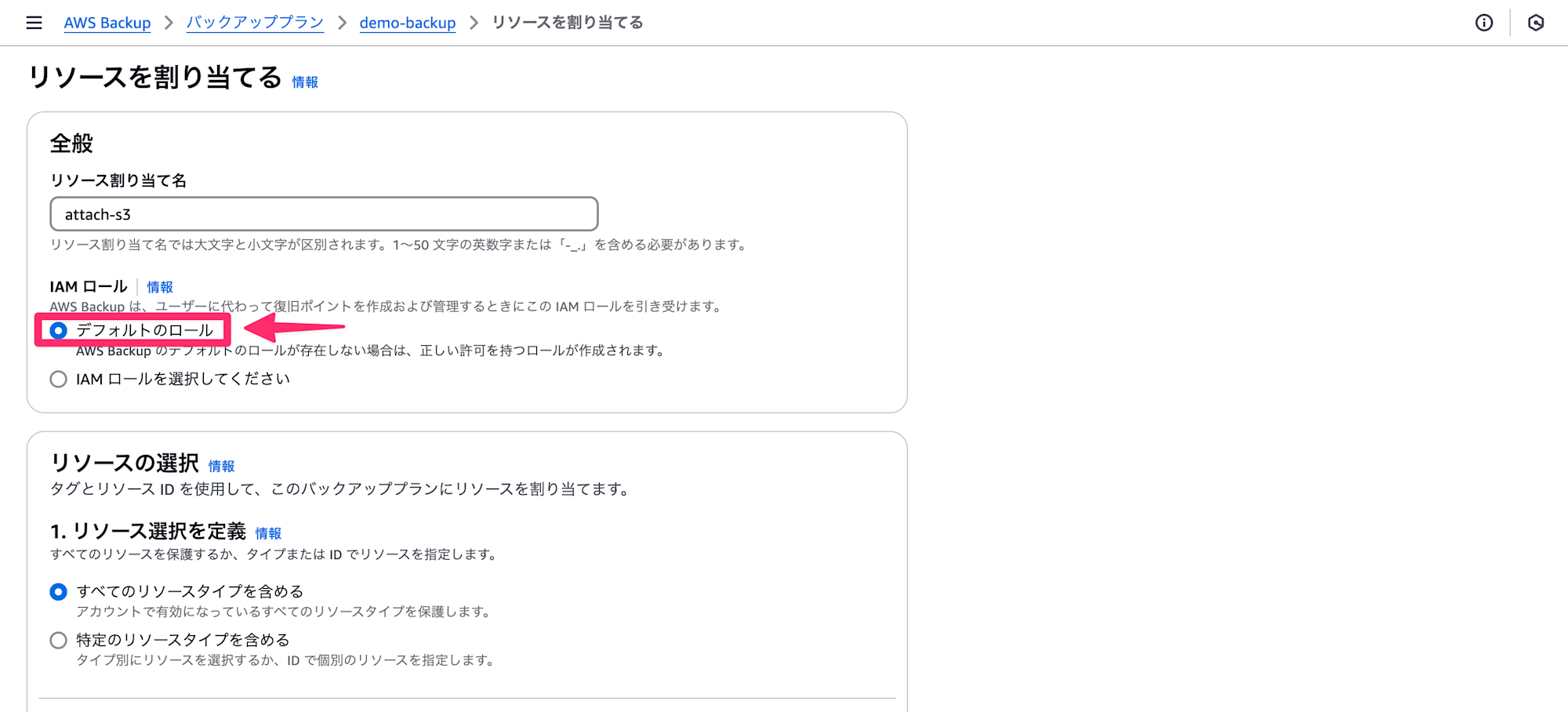
説明文では「AWS Backup のデフォルトのロールが存在しない場合は、正しい許可を持つロールが作成されます。」と書かれています。
ちなみに、この操作を行う際はAWS Backup のデフォルトのロールは存在していません。
発見
S3がバックアップされていることを確認するため、バックアップジョブを確認したところ以下のようにステータスが失敗と表示されていました。
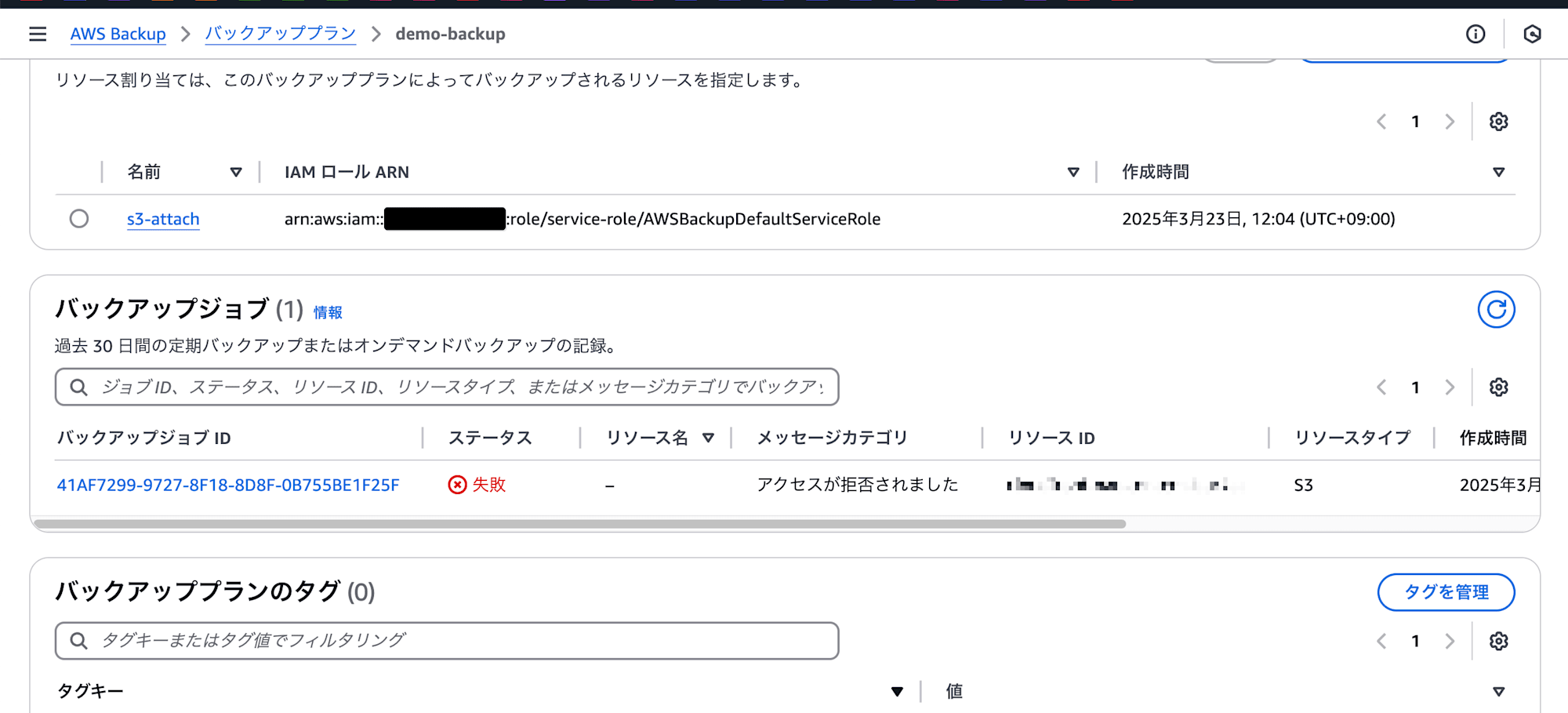
ジョブIDから詳細を確認すると、次のエラーメッセージが表示されていました。
アクセスが拒否されました
Your backup job failed as AWS Backup does not have permission to describe resource arn:aws:s3:::<bucket-name>. Please review your IAM policies to ensure AWS Backup can protect your resources.
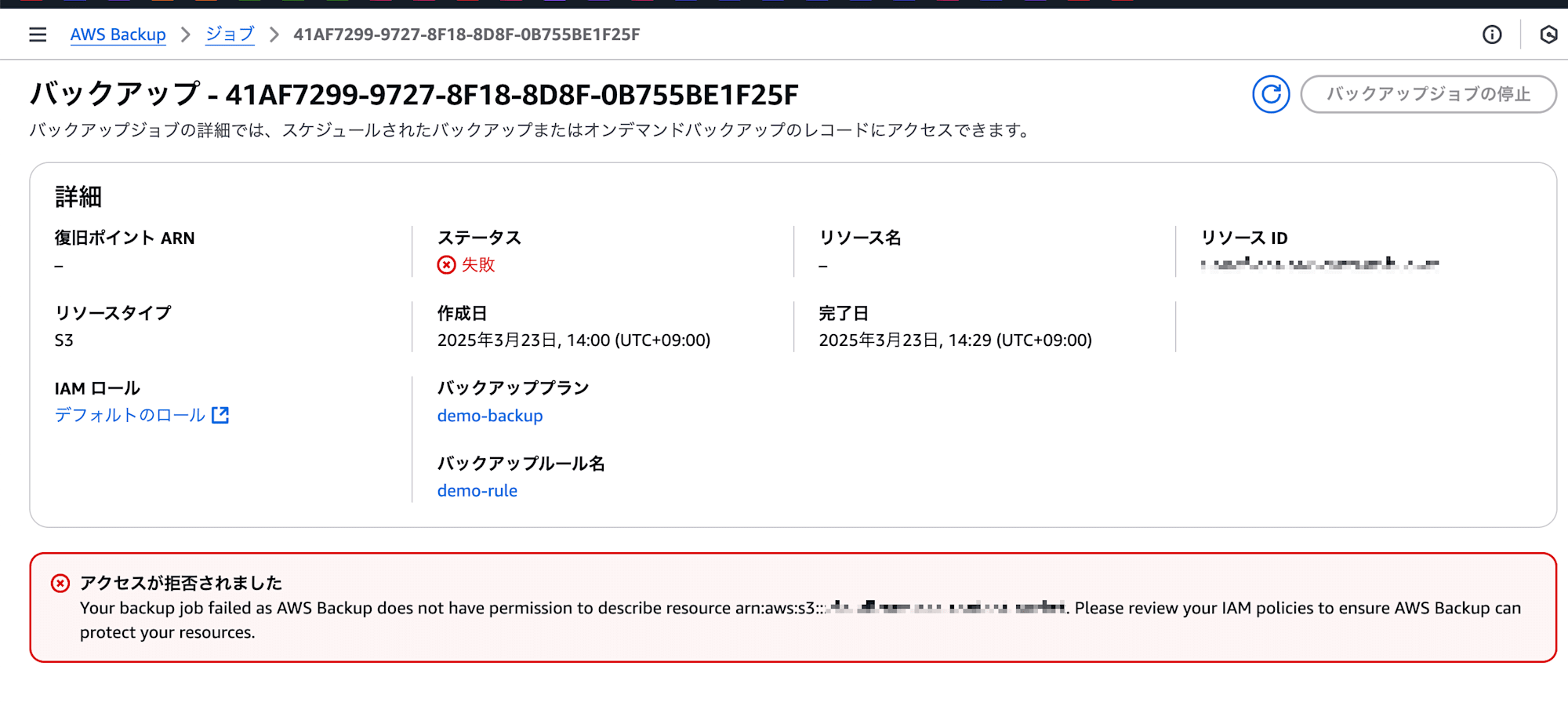
バックアップ対象のS3バケットにアクセスするための権限が不足している旨の内容が書かれています。
ここで、あれ?自動で作成されるロールなのに権限が足りないの?と思いました。
この時、S3バケットのバケットポリシーが必要なのかと考えましたがドキュメントにはそのような記載はなかったのでバケットポリシーは設定していません。
原因
ドキュメントを確認したところ次の記載がありました。
S3 バックアップの前提条件
Amazon S3 のバックアップと復元のアクセス許可とポリシー
S3 リソースをバックアップ、コピー、復元するには、ロールに適切なポリシーが必要です。これらのポリシーを追加するには、「AWS 管理ポリシー」を参照してください。S3 バケットのバックアップと復元に使用するロールに、AWSBackupServiceRolePolicyForS3Backup と AWSBackupServiceRolePolicyForS3Restore を追加します。
参照:S3 バックアップの前提条件
どうやらS3バケットのバックアップを取得するにはAWSBackupServiceRolePolicyForS3BackupとAWSBackupServiceRolePolicyForS3Restoreというポリシーが必要なようです。
念のため、AWS Backupが作成するデフォルトロール(AWSBackupDefaultServiceRole)のポリシーを確認します。
AWSBackupServiceRolePolicyForBackup
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "DynamoDBPermissions",
"Effect": "Allow",
"Action": [
"dynamodb:DescribeTable",
"dynamodb:CreateBackup"
],
"Resource": "arn:aws:dynamodb:*:*:table/*"
},
{
"Sid": "DynamoDBBackupResourcePermissions",
"Effect": "Allow",
"Action": [
"dynamodb:DescribeBackup",
"dynamodb:DeleteBackup"
],
"Resource": "arn:aws:dynamodb:*:*:table/*/backup/*"
},
{
"Sid": "DynamoDBBackupPermissions",
"Effect": "Allow",
"Action": [
"rds:AddTagsToResource",
"rds:ListTagsForResource",
"rds:DescribeDBSnapshots",
"rds:CreateDBSnapshot",
"rds:CopyDBSnapshot",
"rds:DescribeDBInstances",
"rds:CreateDBClusterSnapshot",
"rds:DescribeDBClusters",
"rds:DescribeDBClusterSnapshots",
"rds:CopyDBClusterSnapshot",
"rds:DescribeDBClusterAutomatedBackups"
],
"Resource": "*"
},
{
"Sid": "RDSInstanceAutomatedBackupPermissions",
"Effect": "Allow",
"Action": "rds:DeleteDBInstanceAutomatedBackup",
"Resource": "arn:aws:rds:*:*:auto-backup:*"
},
{
"Sid": "RDSClusterPermissions",
"Effect": "Allow",
"Action": [
"rds:ModifyDBCluster"
],
"Resource": [
"arn:aws:rds:*:*:cluster:*"
]
},
{
"Sid": "RDSClusterBackupPermissions",
"Effect": "Allow",
"Action": "rds:DeleteDBClusterAutomatedBackup",
"Resource": "arn:aws:rds:*:*:cluster-auto-backup:*"
},
{
"Sid": "RDSModifyPermissions",
"Effect": "Allow",
"Action": [
"rds:ModifyDBInstance"
],
"Resource": [
"arn:aws:rds:*:*:db:*"
]
},
{
"Sid": "RDSBackupPermissions",
"Effect": "Allow",
"Action": [
"rds:DeleteDBSnapshot",
"rds:ModifyDBSnapshotAttribute"
],
"Resource": [
"arn:aws:rds:*:*:snapshot:awsbackup:*"
]
},
{
"Sid": "RDSClusterModifyPermissions",
"Effect": "Allow",
"Action": [
"rds:DeleteDBClusterSnapshot",
"rds:ModifyDBClusterSnapshotAttribute"
],
"Resource": [
"arn:aws:rds:*:*:cluster-snapshot:awsbackup:*"
]
},
{
"Sid": "StorageGatewayPermissions",
"Effect": "Allow",
"Action": [
"storagegateway:CreateSnapshot",
"storagegateway:ListTagsForResource"
],
"Resource": "arn:aws:storagegateway:*:*:gateway/*/volume/*"
},
{
"Sid": "EBSCopyPermissions",
"Effect": "Allow",
"Action": [
"ec2:CopySnapshot"
],
"Resource": "arn:aws:ec2:*::snapshot/*"
},
{
"Sid": "EC2CopyPermissions",
"Effect": "Allow",
"Action": [
"ec2:CopyImage"
],
"Resource": "*"
},
{
"Sid": "EBSTagAndDeletePermissions",
"Effect": "Allow",
"Action": [
"ec2:CreateTags",
"ec2:DeleteSnapshot"
],
"Resource": "arn:aws:ec2:*::snapshot/*"
},
{
"Sid": "EC2Permissions",
"Effect": "Allow",
"Action": [
"ec2:CreateImage",
"ec2:DeregisterImage",
"ec2:DescribeSnapshots",
"ec2:DescribeTags",
"ec2:DescribeImages",
"ec2:DescribeInstances",
"ec2:DescribeInstanceAttribute",
"ec2:DescribeInstanceCreditSpecifications",
"ec2:DescribeNetworkInterfaces",
"ec2:DescribeElasticGpus",
"ec2:DescribeSpotInstanceRequests",
"ec2:DescribeSnapshotTierStatus"
],
"Resource": "*"
},
{
"Sid": "EC2TagPermissions",
"Effect": "Allow",
"Action": [
"ec2:CreateTags"
],
"Resource": "arn:aws:ec2:*:*:image/*"
},
{
"Sid": "EC2ModifyPermissions",
"Effect": "Allow",
"Action": [
"ec2:ModifySnapshotAttribute",
"ec2:ModifyImageAttribute"
],
"Resource": "*",
"Condition": {
"Null": {
"aws:ResourceTag/aws:backup:source-resource": "false"
}
}
},
{
"Sid": "EBSSnapshotTierPermissions",
"Effect": "Allow",
"Action": [
"ec2:ModifySnapshotTier"
],
"Resource": "arn:aws:ec2:*::snapshot/*",
"Condition": {
"Null": {
"aws:ResourceTag/aws:backup:source-resource": "false"
}
}
},
{
"Sid": "BackupVaultPermissions",
"Effect": "Allow",
"Action": [
"backup:DescribeBackupVault",
"backup:CopyIntoBackupVault"
],
"Resource": "arn:aws:backup:*:*:backup-vault:*"
},
{
"Sid": "BackupVaultCopyPermissions",
"Effect": "Allow",
"Action": [
"backup:CopyFromBackupVault"
],
"Resource": "*"
},
{
"Sid": "EFSPermissions",
"Effect": "Allow",
"Action": [
"elasticfilesystem:Backup",
"elasticfilesystem:DescribeTags"
],
"Resource": "arn:aws:elasticfilesystem:*:*:file-system/*"
},
{
"Sid": "EBSResourcePermissions",
"Effect": "Allow",
"Action": [
"ec2:CreateSnapshot",
"ec2:DeleteSnapshot",
"ec2:DescribeVolumes",
"ec2:DescribeSnapshots"
],
"Resource": [
"arn:aws:ec2:*::snapshot/*",
"arn:aws:ec2:*:*:volume/*"
]
},
{
"Sid": "KMSDynamoDBPermissions",
"Effect": "Allow",
"Action": [
"kms:Decrypt",
"kms:GenerateDataKey"
],
"Resource": "*",
"Condition": {
"StringLike": {
"kms:ViaService": [
"dynamodb.*.amazonaws.com"
]
}
}
},
{
"Sid": "KMSPermissions",
"Effect": "Allow",
"Action": "kms:DescribeKey",
"Resource": "*"
},
{
"Sid": "KMSCreateGrantPermissions",
"Effect": "Allow",
"Action": "kms:CreateGrant",
"Resource": "*",
"Condition": {
"Bool": {
"kms:GrantIsForAWSResource": "true"
}
}
},
{
"Sid": "KMSDataKeyEC2Permissions",
"Effect": "Allow",
"Action": [
"kms:GenerateDataKeyWithoutPlaintext"
],
"Resource": "arn:aws:kms:*:*:key/*",
"Condition": {
"StringLike": {
"kms:ViaService": [
"ec2.*.amazonaws.com"
]
}
}
},
{
"Sid": "GetResourcesPermissions",
"Effect": "Allow",
"Action": [
"tag:GetResources"
],
"Resource": "*"
},
{
"Sid": "SSMPermissions",
"Effect": "Allow",
"Action": [
"ssm:CancelCommand",
"ssm:GetCommandInvocation"
],
"Resource": "*"
},
{
"Sid": "SSMSendPermissions",
"Effect": "Allow",
"Action": "ssm:SendCommand",
"Resource": [
"arn:aws:ssm:*:*:document/AWSEC2-CreateVssSnapshot",
"arn:aws:ec2:*:*:instance/*"
]
},
{
"Sid": "FsxBackupPermissions",
"Effect": "Allow",
"Action": "fsx:DescribeBackups",
"Resource": "arn:aws:fsx:*:*:backup/*"
},
{
"Sid": "FsxCreateBackupPermissions",
"Effect": "Allow",
"Action": "fsx:CreateBackup",
"Resource": [
"arn:aws:fsx:*:*:file-system/*",
"arn:aws:fsx:*:*:backup/*",
"arn:aws:fsx:*:*:volume/*"
]
},
{
"Sid": "FsxPermissions",
"Effect": "Allow",
"Action": "fsx:DescribeFileSystems",
"Resource": "arn:aws:fsx:*:*:file-system/*"
},
{
"Sid": "FsxVolumePermissions",
"Effect": "Allow",
"Action": "fsx:DescribeVolumes",
"Resource": "arn:aws:fsx:*:*:volume/*"
},
{
"Sid": "FsxListTagsPermissions",
"Effect": "Allow",
"Action": "fsx:ListTagsForResource",
"Resource": [
"arn:aws:fsx:*:*:file-system/*",
"arn:aws:fsx:*:*:volume/*"
]
},
{
"Sid": "FsxDeletePermissions",
"Effect": "Allow",
"Action": "fsx:DeleteBackup",
"Resource": "arn:aws:fsx:*:*:backup/*"
},
{
"Sid": "FsxResourcePermissions",
"Effect": "Allow",
"Action": [
"fsx:ListTagsForResource",
"fsx:ManageBackupPrincipalAssociations",
"fsx:CopyBackup",
"fsx:TagResource"
],
"Resource": "arn:aws:fsx:*:*:backup/*"
},
{
"Sid": "DynamodbBackupPermissions",
"Effect": "Allow",
"Action": [
"dynamodb:StartAwsBackupJob",
"dynamodb:ListTagsOfResource"
],
"Resource": "arn:aws:dynamodb:*:*:table/*"
},
{
"Sid": "BackupGatewayBackupPermissions",
"Effect": "Allow",
"Action": [
"backup-gateway:Backup",
"backup-gateway:ListTagsForResource"
],
"Resource": "arn:aws:backup-gateway:*:*:vm/*"
},
{
"Sid": "CloudformationStackPermissions",
"Effect": "Allow",
"Action": [
"cloudformation:ListStacks",
"cloudformation:GetTemplate",
"cloudformation:DescribeStacks",
"cloudformation:ListStackResources"
],
"Resource": "arn:aws:cloudformation:*:*:stack/*/*"
},
{
"Sid": "RedshiftCreatePermissions",
"Effect": "Allow",
"Action": [
"redshift:CreateClusterSnapshot",
"redshift:DescribeClusterSnapshots",
"redshift:DescribeTags"
],
"Resource": [
"arn:aws:redshift:*:*:snapshot:*/*",
"arn:aws:redshift:*:*:cluster:*"
]
},
{
"Sid": "RedshiftSnapshotPermissions",
"Effect": "Allow",
"Action": [
"redshift:DeleteClusterSnapshot"
],
"Resource": [
"arn:aws:redshift:*:*:snapshot:*/*"
]
},
{
"Sid": "RedshiftPermissions",
"Effect": "Allow",
"Action": [
"redshift:DescribeClusters"
],
"Resource": [
"arn:aws:redshift:*:*:cluster:*"
]
},
{
"Sid": "RedshiftResourcePermissions",
"Effect": "Allow",
"Action": [
"redshift:CreateTags"
],
"Resource": [
"arn:aws:redshift:*:*:snapshot:*/*"
]
},
{
"Sid": "TimestreamResourcePermissions",
"Effect": "Allow",
"Action": [
"timestream:StartAwsBackupJob",
"timestream:GetAwsBackupStatus",
"timestream:ListTables",
"timestream:ListDatabases",
"timestream:ListTagsForResource",
"timestream:DescribeTable",
"timestream:DescribeDatabase"
],
"Resource": [
"arn:aws:timestream:*:*:database/*"
]
},
{
"Sid": "TimestreamEndpointPermissions",
"Effect": "Allow",
"Action": [
"timestream:DescribeEndpoints"
],
"Resource": "*"
},
{
"Sid": "SSMSAPPermissions",
"Effect": "Allow",
"Action": [
"ssm-sap:GetOperation",
"ssm-sap:ListDatabases"
],
"Resource": "*"
},
{
"Sid": "SSMSAPResourcePermissions",
"Effect": "Allow",
"Action": [
"ssm-sap:BackupDatabase",
"ssm-sap:UpdateHanaBackupSettings",
"ssm-sap:GetDatabase",
"ssm-sap:ListTagsForResource"
],
"Resource": "arn:aws:ssm-sap:*:*:*"
},
{
"Sid": "RecoveryPointTaggingPermissions",
"Effect": "Allow",
"Action": [
"backup:TagResource"
],
"Resource": "arn:aws:backup:*:*:recovery-point:*",
"Condition": {
"StringEquals": {
"aws:PrincipalAccount": "${aws:ResourceAccount}"
}
}
}
]
}
AWSBackupServiceRolePolicyForRestores
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "DynamoDBPermissions",
"Effect": "Allow",
"Action": [
"dynamodb:Scan",
"dynamodb:Query",
"dynamodb:UpdateItem",
"dynamodb:PutItem",
"dynamodb:GetItem",
"dynamodb:DeleteItem",
"dynamodb:BatchWriteItem",
"dynamodb:DescribeTable"
],
"Resource": "arn:aws:dynamodb:*:*:table/*"
},
{
"Sid": "DynamoDBBackupResourcePermissions",
"Effect": "Allow",
"Action": [
"dynamodb:RestoreTableFromBackup"
],
"Resource": "arn:aws:dynamodb:*:*:table/*/backup/*"
},
{
"Sid": "EBSPermissions",
"Effect": "Allow",
"Action": [
"ec2:CreateVolume",
"ec2:DeleteVolume"
],
"Resource": [
"arn:aws:ec2:*::snapshot/*",
"arn:aws:ec2:*:*:volume/*"
]
},
{
"Sid": "EC2DescribePermissions",
"Effect": "Allow",
"Action": [
"ec2:DescribeImages",
"ec2:DescribeInstances",
"ec2:DescribeSnapshots",
"ec2:DescribeVolumes",
"ec2:DescribeAccountAttributes",
"ec2:DescribeAddresses",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSubnets",
"ec2:DescribeVpcs",
"ec2:DescribeInternetGateways",
"ec2:DescribeSnapshotTierStatus"
],
"Resource": "*"
},
{
"Sid": "StorageGatewayVolumePermissions",
"Effect": "Allow",
"Action": [
"storagegateway:DeleteVolume",
"storagegateway:DescribeCachediSCSIVolumes",
"storagegateway:DescribeStorediSCSIVolumes",
"storagegateway:AddTagsToResource"
],
"Resource": "arn:aws:storagegateway:*:*:gateway/*/volume/*"
},
{
"Sid": "StorageGatewayGatewayPermissions",
"Effect": "Allow",
"Action": [
"storagegateway:DescribeGatewayInformation",
"storagegateway:CreateStorediSCSIVolume",
"storagegateway:CreateCachediSCSIVolume"
],
"Resource": "arn:aws:storagegateway:*:*:gateway/*"
},
{
"Sid": "StorageGatewayListPermissions",
"Effect": "Allow",
"Action": [
"storagegateway:ListVolumes"
],
"Resource": "arn:aws:storagegateway:*:*:*"
},
{
"Sid": "RDSPermissions",
"Effect": "Allow",
"Action": [
"rds:DescribeDBInstances",
"rds:DescribeDBSnapshots",
"rds:ListTagsForResource",
"rds:RestoreDBInstanceFromDBSnapshot",
"rds:DeleteDBInstance",
"rds:AddTagsToResource",
"rds:DescribeDBClusters",
"rds:RestoreDBClusterFromSnapshot",
"rds:DeleteDBCluster",
"rds:RestoreDBInstanceToPointInTime",
"rds:DescribeDBClusterSnapshots",
"rds:RestoreDBClusterToPointInTime",
"rds:CreateTenantDatabase",
"rds:DeleteTenantDatabase"
],
"Resource": "*"
},
{
"Sid": "EFSPermissions",
"Effect": "Allow",
"Action": [
"elasticfilesystem:Restore",
"elasticfilesystem:CreateFilesystem",
"elasticfilesystem:DescribeFilesystems",
"elasticfilesystem:DeleteFilesystem",
"elasticfilesystem:TagResource"
],
"Resource": "arn:aws:elasticfilesystem:*:*:file-system/*"
},
{
"Sid": "KMSDescribePermissions",
"Effect": "Allow",
"Action": "kms:DescribeKey",
"Resource": "*"
},
{
"Sid": "KMSPermissions",
"Effect": "Allow",
"Action": [
"kms:Decrypt",
"kms:Encrypt",
"kms:GenerateDataKey",
"kms:ReEncryptTo",
"kms:ReEncryptFrom",
"kms:GenerateDataKeyWithoutPlaintext"
],
"Resource": "*",
"Condition": {
"StringLike": {
"kms:ViaService": [
"dynamodb.*.amazonaws.com",
"ec2.*.amazonaws.com",
"elasticfilesystem.*.amazonaws.com",
"rds.*.amazonaws.com",
"redshift.*.amazonaws.com"
]
}
}
},
{
"Sid": "KMSCreateGrantPermissions",
"Effect": "Allow",
"Action": "kms:CreateGrant",
"Resource": "*",
"Condition": {
"Bool": {
"kms:GrantIsForAWSResource": "true"
}
}
},
{
"Sid": "EBSSnapshotBlockPermissions",
"Effect": "Allow",
"Action": [
"ebs:CompleteSnapshot",
"ebs:StartSnapshot",
"ebs:PutSnapshotBlock"
],
"Resource": "arn:aws:ec2:*::snapshot/*"
},
{
"Sid": "RDSResourcePermissions",
"Effect": "Allow",
"Action": [
"rds:CreateDBInstance"
],
"Resource": "arn:aws:rds:*:*:db:*"
},
{
"Sid": "EC2DeleteAndRestorePermissions",
"Effect": "Allow",
"Action": [
"ec2:DeleteSnapshot",
"ec2:DeleteTags",
"ec2:RestoreSnapshotTier"
],
"Resource": "arn:aws:ec2:*::snapshot/*",
"Condition": {
"Null": {
"aws:ResourceTag/aws:backup:source-resource": "false"
}
}
},
{
"Sid": "EC2CreateTagsScopedPermissions",
"Effect": "Allow",
"Action": "ec2:CreateTags",
"Resource": [
"arn:aws:ec2:*::snapshot/*",
"arn:aws:ec2:*:*:instance/*"
],
"Condition": {
"ForAllValues:StringEquals": {
"aws:TagKeys": [
"aws:backup:source-resource"
]
}
}
},
{
"Sid": "EC2RunInstancesPermissions",
"Effect": "Allow",
"Action": [
"ec2:RunInstances"
],
"Resource": "*"
},
{
"Sid": "EC2TerminateInstancesPermissions",
"Effect": "Allow",
"Action": [
"ec2:TerminateInstances"
],
"Resource": "arn:aws:ec2:*:*:instance/*"
},
{
"Sid": "EC2CreateTagsPermissions",
"Effect": "Allow",
"Action": [
"ec2:CreateTags"
],
"Resource": [
"arn:aws:ec2:*:*:instance/*",
"arn:aws:ec2:*:*:volume/*"
],
"Condition": {
"ForAnyValue:StringLike": {
"ec2:CreateAction": [
"RunInstances",
"CreateVolume"
]
}
}
},
{
"Sid": "FsxPermissions",
"Effect": "Allow",
"Action": [
"fsx:CreateFileSystemFromBackup"
],
"Resource": [
"arn:aws:fsx:*:*:file-system/*",
"arn:aws:fsx:*:*:backup/*"
]
},
{
"Sid": "FsxTagPermissions",
"Effect": "Allow",
"Action": [
"fsx:DescribeFileSystems",
"fsx:TagResource"
],
"Resource": "arn:aws:fsx:*:*:file-system/*"
},
{
"Sid": "FsxBackupPermissions",
"Effect": "Allow",
"Action": "fsx:DescribeBackups",
"Resource": "arn:aws:fsx:*:*:backup/*"
},
{
"Sid": "FsxDeletePermissions",
"Effect": "Allow",
"Action": [
"fsx:DeleteFileSystem",
"fsx:UntagResource"
],
"Resource": "arn:aws:fsx:*:*:file-system/*",
"Condition": {
"Null": {
"aws:ResourceTag/aws:backup:source-resource": "false"
}
}
},
{
"Sid": "FsxDescribePermissions",
"Effect": "Allow",
"Action": [
"fsx:DescribeVolumes"
],
"Resource": "arn:aws:fsx:*:*:volume/*"
},
{
"Sid": "FsxVolumeTagPermissions",
"Effect": "Allow",
"Action": [
"fsx:CreateVolumeFromBackup",
"fsx:TagResource"
],
"Resource": [
"arn:aws:fsx:*:*:volume/*"
],
"Condition": {
"ForAllValues:StringEquals": {
"aws:TagKeys": [
"aws:backup:source-resource"
]
}
}
},
{
"Sid": "FsxBackupTagPermissions",
"Effect": "Allow",
"Action": [
"fsx:CreateVolumeFromBackup",
"fsx:TagResource"
],
"Resource": [
"arn:aws:fsx:*:*:storage-virtual-machine/*",
"arn:aws:fsx:*:*:backup/*",
"arn:aws:fsx:*:*:volume/*"
]
},
{
"Sid": "FsxVolumePermissions",
"Effect": "Allow",
"Action": [
"fsx:DeleteVolume",
"fsx:UntagResource"
],
"Resource": "arn:aws:fsx:*:*:volume/*",
"Condition": {
"Null": {
"aws:ResourceTag/aws:backup:source-resource": "false"
}
}
},
{
"Sid": "DSPermissions",
"Effect": "Allow",
"Action": "ds:DescribeDirectories",
"Resource": "*"
},
{
"Sid": "DynamoDBRestorePermissions",
"Effect": "Allow",
"Action": [
"dynamodb:RestoreTableFromAwsBackup"
],
"Resource": "arn:aws:dynamodb:*:*:table/*"
},
{
"Sid": "GatewayRestorePermissions",
"Effect": "Allow",
"Action": [
"backup-gateway:Restore"
],
"Resource": "arn:aws:backup-gateway:*:*:hypervisor/*"
},
{
"Sid": "CloudformationChangeSetPermissions",
"Effect": "Allow",
"Action": [
"cloudformation:CreateChangeSet",
"cloudformation:DescribeChangeSet",
"cloudformation:TagResource"
],
"Resource": "arn:aws:cloudformation:*:*:*/*/*"
},
{
"Sid": "RedshiftClusterSnapshotPermissions",
"Effect": "Allow",
"Action": [
"redshift:RestoreFromClusterSnapshot",
"redshift:RestoreTableFromClusterSnapshot"
],
"Resource": [
"arn:aws:redshift:*:*:snapshot:*/*",
"arn:aws:redshift:*:*:cluster:*"
]
},
{
"Sid": "RedshiftClusterPermissions",
"Effect": "Allow",
"Action": [
"redshift:DescribeClusters"
],
"Resource": [
"arn:aws:redshift:*:*:cluster:*"
]
},
{
"Sid": "RedshiftTablePermissions",
"Effect": "Allow",
"Action": [
"redshift:DescribeTableRestoreStatus"
],
"Resource": "*"
},
{
"Sid": "TimestreamResourcePermissions",
"Effect": "Allow",
"Action": [
"timestream:StartAwsRestoreJob",
"timestream:GetAwsRestoreStatus",
"timestream:ListTables",
"timestream:ListTagsForResource",
"timestream:ListDatabases",
"timestream:DescribeTable",
"timestream:DescribeDatabase"
],
"Resource": [
"arn:aws:timestream:*:*:database/*"
]
},
{
"Sid": "TimestreamEndpointPermissions",
"Effect": "Allow",
"Action": [
"timestream:DescribeEndpoints"
],
"Resource": [
"*"
]
}
]
}
どちらのポリシーもS3バケットに対する操作権限が付与されていません。
つまり、AWS Backupが作成するデフォルトロールではS3バケットのバックアップは取得できないようです。
対策
ドキュメントに記載の通り、AWSBackupServiceRolePolicyForS3BackupとAWSBackupServiceRolePolicyForS3Restoreをロールに追加します。
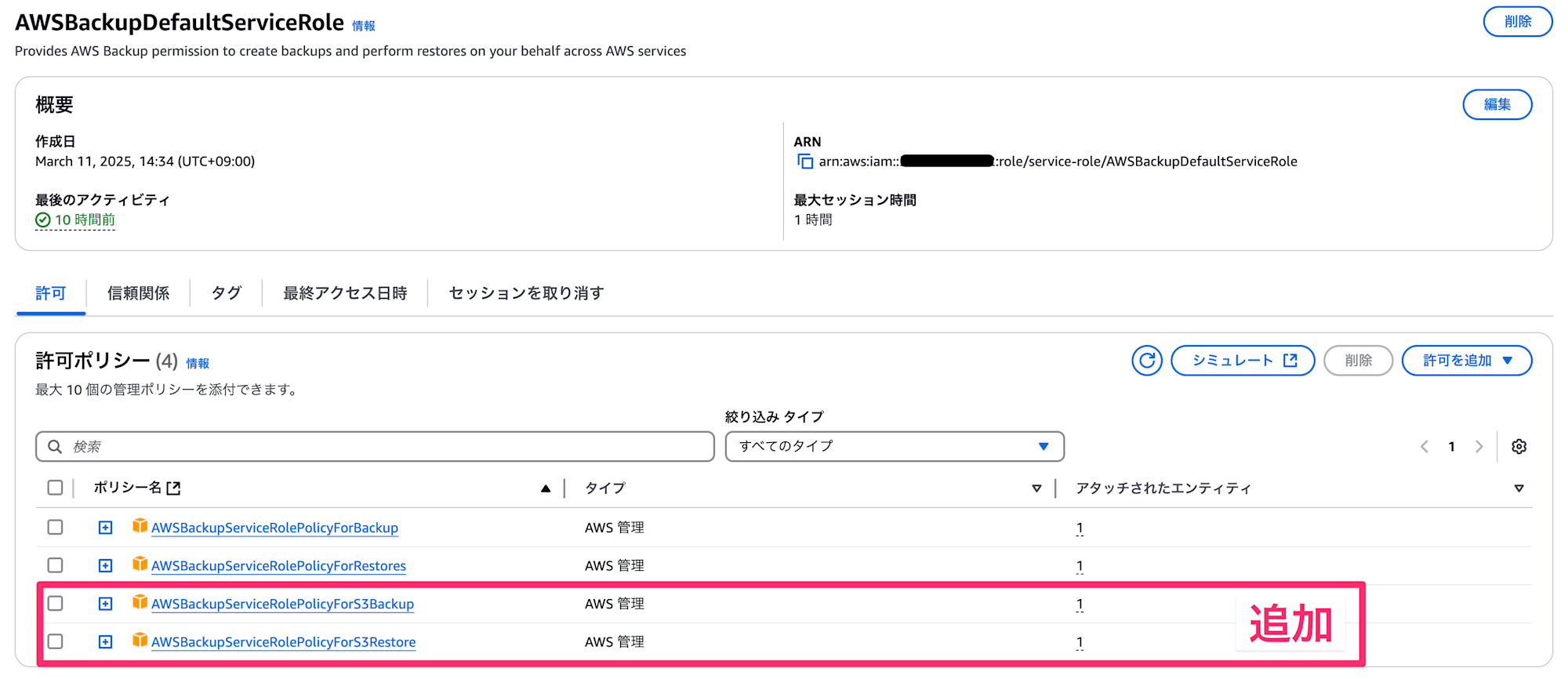
次のバックアップタイミングまで待ち、バックアップが成功することを確認します。
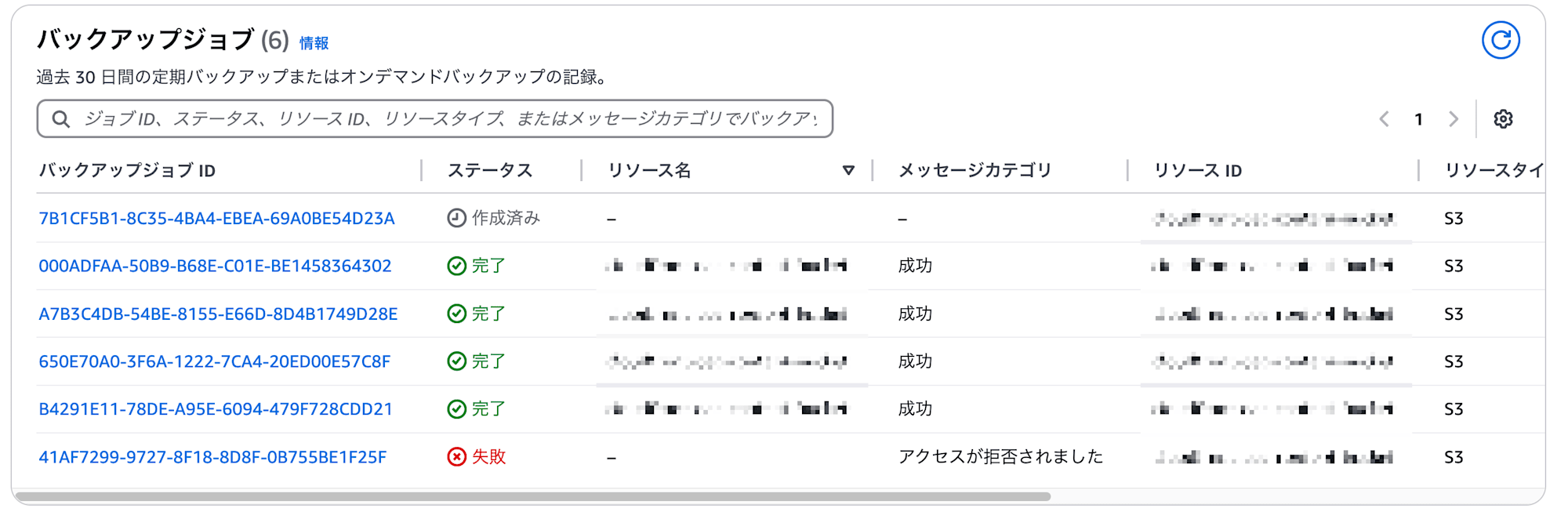
問題なくバックアップが取得できていることが確認できました。
まとめ
AWS BackupでS3のバックアップを取得する際は、AWS Backupが作成するデフォルトロール以外に特定のポリシーが必要ということがわかりました。
ドキュメントを見れば分かるのですが、初見だと、え?なんで自動作成されたロールなのに権限エラーになるの?と戸惑うかもしれません。
AWS BackupではS3以外にEC2やAurora, DynamoDBなど、複数のリソースタイプをサポートしています。
AWSBackupDefaultServiceRoleの権限を確認すると、ほとんどのリソースのbackupを取得する権限はアタッチされているようでした。
AWS Backupが作成するデフォルトロールで権限エラーが出る場合は、「AWS Backup <リソース名>」などで検索して、前提条件として必要な権限がないか確認してみましょう。








