
Recap of AWS Community Day DACH 2025: Implementing Compliance in AWS with Terraform
Session Information

Presenter: Anton Babenko
Implementing Compliance in AWS with Terraform: Practical Steps That Work
Implementing compliance doesn't have to be treated like voodoo magic (though some vendors want you to think it is). As the creator of the popular open-source Terraform AWS modules, which have been provisioned several billion times worldwide, and the newer compliance modules.tf project, I've spent years helping teams make their AWS infrastructure secure and compliant without burning out.
In this talk, I'll walk through practical, hands-on ways to approach compliance in modern cloud environments using Terraform. I'll show you how to evaluate your compliance readiness for frameworks like SOC 2, ISO 27001, GDPR, and HIPAA using a mix of cloud-native services and open-source tools, such as Prowler, SteamPipe, and Checkov. Then I'll demonstrate how to write Terraform code to meet those required controls, implement compliance-as-code as part of your CI/CD pipelines, and prevent compliance drift over time, so your infrastructure stays secure as it evolves.
This talk is packed with real-world examples, so if you're responsible for building or maintaining infrastructure and want to get compliance right from the start (or finally address what's already there), this session is for you.
Overview
This session was presented by Anton Babenko, the creator of popular open-source Terraform AWS modules and the compliance.tf project.
The talk focused on practical steps to implement compliance in AWS using Terraform, which is a critical aspect of modern cloud infrastructure management.
Why Compliance Matters

Modern cloud infrastructure requires compliance with various frameworks including SOC 2, ISO 27001, GDPR, and HIPAA.
However, compliance initiatives often fail because they're treated as afterthoughts.
Issues typically surface only after incidents occur, leading to reactive rather than proactive security measures.
Compliance process

Using Infrastructure as Code (IaC) creates automatic evidence trails for compliance audits.
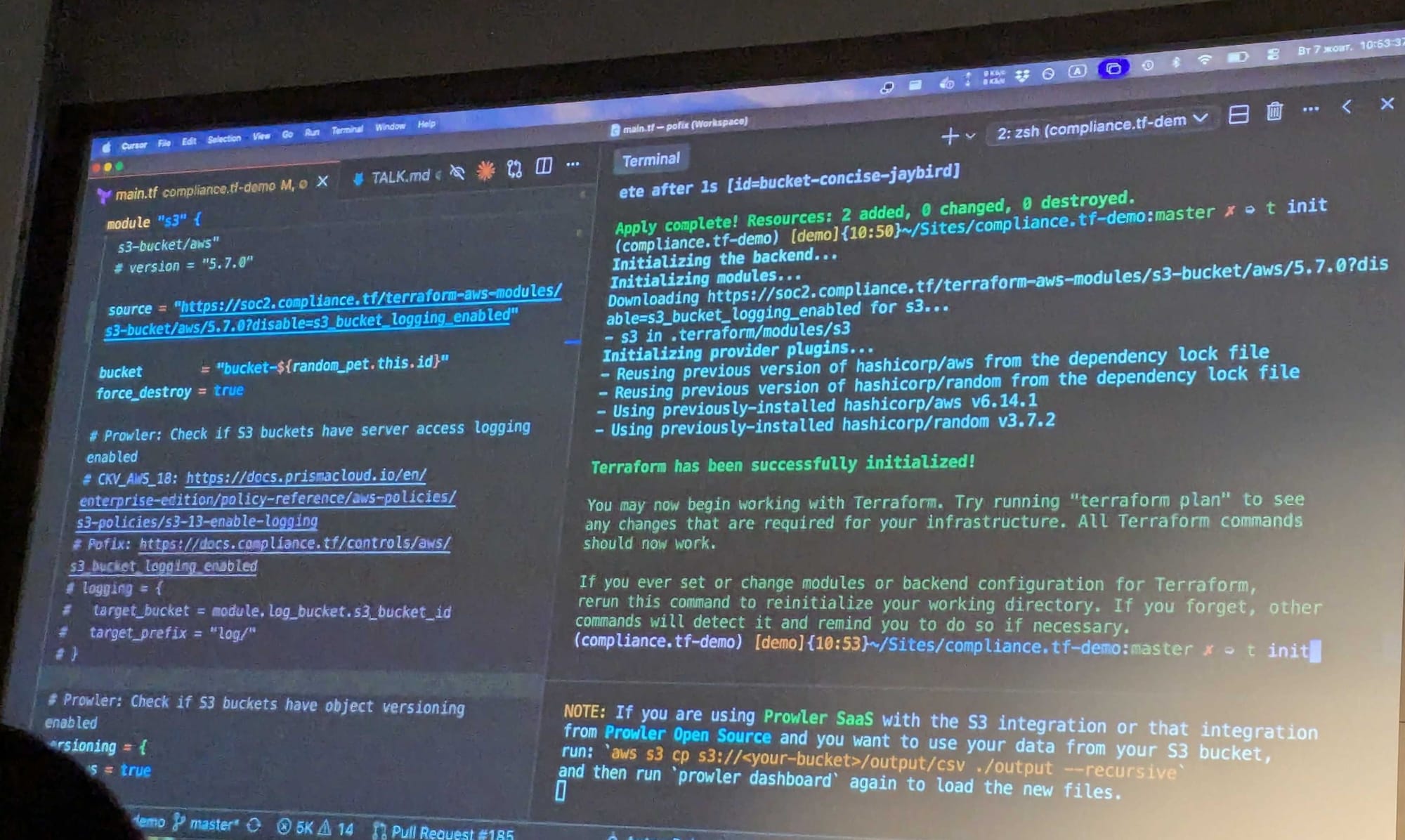
Anton demonstrated concrete approaches to implement compliance controls directly in Terraform code, making compliance verification automated and continuous.
In addition, Anton demonstrated how compliance.tf modules can be integrated into Terraform code to enforce compliance standards automatically.
Key Highlights
Steps to Implement Compliance
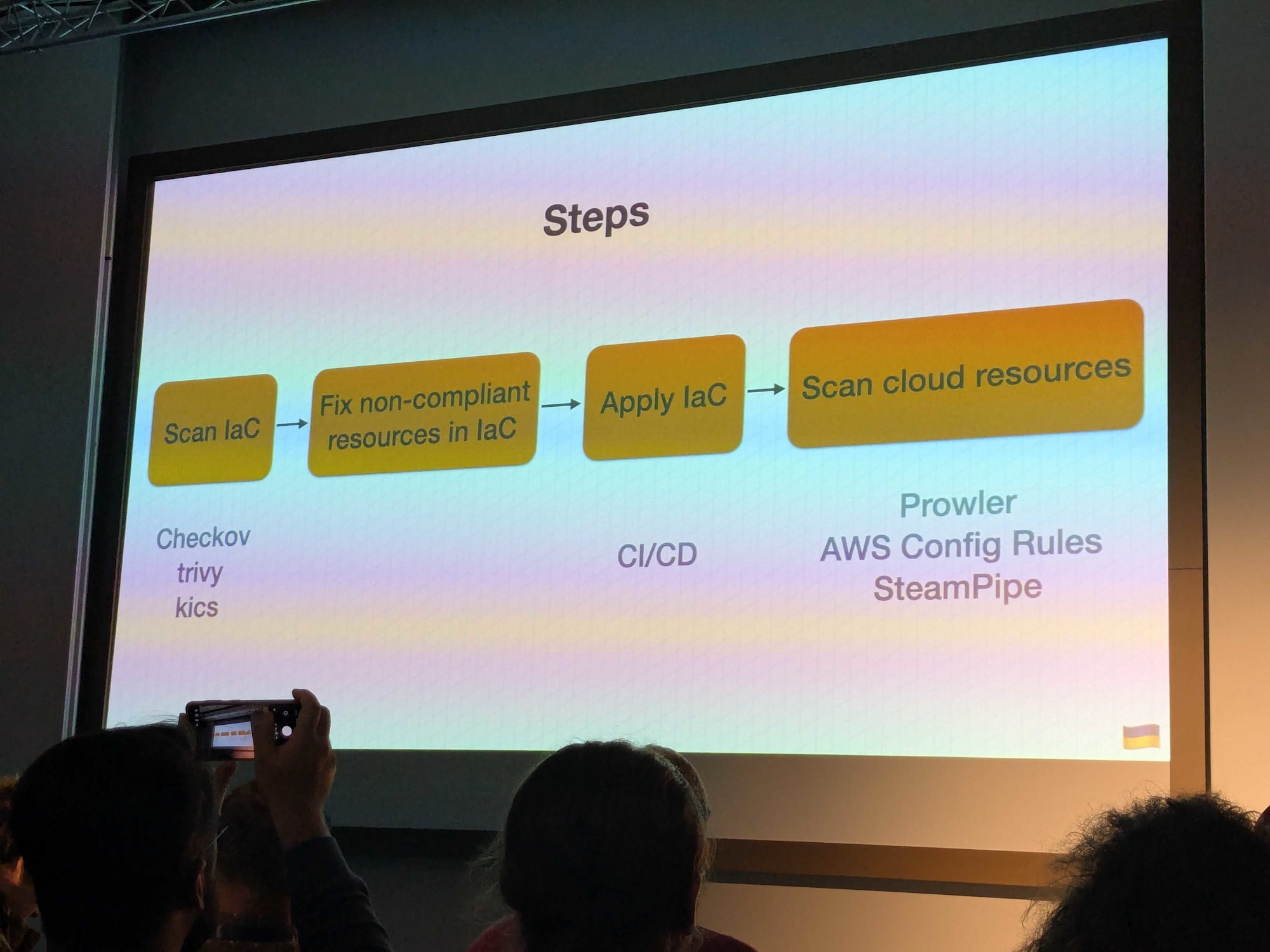

Anton introduced a powerful toolkit for compliance implementation that works effectively together:
- Checkov: Static code analysis for security checks in your IaC code
- Prowler: Validates AWS security best practices against your live AWS accounts
- Steampipe: Enables querying cloud resources using SQL for compliance reporting
- pre-commit-terraform: Maintains Terraform code quality through automated checks
Use Checkov to catch basic vulnerabilities in your code, then employ Prowler and Steampipe to ensure your account state remains compliant.
In addition, Anton highlighted compliance.tf as a curated set of Terraform modules designed with compliance requirements built in.
Drift Prevention

Preventing configuration drift is crucial for maintaining compliance.
Anti-Patterns to Avoid

- Recommended reading:
- The Snowflakes as Code anti pattern http://infrastructure-as-code.com/posts/snowflakes-as-code.html
- Terraform Best Practices https://www.terraform-best-practices.com/
What's Next
After this session, I quickly installed Checkov in our GitHub Actions workflows on our projects. It was very easy to set up and I highly recommend it.
I'm now investigating practical usage of Prowler in our current projects.
Next, I'm going to explore compliance.tf modules to see how they can be integrated into our Terraform codebase to enhance compliance.
There are free trials available!









