
Terraform MCP ServerをAWS Marketplaceでサブスクライブして、Amazon Bedrock AgentCoreを使ってセットアップしてみた
先日、AWS MarketplaceにTerraform MCP Serverが追加されました。
Build secure, AI-driven workflows with Terraform and Vault MCP servers
今回はこちらをサブスクライブし、Amazon Bedrock Agent Coreを使ってセットアップしてみます。
Terraform MCP Server
Terraform MCP Serverを使うことで、AIがTerraform Registryの情報を読み取って回答を生成してくれます。
詳細は以下をご確認ください。
Amazon Bedrock Agent Coreとは
2025年7月(プレビュー)に発表されたサービスで、AIエージェントを構築して公開するために必要な様々な機能が搭載されています。
やってみた
AWS MarketplaceでTerraform MCP Serverをサブスクライブ
AWS MarketplaceでTerraform MCP Serverを検索し選択します。
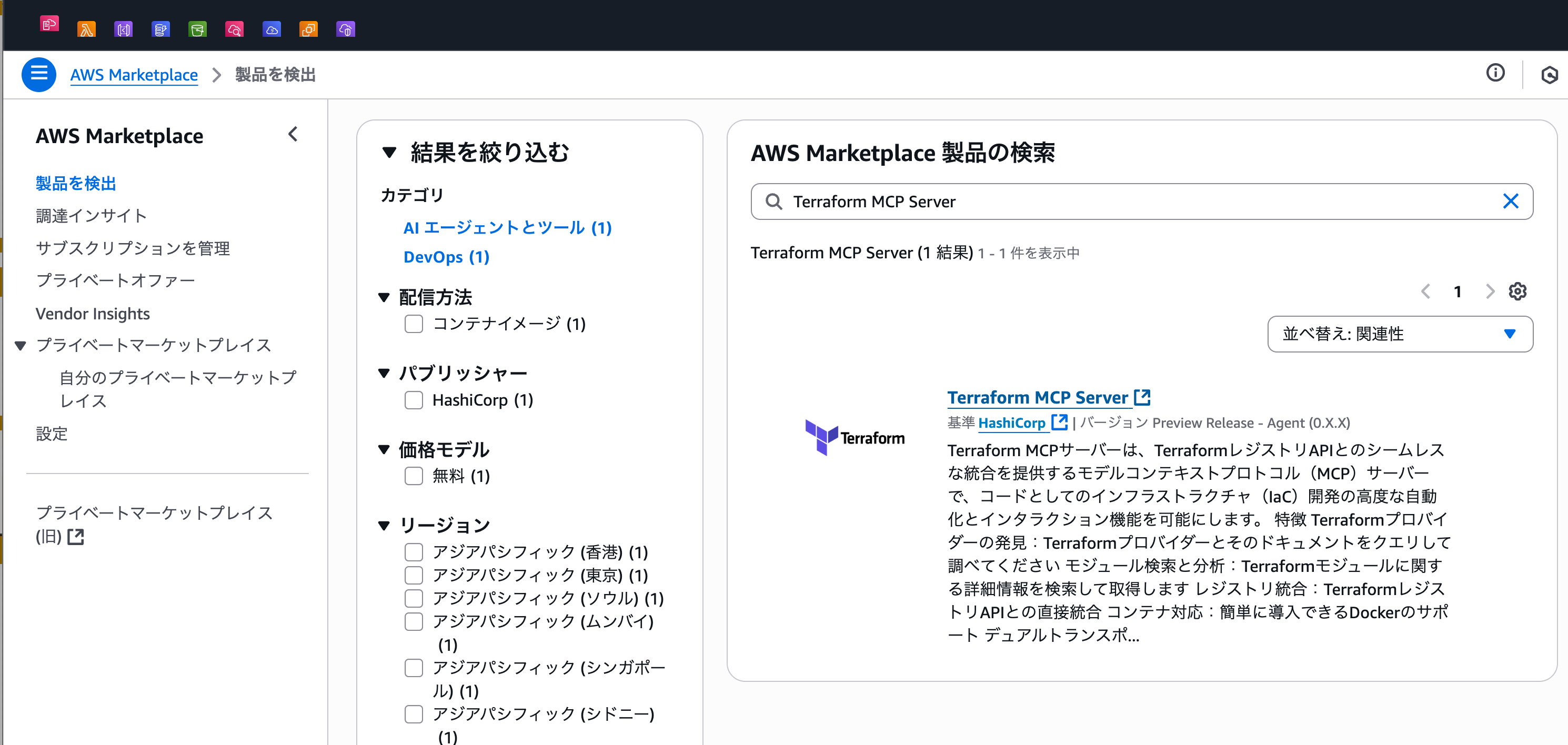
以下のリンクからもアクセスできます。
AWS Marketplace: Terraform MCP Server
こちらの製品は無料でサブスクライブできます。
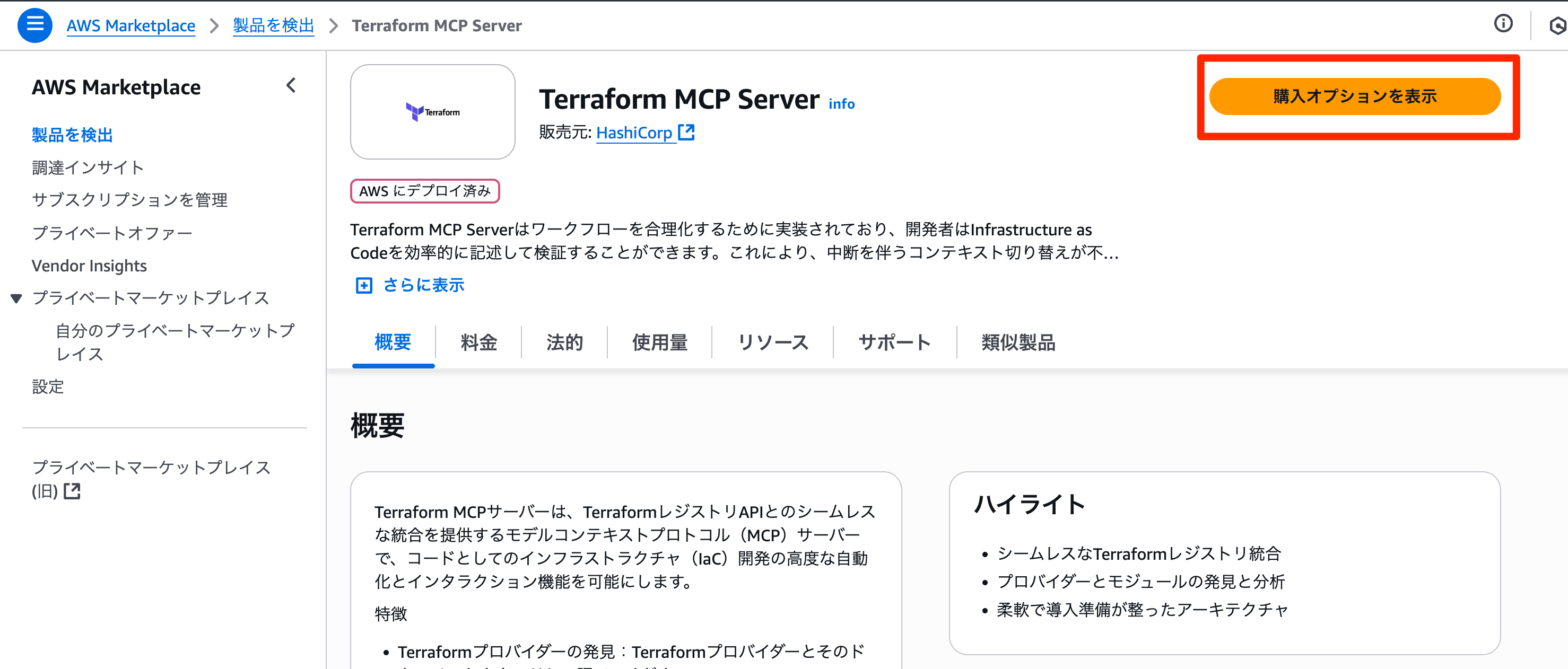
購入オプションを表示からサブスクライブ画面に進んでサブスクライブします。
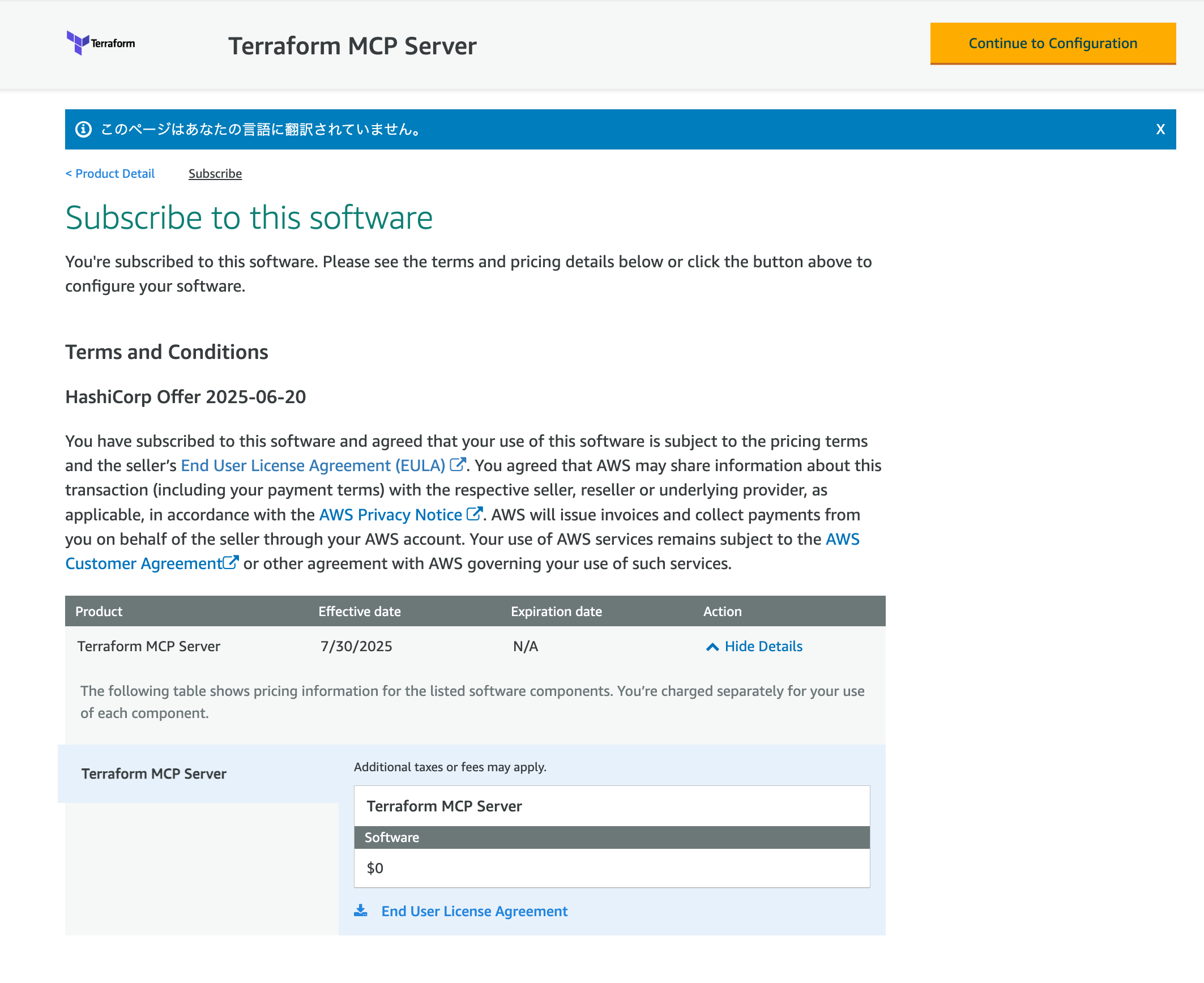
Continue to Configurationから設定に進みます。
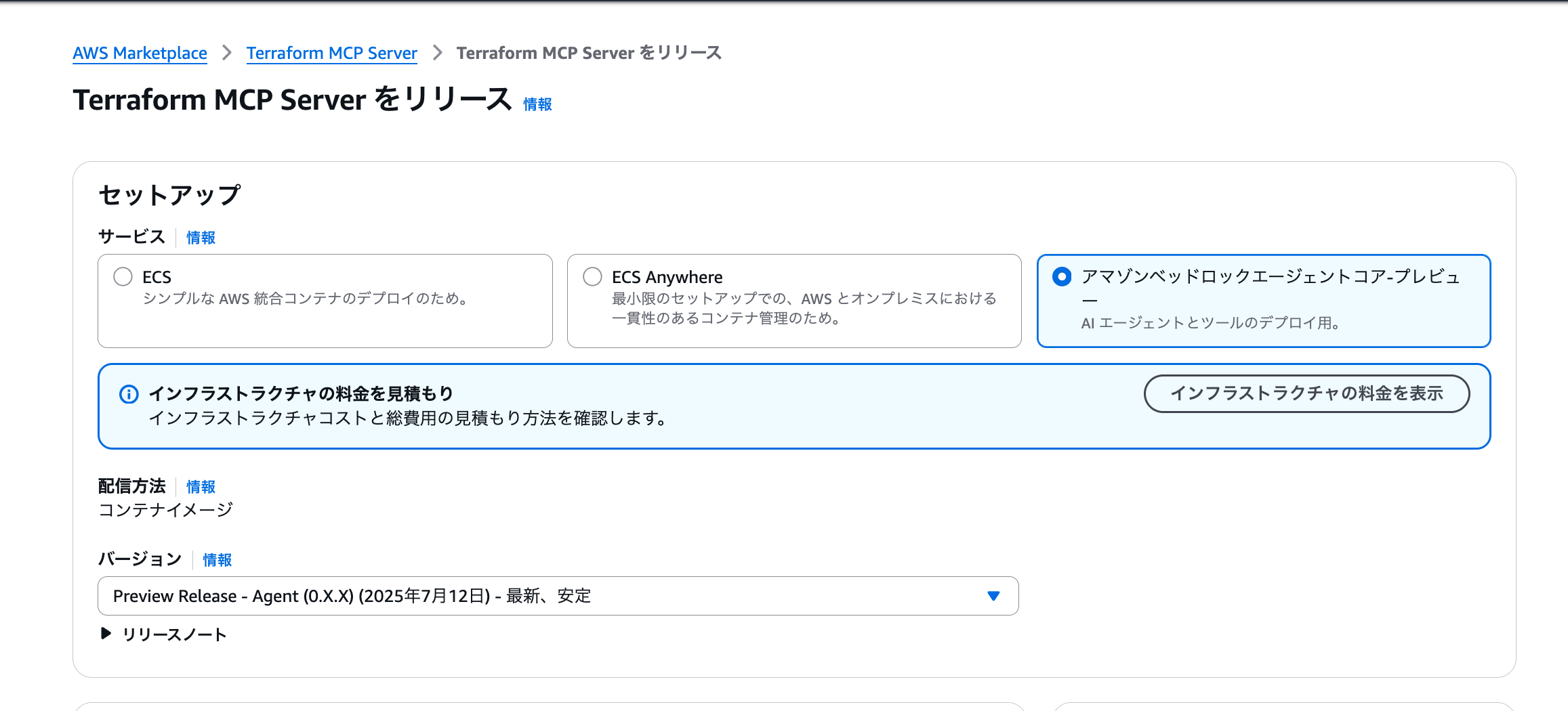
以下のようにデプロイのガイドが表示されます。
ガイドに従ってAmazon Bedrock Agent Coreにデプロイしていきます。
Agent Runtime用のIAM Roleを作成
Agent Runtime用のIAM Roleが必要なため作成します。
IAM Role名は、AmazonBedrockAgentCoreRuntimeServiceRole-TerraformMCPServerとしました。
以下の内容でIAM Roleを作成します。<accountId> <region>部分は環境に合わせて修正してください。
<Terraform MCP Server ECR Repo ARN>はAWS Marketplaceでサブスクライブ後のガイドにAmazon ECRイメージURLが表示されるので、ARNに変換して設定します。
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "ECRImageAccess",
"Effect": "Allow",
"Action": [
"ecr:BatchGetImage",
"ecr:GetDownloadUrlForLayer"
],
"Resource": [
"<Terraform MCP Server ECR Repo ARN>"
]
},
{
"Effect": "Allow",
"Action": [
"logs:DescribeLogStreams",
"logs:CreateLogGroup"
],
"Resource": [
"arn:aws:logs:<region>:<accountId>:log-group:/aws/bedrock-agentcore/runtimes/*"
]
},
{
"Effect": "Allow",
"Action": [
"logs:DescribeLogGroups"
],
"Resource": [
"arn:aws:logs:<region>:<accountId>:log-group:*"
]
},
{
"Effect": "Allow",
"Action": [
"logs:CreateLogStream",
"logs:PutLogEvents"
],
"Resource": [
"arn:aws:logs:<region>:<accountId>:log-group:/aws/bedrock-agentcore/runtimes/*:log-stream:*"
]
},
{
"Sid": "ECRTokenAccess",
"Effect": "Allow",
"Action": [
"ecr:GetAuthorizationToken"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"xray:PutTraceSegments",
"xray:PutTelemetryRecords",
"xray:GetSamplingRules",
"xray:GetSamplingTargets"
],
"Resource": [ "*" ]
},
{
"Effect": "Allow",
"Resource": "*",
"Action": "cloudwatch:PutMetricData",
"Condition": {
"StringEquals": {
"cloudwatch:namespace": "bedrock-agentcore"
}
}
},
{
"Sid": "GetAgentAccessToken",
"Effect": "Allow",
"Action": [
"bedrock-agentcore:GetWorkloadAccessToken",
"bedrock-agentcore:GetWorkloadAccessTokenForJWT",
"bedrock-agentcore:GetWorkloadAccessTokenForUserId"
],
"Resource": [
"arn:aws:bedrock-agentcore:<region>:<accountId>:workload-identity-directory/default",
"arn:aws:bedrock-agentcore:<region>:<accountId>:workload-identity-directory/default/workload-identity/terraform-mcp*"
]
},
{"Sid": "BedrockModelInvocation",
"Effect": "Allow",
"Action": [
"bedrock:InvokeModel",
"bedrock:InvokeModelWithResponseStream"
],
"Resource": [
"arn:aws:bedrock:*::foundation-model/*",
"arn:aws:bedrock:<region>:<accountId>:*"
]
}
]
}
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AssumeRolePolicy",
"Effect": "Allow",
"Principal": {
"Service": "bedrock-agentcore.amazonaws.com"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"aws:SourceAccount": "<accountId>"
},
"ArnLike": {
"aws:SourceArn": "arn:aws:bedrock-agentcore:<region>:<accountId>:*"
}
}
}
]
}
Permissions for AgentCore Runtime - Amazon Bedrock AgentCore
Amazon Bedrock Agent CoreにTerraform MCPをデプロイする
以下のコマンドを実行して、Agent Runtimeを作成します。
aws bedrock-agentcore-control create-agent-runtime \
--region us-east-1 \
--agent-runtime-name "terraform_mcp_server" \
--description "terraform_mcp_server" \
--agent-runtime-artifact '{
"containerConfiguration": {
"containerUri": "<Terraform MCP Server ECR Image URI>"
}
}' \
--role-arn "arn:aws:iam::<accdountId>:role/service-role/AmazonBedrockAgentCoreRuntimeDefaultServiceRole-TerraformMCPServer" \
--network-configuration '{
"networkMode": "PUBLIC"
}' \
--protocol-configuration '{
"serverProtocol": "MCP"
}' \
--environment-variables '{
"MCP_SESSION_MODE": "stateless",
"MCP_CORS_MODE": "strict",
"MCP_ALLOWED_ORIGINS": "http://127.0.0.1:8000",
"TRANSPORT_MODE": "streamable-http",
"TRANSPORT_HOST": "0.0.0.0",
"TRANSPORT_PORT": "8000"
}'
マネジメントコンソール上からもAgent Runtimeが作成されていて、StatusがReadyになっていることを確認できました。
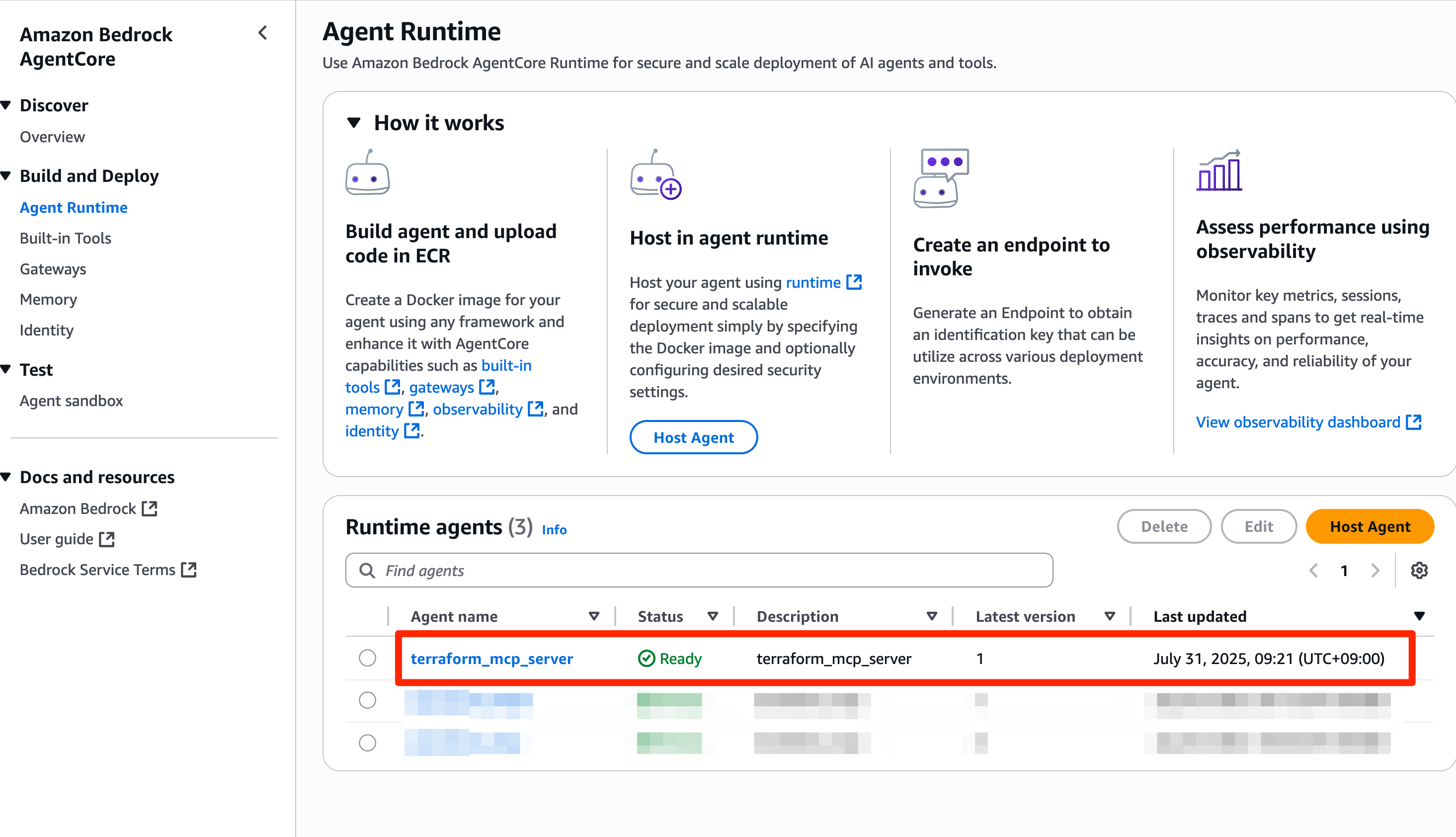
動作確認: Agent Runtimeを呼び出す
デプロイしたAgent Runtimeを呼び出してみます。
以下のコマンドを実行します。tools/listをリクエストして、terraform-mcp-serverが利用可能なツールを一覧を取得します。
export AGENT_RUNTIME_ARN=$(aws bedrock-agentcore-control list-agent-runtimes --query "agentRuntimes[?agentRuntimeName=='terraform_mcp_server'].agentRuntimeArn" --output text)
export PAYLOAD='{ "jsonrpc": "2.0", "id": 1, "method": "tools/list", "params": { "_meta": { "progressToken": 1}}}'
aws bedrock-agentcore invoke-agent-runtime \
--agent-runtime-arn $AGENT_RUNTIME_ARN \
--content-type "application/json" \
--accept "application/json, text/event-stream" \
--payload "$(echo -n "$PAYLOAD" | base64)" output.json
レスポンスはoutput.jsonに出力されます。
中身を確認するとツール一覧が出力されていました。
cat output.json
出力例
{"jsonrpc":"2.0","id":1,"result":{"tools":[{"annotations":{"title":"Fetch detailed Terraform provider documentation using a document ID","readOnlyHint":false,"destructiveHint":true,"idempotentHint":false,"openWorldHint":true},"description":"Fetches up-to-date documentation for a specific service from a Terraform provider. You must call 'resolveProviderDocID' first to obtain the exact tfprovider-compatible providerDocID required to use this tool.","inputSchema":{"properties":{"providerDocID":{"description":"Exact tfprovider-compatible providerDocID, (e.g., '8894603', '8906901') retrieved from 'resolveProviderDocID'","type":"string"}},"required":["providerDocID"],"type":"object"},"name":"getProviderDocs"},{"annotations":{"title":"Retrieve documentation for a specific Terraform module","readOnlyHint":false,"destructiveHint":true,"idempotentHint":false,"openWorldHint":true},"description":"Fetches up-to-date documentation on how to use a Terraform module. You must call 'searchModules' first to obtain the exact valid and compatible moduleID required to use this tool.","inputSchema":{"properties":{"moduleID":{"description":"Exact valid and compatible moduleID retrieved from searchModules (e.g., 'squareops/terraform-kubernetes-mongodb/mongodb/2.1.1', 'GoogleCloudPlatform/vertex-ai/google/0.2.0')","type":"string"}},"required":["moduleID"],"type":"object"},"name":"moduleDetails"},{"annotations":{"title":"Fetch detailed Terraform policy documentation using a terraformPolicyID","readOnlyHint":false,"destructiveHint":true,"idempotentHint":false,"openWorldHint":true},"description":"Fetches up-to-date documentation for a specific policy from the Terraform registry. You must call 'searchPolicies' first to obtain the exact terraformPolicyID required to use this tool.","inputSchema":{"properties":{"terraformPolicyID":{"description":"Matching terraformPolicyID retrieved from the 'searchPolicies' tool (e.g., 'policies/hashicorp/CIS-Policy-Set-for-AWS-Terraform/1.0.1')","type":"string"}},"required":["terraformPolicyID"],"type":"object"},"name":"policyDetails"},{"annotations":{"title":"Identify the most relevant provider document ID for a Terraform service","readOnlyHint":true,"destructiveHint":true,"idempotentHint":false,"openWorldHint":true},"description":"This tool retrieves a list of potential documents based on the serviceSlug and providerDataType provided. You MUST call this function before 'getProviderDocs' to obtain a valid tfprovider-compatible providerDocID. \n\t\t\tUse the most relevant single word as the search query for serviceSlug, if unsure about the serviceSlug, use the providerName for its value.\n\t\t\tWhen selecting the best match, consider: - Title similarity to the query - Category relevance Return the selected providerDocID and explain your choice. \n\t\t\tIf there are multiple good matches, mention this but proceed with the most relevant one.","inputSchema":{"properties":{"providerDataType":{"default":"resources","description":"The type of the document to retrieve, for general information use 'guides', for deploying resources use 'resources', for reading pre-deployed resources use 'data-sources', for functions use 'functions', and for overview of the provider use 'overview'","enum":["resources","data-sources","functions","guides","overview"],"type":"string"},"providerName":{"description":"The name of the Terraform provider to perform the read or deployment operation","type":"string"},"providerNamespace":{"description":"The publisher of the Terraform provider, typically the name of the company, or their GitHub organization name that created the provider","type":"string"},"providerVersion":{"description":"The version of the Terraform provider to retrieve in the format 'x.y.z', or 'latest' to get the latest version","type":"string"},"serviceSlug":{"description":"The slug of the service you want to deploy or read using the Terraform provider, prefer using a single word, use underscores for multiple words and if unsure about the serviceSlug, use the providerName for its value","type":"string"}},"required":["providerName","providerNamespace","serviceSlug"],"type":"object"},"name":"resolveProviderDocID"},{"annotations":{"title":"Search and match Terraform modules based on name and relevance","readOnlyHint":false,"destructiveHint":true,"idempotentHint":false,"openWorldHint":true},"description":"Resolves a Terraform module name to obtain a compatible moduleID for the moduleDetails tool and returns a list of matching Terraform modules. You MUST call this function before 'moduleDetails' to obtain a valid and compatible moduleID. When selecting the best match, consider: - Name similarity to the query - Description relevance - Verification status (verified) - Download counts (popularity) Return the selected moduleID and explain your choice. If there are multiple good matches, mention this but proceed with the most relevant one. If no modules were found, reattempt the search with a new moduleName query.","inputSchema":{"properties":{"currentOffset":{"default":0,"description":"Current offset for pagination","minimum":0,"type":"number"},"moduleQuery":{"description":"The query to search for Terraform modules.","type":"string"}},"required":["moduleQuery"],"type":"object"},"name":"searchModules"},{"annotations":{"title":"Search and match Terraform policies based on name and relevance","readOnlyHint":false,"destructiveHint":true,"idempotentHint":false,"openWorldHint":true},"description":"Searches for Terraform policies based on a query string. This tool returns a list of matching policies, which can be used to retrieve detailed policy information using the 'policyDetails' tool. \n\t\t\tYou MUST call this function before 'policyDetails' to obtain a valid terraformPolicyID.\n\t\t\tWhen selecting the best match, consider: - Name similarity to the query - Title relevance - Verification status (verified) - Download counts (popularity) Return the selected policyID and explain your choice. \n\t\t\tIf there are multiple good matches, mention this but proceed with the most relevant one. If no policies were found, reattempt the search with a new policyQuery.","inputSchema":{"properties":{"policyQuery":{"description":"The query to search for Terraform modules.","type":"string"}},"required":["policyQuery"],"type":"object"},"name":"searchPolicies"}]}}
おわりに
Terraform MCP ServerがAWS Marketplaceに追加されました。
これまでもGitHub上で公開されていました。
Marketplaceでも公開されたことでAWS認証済みのソリューションになり、より安全に利用ができるようになりました。
Amazon Bedrock AgentCoreは初めて使いました。
DockerイメージとIAMロールを用意するだけのシンプルな設定でリモートMCPサーバーを立ち上げることができました。
Amazon Bedrock AgentCoreはプレビューで2025/9/16まで無料で試せるので、この機会に色々試していきたいと思いました。







